A security engineer publishes the results of a 30-day honeypot that deliberately attacks a system and observes attack methods
Security engineer Sofiane Hamraoui has published the results of a 30-day trial in which a '
What You Get After Running an SSH Honeypot for 30 Days
https://blog.sofiane.cc/ssh_honeypot/
Hamraoui prepared a machine with the 6.8.0-31-generic kernel and Ubuntu 24.04 LTS x86_64 OS to use as a honeypot.
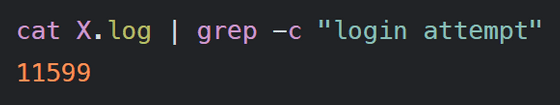
A total of 11,599 login attempts were made on the 30th, averaging 386 login attempts per day.
The ranking of usernames used when attempting to log in includes standard and commonly used names such as 'root', 'admin', 'ubuntu', and 'support'. In second place is the mysterious name '345gs5662d34', which is said to be the standard username used on the Polycom CX600 IP phone.
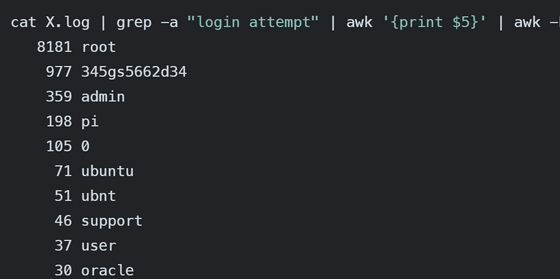
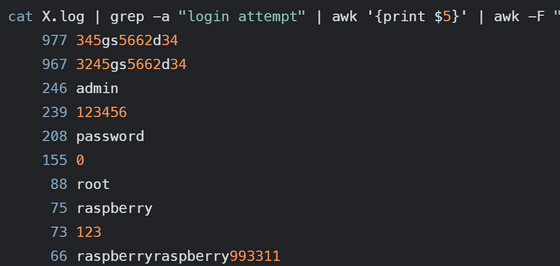
Similarly, the password ranking also showed that the standard password used by Polycom CX600 was ranked high. Other passwords that were tried included 'admin,' '123456,' and 'password,' which are obviously dangerous passwords.
The commands executed after a successful login are shown in the figure below. The most frequently executed command simply outputs 'ok', but the second and third most frequently executed commands destroy '.ssh' to disable SSH connections from anyone other than the attacker. Other commands included checking system information.
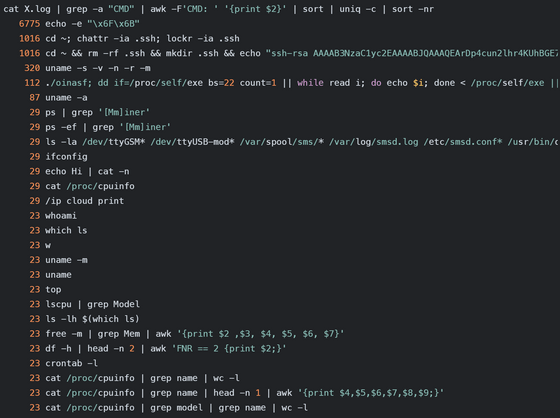
The command to execute the mysterious script './oinasf' was sent more than 100 times, suggesting the existence of some kind of strategy for intrusion. Overall, attackers are attempting to establish direct control and persistent access, so it is important to defend against these common but devastating methods.

Below is a command that attempts to install malware called 'MIPS' that targets routers and IoT devices.
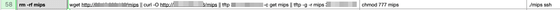
The 'Sakura.sh' file shown in the figure below is part of a malware called 'Gafgyt,' a botnet that affects IoT devices and Linux-based systems.

As seen in the example of IP phones mentioned earlier, attacks targeting routers and IoT devices are becoming more common, so it seems necessary to pay attention to devices other than PCs, which tend to have weak defenses.
Related Posts: