New side channel attack 'SGAxe' 'CrossTalk' is reported to Intel CPU, secret data can be restored

Vulnerability '
CacheOut
https://sgaxe.com/
CROSSTalk-VUSec
https://www.vusec.net/projects/crosstalk/
IPAS: Security Advisories for June 2020-Technology@Intel
https://blogs.intel.com/technology/2020/06/ipas-security-advisories-for-june-2020/#gs.8ama0y
MDS Attacks: Microarchitectural Data Sampling
https://mdsattacks.com/
Plundering of crypto keys from ultrasecure SGX sends Intel scrambling again | Ars Technica
https://arstechnica.com/information-technology/2020/06/new-exploits-plunder-crypto-keys-and-more-from-intels-ultrasecure-sgx/2/
MDS is a vulnerability that can infer data from a buffer on a microarchitecture. For example, in a CacheOut attack, it is possible to infer the contents of the private key from the public key in the RSA public key/private key pair. Several patches have been provided by Intel to mitigate the vulnerability.
Vulnerability ``MDS'' affecting almost all Intel processors since 2011 revealed-GIGAZINE

One of the

In addition, the authentication key used for remote authentication of Intel SGX has also been analyzed, and a Twitter account that opens a reply with a signature by the authentication key has also been opened.
Your quote 'You can send a tweet to our bot to get it signed! :)' has been signed. Your quote and instructions on how to verify it can be found at https://t.co/sw0D9ZRAeB .Visit https:/ /T.Co/c9VO7x0aLA For More Information. Pic.Twitter.Com/Y9AaysbmKT
— SGAxe-Bot (@SGAxe_AaaS) June 9, 2020
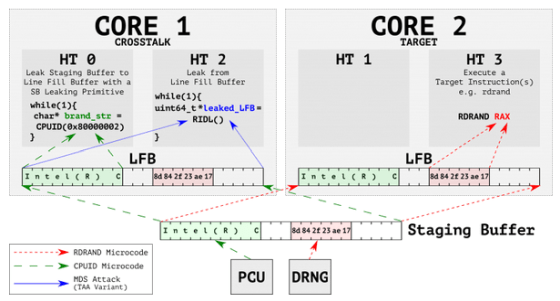
Another vulnerability reported, 'CrossTalk,' was reported by security organization VUSec . In the past attacks using MDS, the attack target and the CPU core that executes the attack program had to be the same, but in CrossTalk, data is extracted from a buffer shared by all CPU cores called 'Staging Buffer'. Therefore, it is explained that an attack that spans multiple cores is possible.
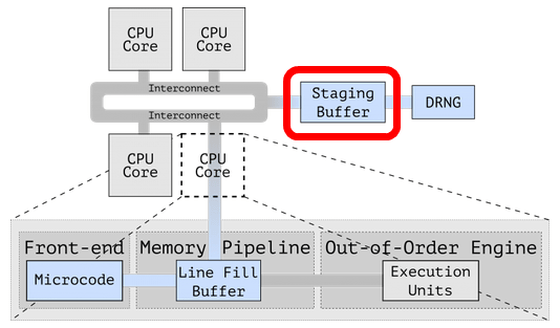
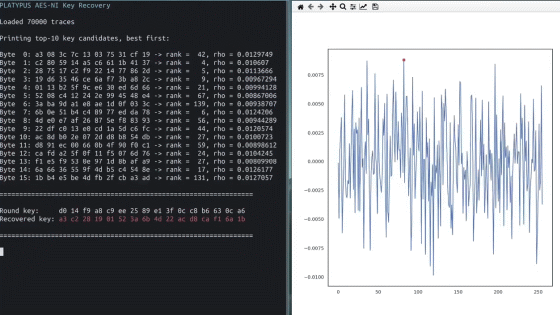
In CrossTalk, an attack such as reading the value of a general-purpose register that stores the execution result of RDRAND , which is a random number generation instruction, from another core via 'Staging Buffer' is possible. RDRAND is also used during key generation, and if the random number used during key generation is known, it will be easy to analyze the generated key itself.
According to Intel, SGAxe relies on CacheOut, which has already been patched with microcode, so it is possible to mitigate the impact by applying a patch.
Regarding CrossTalk, VUSec tested Intel CPUs released from 2015 to 2019 and confirmed that CrossTalk is effective on almost all CPUs including Xeon E3. Intel has named CrossTalk 'Special Register Buffer Data Sampling' and has already distributed patches.
Related Posts: