A vulnerability in Thunderbolt that can access data in PC in a few minutes was found, software correction is impossible

A high-speed data transmission technology '
Thunderspy-When Lightning Strikes Thrice: Breaking Thunderbolt 3 Security
https://thunderspy.io/
More Information on Thunderbolt (TM) Security-Technology @ Intel
Thunderbolt flaws affect millions of computers – even locking unattended devices won't help | ZDNet
https://www.zdnet.com/article/thunderbolt-flaws-affect-millions-of-computers-even-locking-unattended-devices-wont-help/
A series of vulnerabilities called ' Thunderspy ' discovered by researchers at the Eindhoven University of Technology such as information security researcher Björn Ruytenberg centered on attacks using DMA enabled on the Thunderbolt controller. It has become. Normally, reading and writing data is done through the CPU, but when DMA is enabled, the controller can directly access the memory to read and write data. Due to its characteristics, DMA is vulnerable to attacks when physical access is allowed, and vulnerabilities related to DMA have been previously reported .
A demo movie that actually breaks the lock screen of Windows 10 using Thunderspy has also been released.
Thunderspy PoC demo 1: Unlocking Windows PC in 5 minutes-YouTube
The laptop with Windows used for the demo is locked with a password.
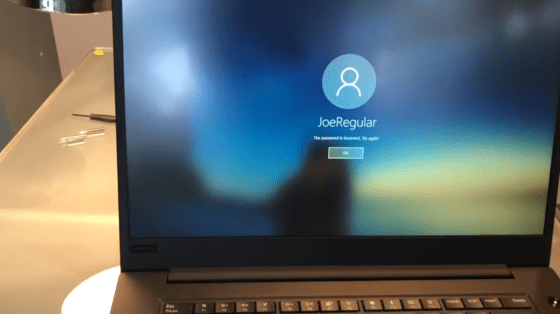
Ruytenberg turning the laptop over and removing the screws.

Remove the back cover ……

Bypasses the SPI flash implemented on the board. It is said that you will access the Thunderbolt controller from this SPI flash.
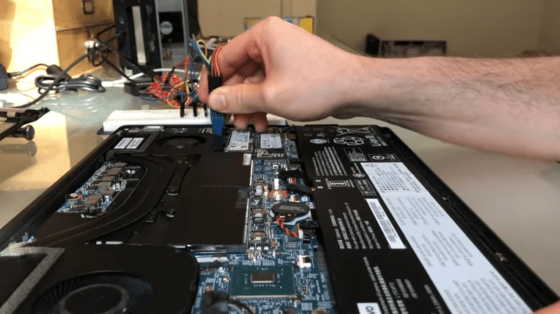
By connecting the bypassed SPI flash to the attacking MacBook Pro and running a program that exploits the vulnerability, we were able to extract the Thunderbolt controller information.
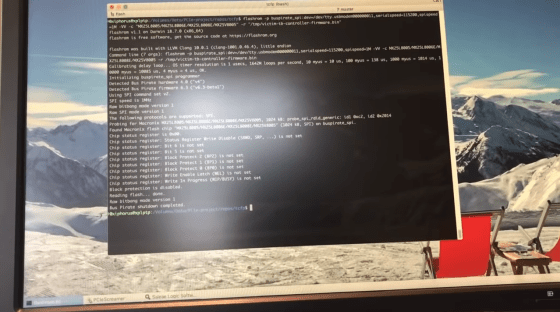
Next, Ruytenberg will disable Thunderbolt security. Normally, the security level is 'SL1', and Thunderbolt is protected.
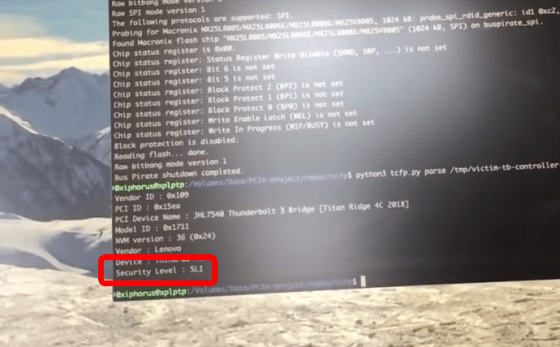
However, when Thunderspy was used for the attack, the security level was 'SL0', that is, the security could be disabled. During this time, he said that he did not leave any traces on the OS or BIOS.
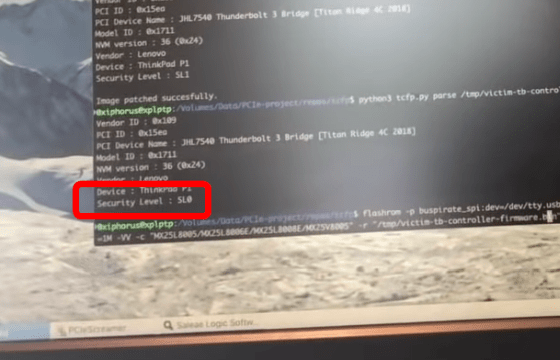
The security has been disabled, so you can freely rewrite the firmware of the Thunderbolt controller. Ruytenberg will write his own custom firmware.
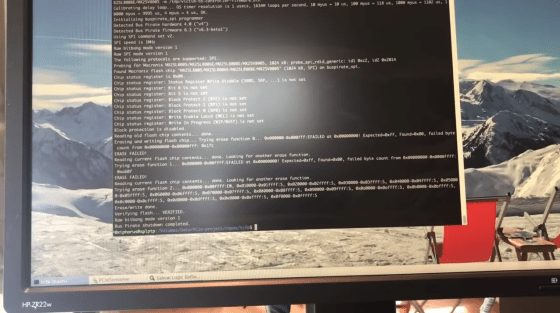
Once the firmware has been rewritten, replace the PC and insert the cable into the hacked Thunderbolt port.

Ruytenberg inserts a cable into a MacBook Pro and loads a Windows kernel module via Thunderbolt. Delete the Windows password using the loaded module.
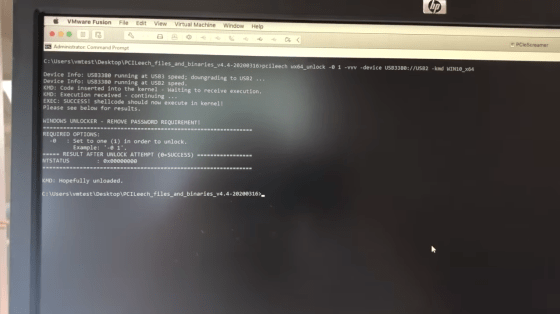
If you press Enter on the lock screen without entering a password ...
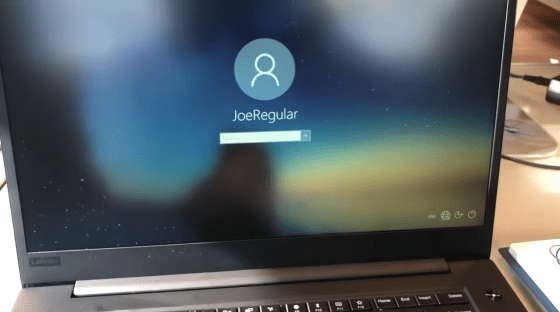
I am able to log in. It takes about 5 minutes from the start of the attack to the end, but it is possible to access the data in the PC.
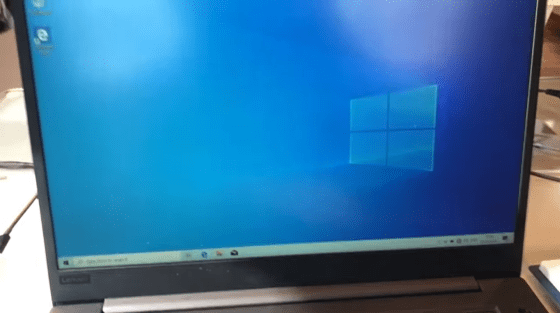
Thunderspy attacks target all Thunderbolt-equipped systems shipped between 2011 and 2020. It is reported that it cannot be fixed by software and will affect future standards such as USB4 and Thunderbolt 4. However, if you have an OS with a

These Thunderspy attacks utilize a total of 7 vulnerabilities, including improper firmware verification, weak device authentication, and SPI flash interface flaws. Ruytenberg reported the vulnerability to Intel, but it seems that he could not get it at first. Ruytenberg sent a list of affected parties to Intel, but said he did not have detailed notification regarding information disclosure.
Regarding this vulnerability, Intel announced a statement on the blog about the vulnerability. 'Thunderspy's underlying vulnerabilities are not new, and major operating systems have already implemented mitigations with kernel DMA protection. Researchers have demonstrated successful attacks on systems where these mitigations are effective. No '.
Ruytenberg has released software on GitHub that determines if the PC that I am using is affected by Thunderspy.
BjornRuytenberg / spycheck-linux: Verify whether your Thunderbolt-enabled Linux system is vulnerable to the Thunderspy attacks.
https://github.com/BjornRuytenberg/spycheck-linux
Related Posts:







