Vulnerability 'Thunderclap' which enables direct reading and writing of PC system memory via Thunderbolt port

Security researchers have discovered new vulnerabilities that affect major operating systems such as Microsoft's Windows and Apple's macOS, Linux, FreeBSD. With this vulnerability it is possible to bypass the defense mechanism against Direct Memory Access (DMA) based attacks and read and write directly to the system memory of the PC.
Thunderclap: Exploring Vulnerabilities in Operating System IOMMU Protection via DMA from Untrustworthy Peripherals
(PDF) https://www.ndss-symposium.org/wp-content/uploads/2019/02/ndss2019_05A-1_Markettos_paper.pdf
New Flaws Re-Enable DMA Attacks On Wide Range of Modern Computers
https://thehackernews.com/2019/02/thunderbolt-peripheral-dma-attacks.html
Cambridge University and Rice University, SRI International joint cyber security team has a vulnerability "Thunderclap" that can bypass the memory management unit " IOMMU " used to block DMA-based attacks exists in major operating systems It was made clear.
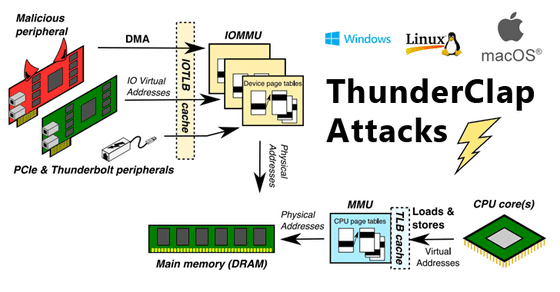
On the Thunderbolt port, connected peripheral devices bypass the OS security policy and can directly read and write to system memory including personal information such as password · bank login information · private data. As a result, security researchers point out the risks targeted by DMA-based attacks.
In fact, using an open source hacking tool " Inception ", it is easy to populate malware on peripheral devices and afterwards attacks are nearly complete only by connecting the infected device to the Thunderbolt port of the target PC . As mentioned above, system memory can be operated with much higher privilege than via normal USB port if via Thunderbolt port, so arbitrary code can be executed from infected device, unlock PC or target You can also remotely control the PC.
In other words, when launching a DMA-based attack that makes use of Thunderclap, hackers can use external Thunderbolt 3 compliant USB-Cs for peripheral devices such as external network cards, mice, keyboards, printers, external storage, It is possible to infringe the target PC simply by connecting to the port.

In the paper, "It is written that even if we are building a defense mechanism against DMA attack using IOMMU, if we exploit the vulnerability in using IOMMU of OS, we can put the target system at risk through DMA" I will. In addition to this, initially IOMMU is invalid by default on most OSs, and the latest devices are equipped with USB-C ports, so many Thunderclap influences are increasing I can say
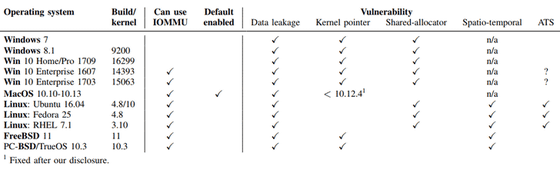
The following figure shows whether each version of the main OS corresponds to IOMMU or whether it is enabled by default. In the figure, IOMMU is enabled by default only for macOS 10.10 to 10.13.
Security researchers said, "With the advent of something like Thunderbolt 3 compatible USB-C port that combines power input, video output, and peripheral DMA all on the same port, the possibility of vulnerability · Thunderclap spreading in the real world "It is pointed out that the danger of Thunderclap has been increased by the flow of trying to cover many functions with one port.
In addition, especially Apple computers manufactured after 2011 are all vulnerable except for the 12-inch MacBook. In addition, researchers point out that PCs equipped with Windows or Linux manufactured after 2016 will also be heavily influenced.
Researchers have already reported about Thunderclap to OS vendors and PC makers, and many manufacturers already deal with Thunderclap. Specifically, Apple has resolved the vulnerability of certain network cards used to realize root shell at macOS 10.12.4 and later, Intel distributes patches for version 5.0 of the Linux kernel It is.
Not all software patches can completely block DMA attacks, but it is clear that it is useful to reduce attack targets, so The Hacker News recommends "install security updates" I am doing. Security researchers also cite "to invalidate Thunderbolt ports on PC" as the best protection against Thunderclap.

Security researchers have also developed hardware for concept verification for hacking the target system using Thunderclap, but it is not disclosed at the time of article creation.
Related Posts: