It turns out that the `` fixed '' vulnerability of Intel CPUs was actually unfixable, allowing privileged code execution and avoiding DRM etc.

Many vulnerabilities have been found in Intel CPUs in recent years, including '
Positive Technologies: Unfixable vulnerability in Intel chipsets threatens users and content rightsholders
https://www.ptsecurity.com/ww-en/about/news/unfixable-vulnerability-in-intel-chipsets-threatens-users-and-content-rightsholders/
Positive Technologies-learn and secure: Intel x86 Root of Trust: loss of trust
http://blog.ptsecurity.com/2020/03/intelx86-root-of-trust-loss-of-trust.html
5 years of Intel CPUs and chipsets have a concerning flaw that's unfixable | Ars Technica
https://arstechnica.com/information-technology/2020/03/5-years-of-intel-cpus-and-chipsets-have-a-concerning-flaw-thats-unfixable/
Intel CSME bug is worse than previously thought | ZDNet
https://www.zdnet.com/article/intel-csme-bug-is-worse-than-previously-thought/
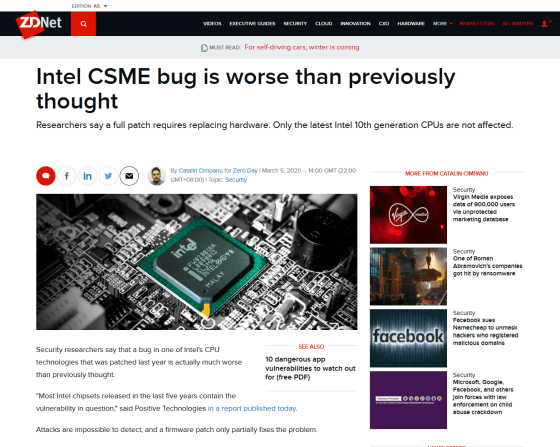
Intel CSME operates at the initial stage of booting a computer, plays a central role in encryption functions based on Intel products such as
In May 2019, Intel released a firmware patch ' INTEL-SA-00213 ' that fixes a vulnerability ' CVE-2019-0090 ' related to Intel CSME. At the time, it was described as a vulnerability that allowed privileged code to be executed only if the CPU had physical access. This patch can prevent attacks on Intel CSME via ISH which processes external input.
INTEL-SA-00213
https://www.intel.com/content/www/us/en/security-center/advisory/intel-sa-00213.html
However, a research by security company Positive Technologies researchers found that Intel CSME was not protected on boot ROM at startup. Even without going through the ISH, it was found that when reading the boot ROM, malicious code could be executed, DRM could be avoided, and input from the USB keyboard could be obtained illegally.
In addition, it is a highly vulnerable vulnerability that requires only local access to the CPU, such as executing malware hidden in the computer without requiring physical access to the CPU, and is recorded It has been reported that a complete fix in the firmware is not possible because the mask ROM , whose contents cannot be rewritten, contains a vulnerability.
Affected by this vulnerability are all CPUs sold in the past five years from 2020, except Intel's 10th generation CPU. Positive Technologies researchers say that CPUs need to be replaced to completely fix the vulnerability.
Related Posts:
in Security, Posted by darkhorse_log