A vulnerability is discovered that can break through multiple security layers of macOS and read all files

A vulnerability that can break through the multiple security layers provided in
Process injection: breaking all macOS security layers with a single vulnerability Sector 7
https://sector7.computest.nl/post/2022-08-process-injection-breaking-all-macos-security-layers-with-a-single-vulnerability/
A Single Flaw Broke Every Layer of Security in MacOS | WIRED UK
https://www.wired.co.uk/article/macos-process-injection-flaw
The macOS vulnerability discovered by Sector 7 researchers is related to the function `` reopen the last opened window when logging in after restart' ' installed in macOS. When restarting or shutting down on a Mac, the option 'Reopen windows when logging in again' is displayed, and if you check it, the previously opened apps and windows will be automatically displayed, and documents that were not saved by the app will be displayed. It is also possible to restore. This function is not necessarily used only at shutdown, but is also used in a process called App Nap , which suspends the processing of apps running in the background to reduce power consumption.
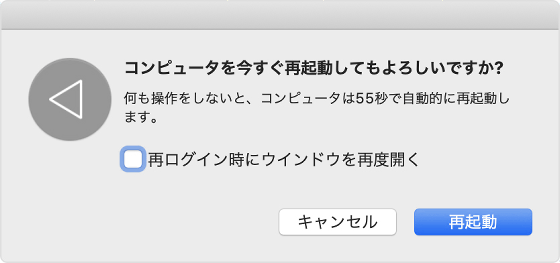
macOS creates files that record windows and apps, and reads and restores these files when it starts up. However, it is possible to execute harmful code by using a ' process injection ' attack that replaces the serialized objects contained in these files with malicious versions.
Sector 7 has shown that it is possible to circumvent the security function ' sandbox ' installed in macOS by using a process injection attack. A sandbox is a defense system that restricts access to system resources so that malicious applications can run with minimal impact. However, it has been reported that it was possible to escape the sandbox and extend the attack range by executing malicious code in conjunction with shutdown and file restoration at startup.
Sector 7 also said it was able to perform privilege escalation by injecting code into apps with certain entitlements, as well as bypass system integrity protections that prevent access to sensitive files on the Mac. This allowed the attacker to read virtually all files on the Mac and control the webcam.
'Essentially one vulnerability can be applied to three different attack surfaces,' said Thijs Alkemade, a security researcher at Sector 7. , it is very rare to find something so universally applicable.'

Alkemade discovered the vulnerability in December 2020 and contacted Apple through the bug bounty program, which he said was a ``pretty good'' bounty. Apple seems to have fixed these flaws in two updates, but it has been pointed out that the vulnerabilities may still work on macOS older than macOS Montrey .
At the time of writing the article, no evidence was found that the discovered vulnerability was exploited, but this case raises the possibility that the attacker will be able to move the entire OS and access more and more data. It is showing.
Related Posts: