AMD distributes security patches to fix 50 vulnerabilities, Intel 25

On November 9, 2021, AMD fixed a total of 50 vulnerabilities, including 27 graphics driver vulnerabilities for Windows 10, 22 Epyc processor vulnerabilities, and 1 μProf vulnerabilities. Intel has also fixed a total of 25 vulnerabilities, including 10 vulnerabilities related to Wi-Fi products.
AMD reveals an Epyc security 50 flaws, Intel has 25 • The Register
https://www.theregister.com/2021/11/12/amd_and_intel_flaws/
AMD fixes dozens of Windows 10 graphics driver security bugs
https://www.bleepingcomputer.com/news/security/amd-fixes-dozens-of-windows-10-graphics-driver-security-bugs/
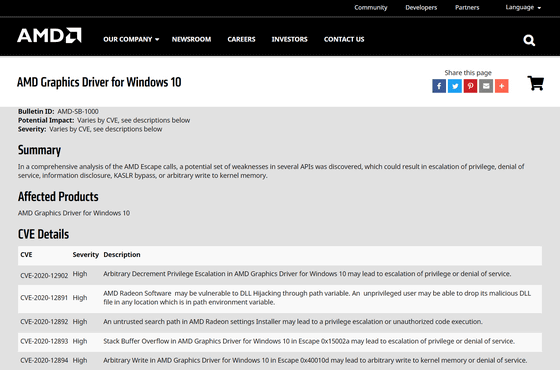
AMD's new security patch for graphics drivers for Windows 10 fixes a total of 27 vulnerabilities. Eighteen of them have been certified as 'Severity: High', and some of them are vulnerabilities that enable privilege escalation, denial of service (DoS), arbitrary writing to kernel memory, malicious code execution, memory corruption, information leakage, etc. is included.
The Common Vulnerabilities and Exposures (CVEs) assigned to these 27 vulnerabilities are:
CVE-2020-12902, CVE-2020-12891, CVE-2020-12892, CVE-2020-12893, CVE-2020-12894, CVE-2020-12895, CVE-2020-12898, CVE-2020-12901, CVE- 2020-12903, CVE-2020-12900, CVE-2020-12929, CVE-2020-12960, CVE-2020-12980, CVE-2020-12981, CVE-2020-12982, CVE-2020-12983, CVE-2020- 12985, CVE-2020-12986, CVE-2020-12962, CVE-2020-12904, CVE-2020-12905, CVE-2020-12964, CVE-2020-12987, CVE-2020-12920, CVE-2020-12899, CVE-2020-12897, CVE-2020-12963
Details of each can be confirmed from the following.
AMD Graphics Driver for Windows 10 | AMD
https://www.amd.com/en/corporate/product-security/bulletin/amd-sb-1000
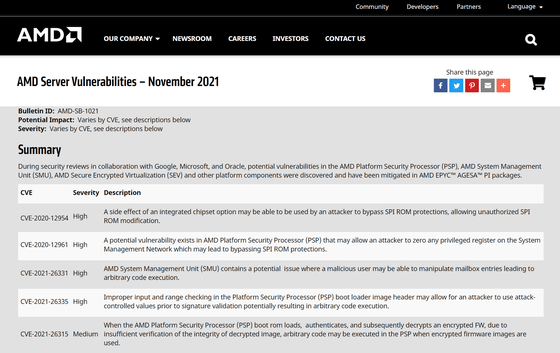
AMD has also distributed security patches for Epyc processors that fix a total of 22 vulnerabilities. Some of the vulnerabilities include those that allow SPI ROM protection bypass and arbitrary code execution. These CVE identifiers are:
CVE-2020-12954, CVE-2020-12961, CVE-2021-26331, CVE-2021-26335, CVE-2021-26315, CVE-2020-12946, CVE-2020-12951, CVE-2021-26336, CVE- 2021-26337, CVE-2021-26338, CVE-2021-26320, CVE-2020-12944, CVE-2020-12988, CVE-2021-26329, CVE-2021-26330, CVE-2021-26321, CVE-2021- 26323, CVE-2021-26325, CVE-2021-26326, CVE-2021-26322, CVE-2021-26327, CVE-2021-26312
You can check the details here from the following.
AMD Server Vulnerabilities – November 2021 | AMD
https://www.amd.com/en/corporate/product-security/bulletin/amd-sb-1021
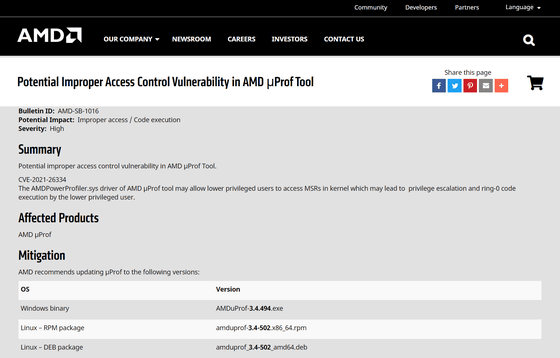
In addition, a security patch for the μProf tool vulnerability 'CVE-2021-26334' has also been distributed. The vulnerability could allow a less privileged user to elevate privileges or execute ring 0 code. Details are below.
Potential Improper Access Control Vulnerability in AMD μProf Tool | AMD
https://www.amd.com/en/corporate/product-security/bulletin/amd-sb-1016
Meanwhile, Intel also distributed a series of security patches on November 9th that fix a total of 25 vulnerabilities. The following vulnerabilities have been fixed this time by the unique vulnerability identifier issued by Intel.
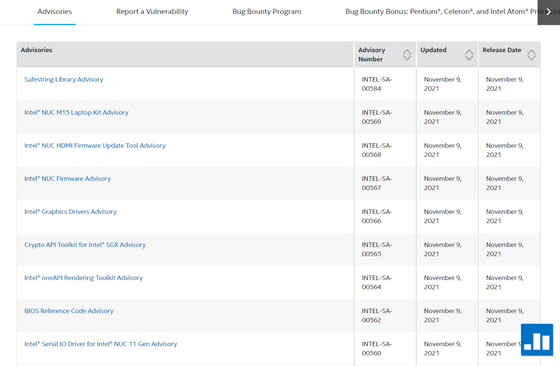
INTEL-SA-00393, INTEL-SA-00481, INTEL-SA-00482, INTEL-SA-00509, INTEL-SA-00524, INTEL-SA-00528, INTEL-SA-00533, INTEL-SA-00535, INTEL- SA-00538, INTEL-SA-00540, INTEL-SA-00547, INTEL-SA-00551, INTEL-SA-00554, INTEL-SA-00555, INTEL-SA-00556, INTEL-SA-00557, INTEL-SA- 00560, INTEL-SA-00562, INTEL-SA-00564, INTEL-SA-00565, INTEL-SA-00566, INTEL-SA-00567, INTEL-SA-00568, INTEL-SA-00569, INTEL-SA-00584
Among them, the ones with 'Severity: High' are as follows.
INTEL-SA-00509: A combination of 10 vulnerabilities included in Intel's Wi-Fi products that enables privilege escalation, service denial, and information disclosure.
INTEL-SA-00535: Refers to CVE-2021-0148 that affects multiple Intel SSDs. Insert information into firmware log files to allow privileged users to disclose information via local files.
INTEL-SA-00528: Privilege promotion for Pentium, Celeron and Atom silicon.
INTEL-SA-00562: Rogue BIOS allows privilege escalation on some of the 2016 Intel Core series and 2013 Celeron.
Each vulnerability can be referred from the following.
Security Center
https://www.intel.com/content/www/us/en/security-center/default.html
Related Posts:
in Security, Posted by darkhorse_log