An attack `` CacheOut '' to extract data using a new vulnerability `` L1D eviction sampling '' of Intel CPU is reported

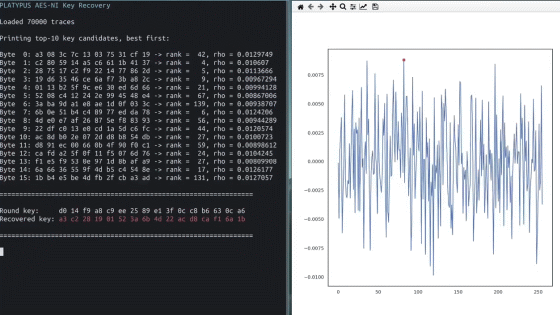
Security researchers released a targeted attack ` ` CacheOut '' that leaks confidential data from CPU using the L1D eviction sampling (CVE-2020-0549) vulnerability of Intel CPUs released before the third quarter of 2018 Reported by Intel has acknowledged the vulnerability and the danger of Cacheout, and states that it will release a mitigation for this vulnerability in the near future, in the form of a BIOS or driver update.
CacheOut
L1D Eviction Sampling
https://software.intel.com/security-software-guidance/software-guidance/l1d-eviction-sampling
L1D eviction sampling and CacheOut were discovered by Stefan Van Scheik of the University of Michigan and a team at the security research organization VUSEC. The vulnerability was reported to Intel in an undisclosed form, after which Intel took measures to disclose it.
Some Intel CPUs have a feature called Intel TSX . This Intel TSX manages the necessary data on the CPU's L1 cache, but with this Intel TSX instruction it is possible to eviction from the L1 cache to an unused buffer, and you can infer data from this buffer Turned out to be possible. Cacheout, which exploits this vulnerability to extract data using L1D eviction sampling, violates almost all hardware-based security domains and uses OS kernels, virtual machines, and even Intel SGX enclaves (private Area) can be extracted from the data.
In May 2019, a vulnerability `` MDS '' affecting Intel processors and an attack `` ZombieLoad '' using it were discovered, and in 2019, a variant of ZombieLoad `` ZombieLoad v2 '' was also discovered . MDS is vulnerable to inferring data from microarchitecture buffers, and OS vendors have updated the OS to overwrite buffers as a mitigation. However, CacheOut forces any data from the L1 cache to the buffer after the OS overwrites the buffer, and pulls data from it.
The attack also bypasses the mitigation for the ' meltdown ' vulnerability reported on Intel CPUs in May 2019, requiring further software fixes. Although it has been demonstrated that CacheOut is feasible, the research team has reported that CacheOut has never been run before. Also, it seems that there is almost no trace of it even after being attacked by CacheOut.
Below is a list of CPUs that may be affected by L1D eviction sampling. Note that AMD CPUs that do not have functions similar to Intel TSX are not affected by L1D eviction sampling. While ARM and IBM processors have similar features, it is unknown at the time of this writing whether they will be affected by L1D eviction sampling.
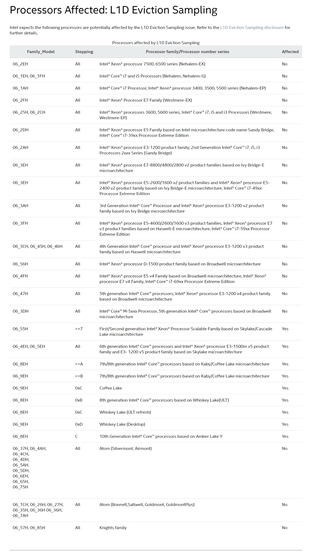
Intel has stated that it will release a microcode update for affected processors in response to CacheOut.
Related Posts: