A new type "Variant 4" appears in the vulnerability "Specter" inherent in the CPU, Intel · AMD · ARM announces countermeasures

Vulnerability inherent in CPU such as Intel "Specter", Newly"Variant 4"Has been added. For Variant 4 discovered by Microsoft and Google Project Zero, Intel, AMD, ARM have announced correspondence respectively.
ADV180012 | Microsoft Guidance for Speculative Store Bypass
https://portal.msrc.microsoft.com/en-US/security-guidance/advisory/ADV180012
1528 - speculative execution, variant 4: speculative store bypass - project - zero - Monorail
https://bugs.chromium.org/p/project-zero/issues/detail?id=1528
Specter Variant 4 is also a side channel attack that exploits the "speculative execution" processing that the CPU performs like the already discovered Spctre, and a new subclass is given according to the attack content "Speculative Store Bypass (SSB)" It is. By exploiting Variant 4's vulnerability, an attacker could read privileged data.
About Variant 4, Intel announced the official announcement as follows and clarifies that it is planned to respond.
Addressing New Research for Side-Channel Analysis | Intel Newsroom
https://newsroom.intel.com/editorials/addressing-new-research-for-side-channel-analysis/
Intel's Leslie Calvertzon says, "First of all, let me start talking about not being reported that the damage was caused by abusing Variant 4". According to Intel, Variant 4 can be handled by a patch for Specter Variant 1 and 2 already released. He then states that it plans to offer additional mitigation measures for Variant 4 in combination with microcode for Variant 4 and software updates by partner companies.
The beta version of the Variant 4 microcode update has already been provided to OEM system makers and some software vendors and will be provided as BIOS or software update within the next few weeks. However, although patch application test showed "There was no effect on performance," it also revealed that the benchmark measurements such as SYSmark 2014 SE and SPEC had a performance drop of 2 to 8% .
In the demonstration test of the Project Zero team, AMD has demonstrated the following attack as demonstrated attack using Variant 4 in "A8-9600 R7".
AMD Processor Security | AMD
https://www.amd.com/en/corporate/security-updates#paragraph-290416
According to AMD, Microsoft has already completed the final test and verification of updates for AMD CPUs for Windows clients and Windows servers. These updates will be released as standard security updates. Please note that SSB updates for Linux distributors are in development, so users want you to follow the guidance of each Linux distributor.
In the test of Project Zero, the ARM which the product is not checked also clarifies the view on Variant 4 as follows.
Speculative Processor Vulnerability - Arm Developer
https://developer.arm.com/support/arm-security-updates/speculative-processor-vulnerability
The newly discovered Variant 4 is a side channel attack on cache timing, and it is said that it is not a new idea already known for security research. And he says, "Most ARM processors are not affected by this type of side channel speculative execution."
Below is a list of influences on the Specter problem by ARM announcement.
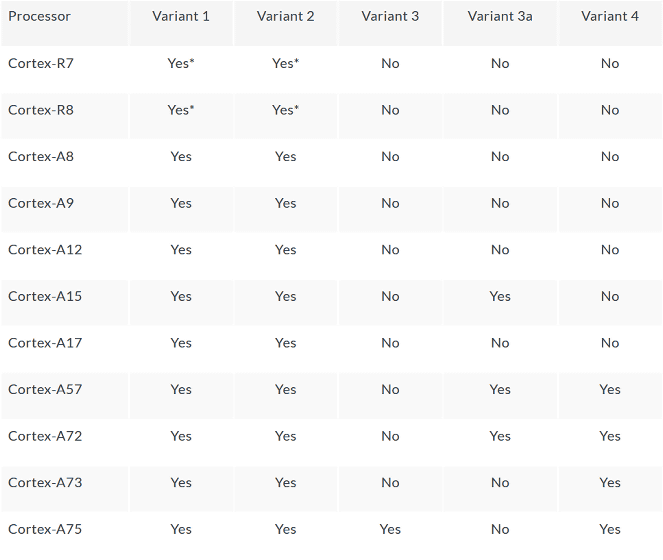
About Cortex-A 57, Cortex-A 72, Cortex-A 73, and Cortex-A 75 of "Yes" in Variant 4, in the Linux OS,memory disambiguationIt depends on whether it can invalidate or not. Therefore, we should wait for support by trusted firmware to be released.
Related Posts: