Vulnerability to crack encryption key from 'power consumption monitoring data' revealed in Intel CPU
A vulnerability ' PLATYPUS ' has been discovered that allows Intel CPUs to perform
PLATYPUS: With Great Power comes Great Leakage
https://platypusattack.com/
INTEL-SA-00389
https://www.intel.com/content/www/us/en/security-center/advisory/intel-sa-00389.html
Intel SGX defeated yet again—this time thanks to on-chip power meter | Ars Technica
https://arstechnica.com/information-technology/2020/11/intel-sgx-defeated-yet-again-this-time-thanks-to-on-chip-power-meter/
Intel CPUs vulnerable to'Platypus' side-channel attacks | IT PRO
https://www.itpro.co.uk/security/357719/intel-cpu-platypus-side-channel-attacks-discovered
Intel Discloses 40 More Security Advisories --PLATYPUS Is An Interesting One --Phoronix
https://www.phoronix.com/scan.php?page=news_item&px=Intel-40-More-Playpus
Intel CPUs have an interface called ' RAPL ' that allows you to monitor power consumption from your PC. RAPL is also used by large vendors such as Fujitsu, and is a technology that is so popular that the RAPL module is loaded by default in the Linux kernel. Since the sampling frequency of RAPL is 20kHz, which is coarser than that of an oscilloscope, and the data is averaged, it has been considered difficult to decrypt encrypted data based on RAPL information.
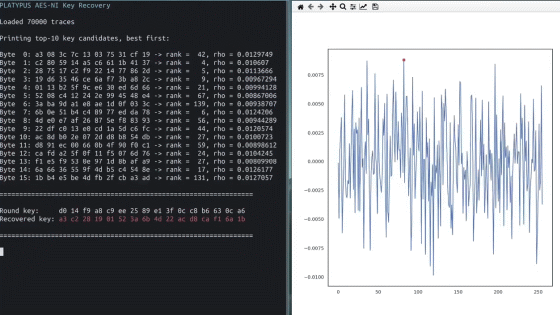
However, a security team consisting of researchers from Graz University of Technology and the University of Birmingham used RAPL to conduct side-channel attacks and succeeded in breaking the encryption key in Intel's security function ' Intel SGX '. This attack is named ' PLATYPUS ', which means 'platypus' that has a sensory organ that receives electricity, and is characterized by being able to perform side-channel attacks without physically measuring power with an oscilloscope.
It is said that the decryption of the encryption key has been achieved by two vulnerabilities by RAPL. The first is a vulnerability that allows the data being processed by the CPU to be inferred from RAPL.
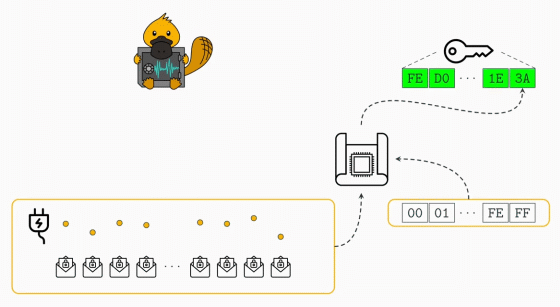
The second is a vulnerability that can predict the
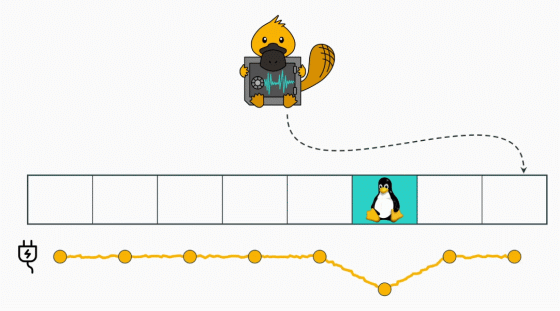
CPU affected by the PLATYPUS as led by Core series from the sixth generation of the Intel until the 10th generation, Pentium and Celeron, until the Xeon series
On the software side, Linux loads the kernel module for RAPL by default, and even unprivileged users can access RAPL data as follows, so it will be greatly affected by PLATYPUS. Since RAPL is available for Windows and macOS only after installing Intel Power Gadget , the impact is limited.
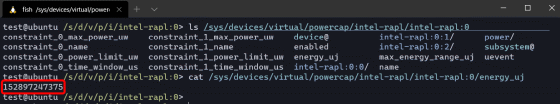
In addition, the Linux kernel has already been modified to prohibit unauthorized users from accessing RAPL, and Xen in the virtual environment has also distributed a patch . Microsoft has also released a microcode security patch for Windows.
Related Posts:






