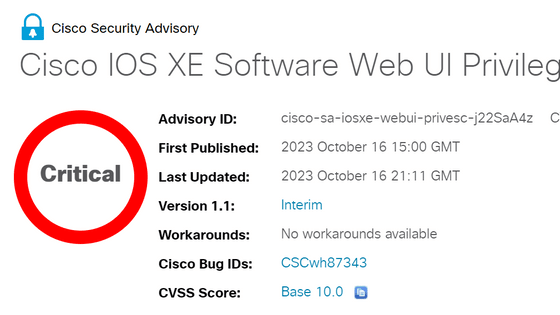
Vulnerability 'USBAnywhere' affecting over 47,000 Supermicro servers

Eclypsium , a cyber security company, has reported a vulnerability “ USBAnywhere ” that affects the
Virtual Media Vulnerability in BMC Opens Servers to Remote Attack-Eclypsium
https://eclypsium.com/2019/09/03/usbanywhere-bmc-vulnerability-opens-servers-to-remote-attack/
New USBAnywhere Vulnerabilities Leave Supermicro Server BMCs Open to Remote Attack-SecAlerts-Security vulnerabilities in your inbox
https://secalerts.co/article/supermicro-server-bmcs-left-exposed-to-remote-attack-by-any-usb-device/67ea5a84
The new vulnerability “USBAnywhere” discovered by Eclypsium on the Supermicro server allows attackers to connect to the server and remotely mount any USB device selected on the server. Multiple vulnerabilities in virtual media services for handling disk images as virtual USB / CD-ROM / floppy drives when BMC on Supermicro server board X9 / X10 / X11 series implements virtual media It seems to have been found.
When accessing the BMC on the Supermicro server board remotely, the virtual media service allows authentication in plain text , so most traffic appears to be sent unencrypted. Although some traffic is encrypted, it is highly likely that authentication will be bypassed because many remain unencrypted.
An attacker can gain access to the server by intercepting the communications of a user who has access to the server and stealing credentials or using default credentials. There are also cases where access is possible without credentials.

by
When accessing the server remotely, it seems that the attacker can communicate with the host system as a USB device via the virtual media service. Access to the virtual media service is facilitated by the 'BMC web interface by Java application to connect to the virtual media service', which is usually listening on BMC TCP port 623.
According to Eclypsium's analysis, one of the problems lies in 'Java application authentication', where usernames and passwords are used in plain text.
The second problem is that “network traffic is not encrypted”. Although encryption can be used at the request of the client, only the initial authentication packet of the Java application is encrypted by default. It seems that all traffic at is not encrypted.
The third problem is “encryption is weak”. The BMC on the Supermicro server board uses a fixed key compiled into the BMC firmware for encryption and is encrypted with RC4 . However, this encryption key is shared by BMC on all Supermicro server boards, and RC4 has been pointed out to have multiple encryption vulnerabilities, so many web browsers are no longer supported .
The fourth problem is 'authentication bypass', which seems to be a vulnerability that exists only in the X10 and X11 series. In these series, it seems that some of the internal state about the client remains accidentally left after the client is disconnected from the virtual media service. This internal state is linked to the client's file descriptor , and depending on the BMC OS, this file descriptor may continue to be used for other clients. Therefore, even if a new client tries to authenticate with incorrect credentials, there seems to be a case where authentication of the previous client is continued.
by Thomas Jensen
Of particular concern is the fourth “authentication bypass” vulnerability, which ZDNet says about this: “This vulnerability is placed in the same server socket used by legitimate administrators, so that hackers It will be possible to repeatedly connect to the web interface virtual media service. '
Eclypsium said, “By combining a framework that can implement USB devices in software (with USBAnywhere), an attacker can emulate a device. This combination of features can even allow an attacker to boot '
Supermicro has received a report from Eclypsium and has released patches for the X9 / X10 / X11 series.
BMC / IPMI Security Vulnerability Update September 3, 2019
https://www.supermicro.com/support/security_BMC_virtual_media.cfm
Related Posts: