Arbitrary BIOS / UEFI level code execution is possible to find critical vulnerabilities affecting over 30 million Dell devices on 129 models

A vulnerability was found in Dell's Support
Eclypsium Discovers Multiple Vulnerabilities in Dell BIOS Connect
https://eclypsium.com/2021/06/24/biosdisconnect/#mitigations
Dell SupportAssist bugs put over 30 million PCs at risk
https://www.bleepingcomputer.com/news/security/dell-supportassist-bugs-put-over-30-million-pcs-at-risk/
30M Dell Devices at Risk for Remote BIOS Attacks, RCE | Threatpost
https://threatpost.com/dell-bios-attacks-rce/167195/
30 million Dell devices affected by BIOSConnect code execution bugs
https://www.hackread.com/dell-devices-biosconnect-code-execution-bugs/
Flaws in Dell BIOSConnect feature affect 128 device models Security Affairs
https://securityaffairs.co/wordpress/119369/security/dell-biosconnect-flaws.html
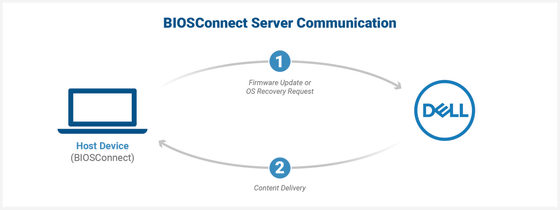
BIOSConnect is Dell's support solution that lets the BIOS perform HTTPS communication with Dell's backend services to perform the update / recovery process. Dell Support leverages BIOS Connect to update system firmware and perform system restore operations online.
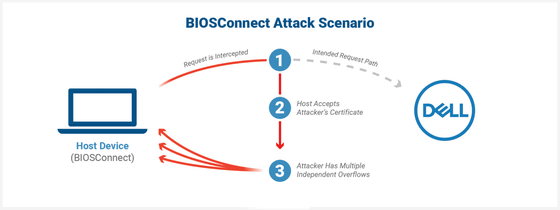
A new vulnerability identified by security company Eclypsium is that an attacker can impersonate Dell.com to execute arbitrary code at the BIOS / UEFI level from BIOS Connect. By exploiting this vulnerability, an attacker could remotely execute code from the pre-boot state of the OS, take control of the device boot process, and destroy the OS and higher-level security controls. It is possible. This vulnerability is attributed to the fact that the TLS connection from BIOS Connect accepts arbitrary wildcard certificates when BIOS Connect attempts to make an HTTPS connection to Dell's backend service.
Support Assist, including BIOS Connect, is used on almost all Windows-based Dell PCs, and all 129 models including Dell desktop PCs, notebook PCs, and tablets are expected to be affected. Shipments of all 129 models are expected to exceed 30 million units, so the impact is expected to be widespread.
Eclypsium identified this vulnerability in March 2021, but in consultation with Dell, a disclosure date was set, and on the same day as the disclosure date, Dell distributed a BIOS firmware update for clients that fixes the vulnerability. did. It is said that this firmware update can be installed via SupportAssist, but Eclypsium says, 'It is recommended to run the BIOS update file from the OS after matching the hash of the update file with the hash published by Dell.' It states and recommends a manual update.
Related Posts:
in Security, Posted by darkhorse_log