Google reports security vulnerabilities in AMD CPUs

Google's security team has reported security vulnerabilities in some of AMD's Zen architecture CPUs, including its EPYC brand of products for servers and embedded systems.
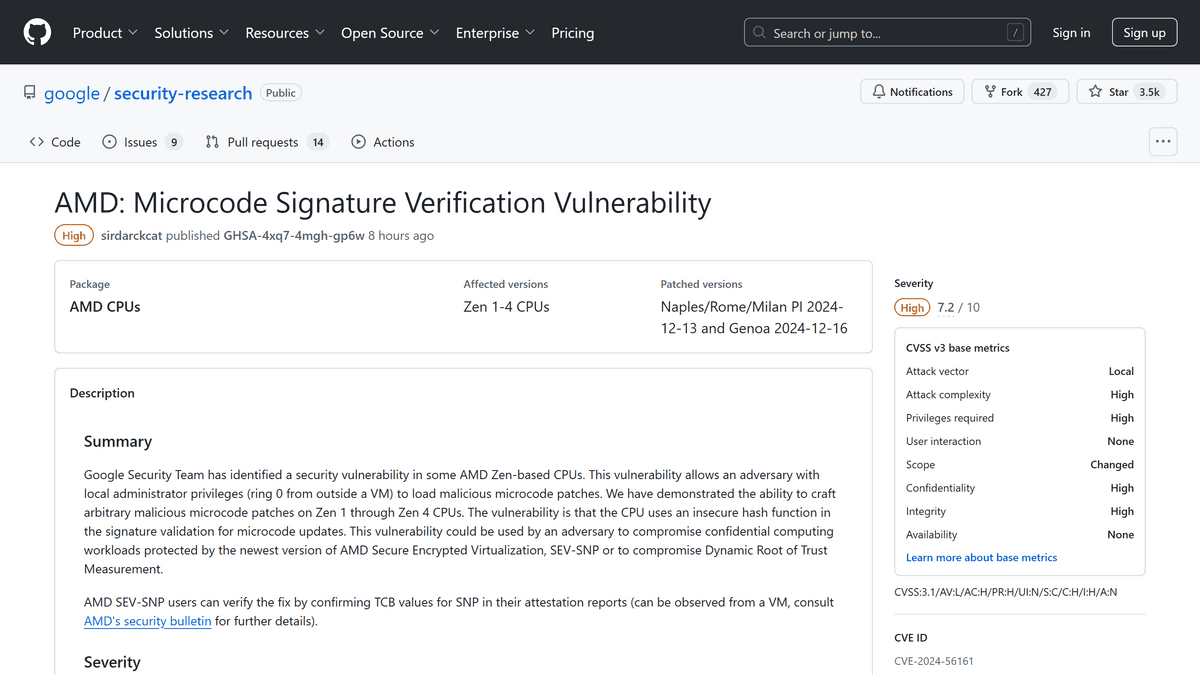
AMD: Microcode Signature Verification Vulnerability · Advisory · google/security-research · GitHub
https://github.com/google/security-research/security/advisories/GHSA-4xq7-4mgh-gp6w
AMD SEV Confidential Computing Vulnerability
https://www.amd.com/en/resources/product-security/bulletin/amd-sb-3019.html
Many recent CPUs use microcode to implement complex instructions within the CPU. According to Google, the EPYC series CPUs use an insecure hash function to verify the digital signature when updating the microcode.
Although the attack requires local administrator privileges, the attacker can perform any operation by rewriting the CPU microcode. The EPYC series is equipped with a mechanism called SEV to protect virtual machines from the host, but by exploiting this vulnerability, this protection can be broken and virtual machine information can be accessed. The severity of the vulnerability is 'high' and the CVSS score is 7.2.
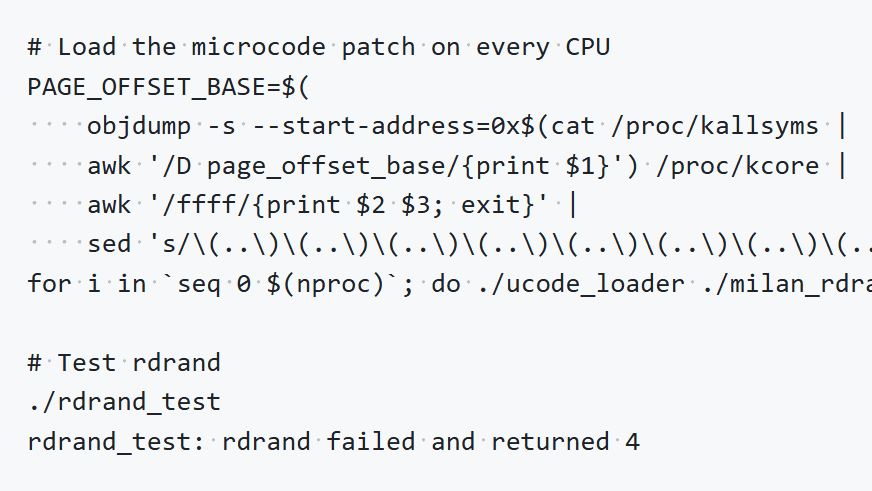
Google has prepared proof-of-concept code for the EPYC 7003 (Milan) series and EPYC 9004 (Genoa) series. When the proof-of-concept code provided by Google is executed, the RDRAND instruction that generates random numbers in a vulnerable CPU is rewritten to always return a fixed value of 4. Note that local administrator privileges are required to run the code.
Google notified AMD about the vulnerability on September 25, 2024, and AMD provided a patch on December 17, 2024. Virtual machine users can determine whether a host is vulnerable by checking the SNP TCB value listed in the authentication report generated when the virtual machine is started. The specific values that should be used are listed on
AMD's security information page
.Google has withheld some information as of February 3, 2025, stating that 'the problem is deep-rooted and will take time to reconstruct.' It plans to release more detailed information and tools on March 5, 2025.
Related Posts: