'BadRAM' attack completely destroys the reliability of AMD's cloud machines for just 1,500 yen

A proof-of-concept attack called 'BadRAM' has been released that can circumvent AMD's 'Secure Encrypted Virtualization (SEV)' that encrypts and protects memory with just $10 (about 1,500 yen) equipment and a few minutes of time. This significantly undermines the reliability of AMD products that are widely adopted by major cloud providers such as Amazon AWS, Google Cloud, and Microsoft Azure, the researchers say.
BadRAM
AMD's trusted execution environment blown wide open by new BadRAM attack - Ars Technica
https://arstechnica.com/information-technology/2024/12/new-badram-attack-neuters-security-assurances-in-amd-epyc-processors/
The BadRAM attack, discovered by a research team from the Catholic University of Leuven in Belgium, the University of Lübeck in Germany, and the University of Birmingham in the UK, tampers with the SPD chip installed in memory to circumvent the security features of AMD's Trusted Execution Environment (TEE) technology.
The SPD chip is responsible for transmitting information such as memory capacity to the BIOS, but to rewrite that information, the research team used a Raspberry Pi Pico , which they bought for $5 (about 750 yen), and it cost only about $10 including the power supply.
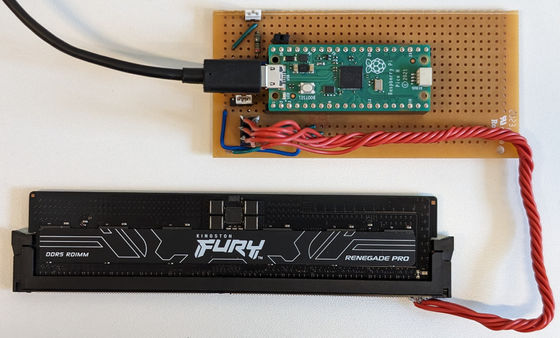
The basic mechanism of a BadRAM attack is as follows: First, an attacker uses a device like the one described above to tamper with the memory SPD chip, tricking the CPU into thinking it has twice the memory capacity it actually does, and tricking it into accessing non-existent 'ghost addresses' that are mapped to existing memory areas. If the chip is not properly protected, it may not even be necessary to have physical access to the server.
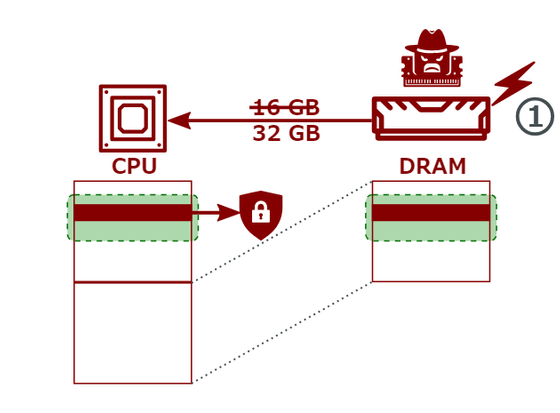
This way, two CPU addresses are now mapped to the same DRAM area.
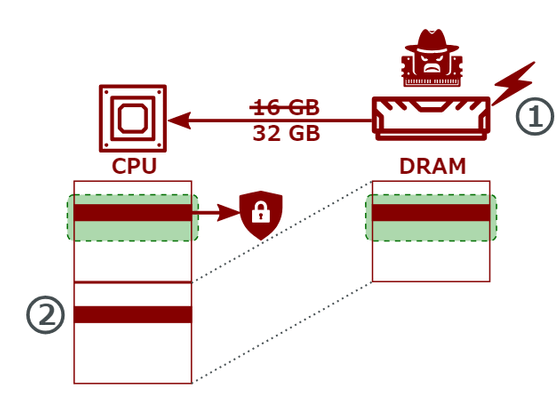
This allows attackers to circumvent the CPU's memory protection features and access sensitive data.
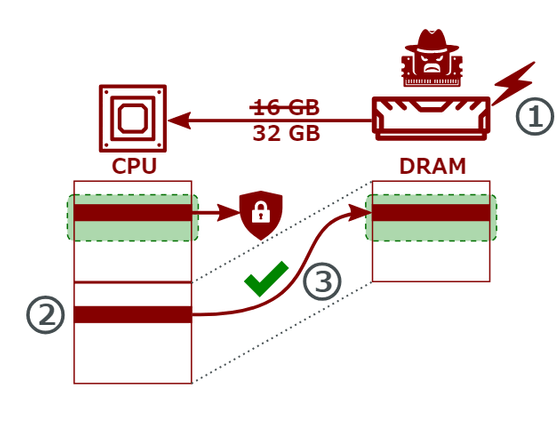
When the research team tested it with Intel's Software Guard Extensions (SGX), a competitor of AMD, they found that it was possible to read the code with the discontinued version of SGX, but not write it. They also found that it was not possible to read it with the new Scalable SGX or Trust Domain Extensions (TDX). It is unclear whether BadRAM is effective because they were unable to obtain an Arm processor.
The details are summarized in the table below.
| TEE | Import | write |
|---|---|---|
| AMD SEV-SNP | ○ | ○ |
| Intel Classic SGX | ○ | × |
| Intel Scalable SGX | × | × |
| Intel TDX | × | × |
| Arm CCA | ? | ? |
'BadRAM completely undermines trust in AMD's Secure Encrypted Virtualization (SEV-SNP) technology, which is widely deployed by major cloud providers such as Amazon AWS, Google Cloud, and Microsoft Azure,' the research team said.
In response to this, AMD has released firmware updates to mitigate the vulnerability to BadRAM attacks.
In a statement to the media, AMD said, 'AMD believes that to exploit the disclosed vulnerabilities, an attacker would need to have physical access to the system, access to the OS kernel of a system with unlocked memory, or install a customized malicious BIOS. The company also recommends the use of memory modules that lock the SPD and following physical system security best practices.'
Related Posts:
in Security, Posted by log1l_ks