It is pointed out that the target range of the 'Rowhammer' attack that falsifies the data stored in DRAM is expanding due to memory miniaturization
The 'Rowhammer ' attack, which exploits the vulnerability of being able to tamper with data stored at another address by repeatedly accessing one address of DRAM, has declined considerably due to countermeasures by chip makers. However, Google researchers have announced that there is a new technique called 'Half-Double ' that allows attacks to propagate across adjacent lines.
Google Online Security Blog: Introducing Half-Double: New hammering technique for DRAM Rowhammer bug
hammer-kit / 20210525_half_double.pdf at main · google / hammer-kit · GitHub
Google says Rowhammer attacks are gaining range as RAM is getting smaller | The Record by Recorded Future
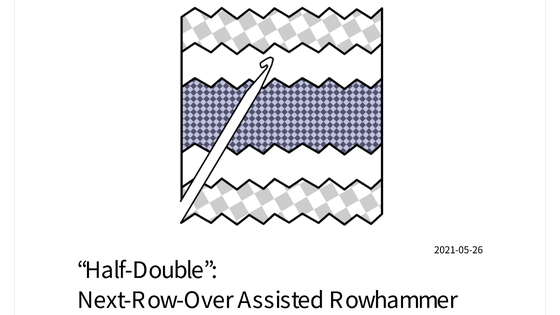
In the conventional 'Rowhammer', when a specific address of DRAM is repeatedly accessed ('Aggressor' in the figure below), bit inversion is detected in two adjacent rows ('Victim' in the figure).
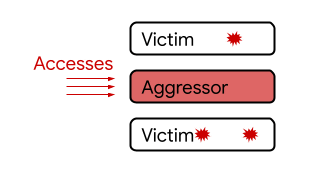
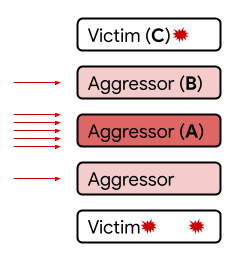
However, it has been confirmed that the newly discovered 'Half-Double' jumps over adjacent rows and propagates bit inversion.
According to the experimental results, when a large number of accesses were concentrated on 'Aggressor (A)', some of them were connected to 'Victim (C)' via 'Aggressor (B)'. 'Half-Double' is a characteristic peculiar to a silicon substrate, and it is thought that the propagation distance increases as the cell shape becomes smaller.
Google has worked with JEDEC, a semiconductor engineering industry group, and other industry partners to explore 'Rowhammer' countermeasures and solutions. The information disclosure is intended to invite all stakeholders to participate in the project in order to develop more practical and effective solutions.
Related Posts: