Techniques are devised for dynamically camouflaging semiconductor chips to prevent intellectual property theft and malicious code inclusion
In recent years, semiconductor chip makers are handling only the design, fabrication is outsourced to foundries (fabs), fabrication is mainstream. As a result, when companies outside the company manufacture chips, serious damage such as intellectual property (IP) being stolen or malicious person being tampered with in the chip may occur. In order to prevent such a crisis, a technique of applying "dynamic camouflage" to the semiconductor from the design stage has been devised.
[1811.06012] Opening the Doors to Dynamic Camouflaging: Harnessing the Power of Polymorphic Devices
https://arxiv.org/abs/1811.06012
A dynamic camouflaging approach to prevent intellectual property theft
https://techxplore.com/news/2018-11-dynamic-camouflaging-approach-intellectual-property.html
Due to the globalization of the IC supply chain, various processes are outsourced for semiconductor chip manufacturing. For example, IC chips designed in one country are outsourced to foundries in another country, manufactured in a manufacturing factory in another country, tested in another place and packaged, and the like Because companies participate in semiconductor chip manufacturing, the security risks are multilayered and the measures are complicated.
Semiconductor manufacturers have made efficiency and risk hedging by making it fabless, but instead of stealing IP of semiconductor design, mass production of the same chip without permission, or "Trojan horse" on hardware It is necessary to face the risk that would have never occurred if it was handled by the company itself.
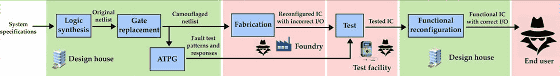
Detecting is relatively easy if it is hardware tampering like Bloomberg's report that "China and a computer adopted by Amazon embed malicious chip for data theft purpose", but IP theft and malware It is difficult for the tip supplier to see or prevent contamination etc from occurring. Therefore, methods are being studied that make it practically impossible for IP outflow and malware contamination by dynamically converting semiconductors at the design stage.
The research team of Nick Hill Rangalaghan of New York University developed a method called "dynamic camouflaging" which makes a part of a semiconductor circuit into a black box at the design stage to make the structure reverse engineer impossible doing. An attempt to prevent reverse engineering (static camouflaging: static camouflage) has already been introduced by applying camouflage as part of the design, but it is required to trust the foundry to the last. Static camouflage will not work if there is a malicious person inside the foundry. Therefore, we should apply more dynamic camouflage.
In dynamic camouflage, the chip is designed so that the circuit can be switched afterwards. Specifically, the chip manufactured according to the design does not function as it is, and the chip manufacturer will be able to generate the intended function for the first time by exchanging the circuit of the semiconductor chip afterwards.
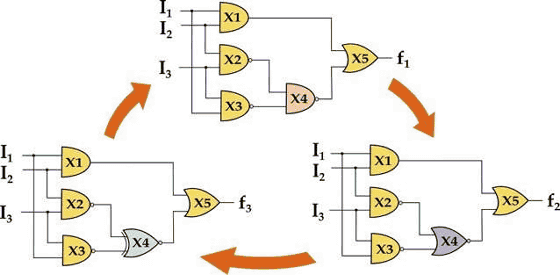
The circuit of the chip with dynamic camouflage does not function as it is because the logic gate is black boxed. Thanks to that, there is no risk that the circuit IP will be stolen or flowed across without permission. Also, since the foundry itself, which undertakes manufacturing, can not completely grasp the design of the chip, it is no longer necessary to "trust the foundry".
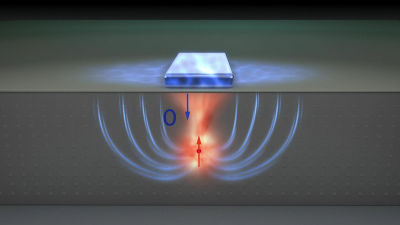
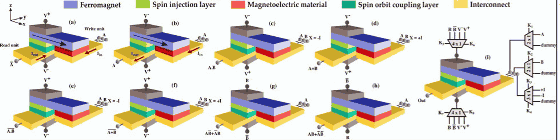
Mr. Ranggaraghan and colleagues reported that by using spin orbital interaction (MESO) using magnetic force, by having a circuit with properties that can be reconfigured posteriorly with polymorphism / multifunction, a chip incorporating dynamic camouflage We have succeeded in trial making.
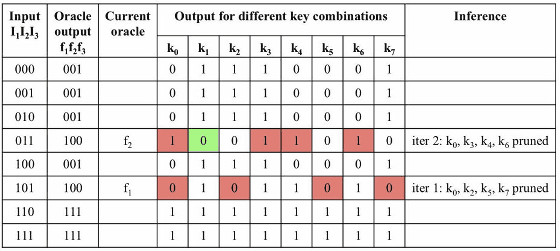
For Boardan satisfiability attacks (Boolean algebra feasibility attack) test including SAT and AppSAT preferred by end users on the chip with dynamic camouflage, it is easy to generate a wrong key , It seems that it has been confirmed that reverse engineering becomes difficult.
According to Mr. Rangalaghan, the prototype is not based on charge-based semiconductors but is based on spin-based characteristics and can not be realized with existing CMOS technology. However, the general concept of dynamic camouflage is a characteristic that can be implemented in other devices, and it is expected that a chip that can prevent IP theft in the future including a hybrid chip that integrates CMOS technology and spintronics will be realized It has been.
Related Posts: