A server expert explains why the article 'suspicion of cyber attack by Chinese spy chip' is wrong

Bloomberg Businessweek's article reporting the possibility that "the Chinese People's Liberation Army made a spy chip on the motherboard made by Supermicro" has become a big topic due to the scale size and the strangeness of the cyber attack method. Companies that appeared in articles such as Supermicro, Apple and Amazon deny "nothing in fact" as a whole, while Bloomberg as opposed to "super confidence" is a situation that does not give way to each other, but professionals familiar with server technology It is evaluated that "Technically impossible, credibility is a big question".
Investigating Implausible Bloomberg Supermicro Stories
https://www.servethehome.com/investigating-implausible-bloomberg-supermicro-stories/
You can find out about spy chip articles by Bloomberg by looking at the following article.
Bloomberg reports that the Apple & Amazon server was set up a chip to steal data to the Chinese People's Liberation Army's active force, Apple · Amazon completely denied - GIGAZINE

Patyk Kennedy of Serve The Home (STH), a server information site that had been criticizing as "technically very doubtful" from the stage when the spy chip article came out, introduced Bloomberg's Supermicro article as technology We have posted a long article to verify in detail. Since the content contains highly experts on server technology, in an article with an annotation that assumes that you have certain knowledge, the content of the spy chip article is credible due to technical reasons I conclude that it is not.
First of all, "There is no point in the part that" this terminal (spy chip) communicates with computers on the net "starting with" spelling tip article "telling the device ......" Kennedy says. Not to mention industry people, of course, those reading STH articles on " Baseboard Management Controller (BMC)" should know immediately that it is incorrect.
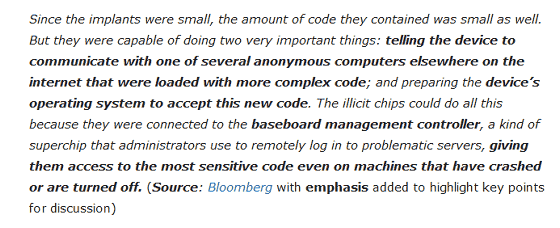
Mr. Kennedy says, "If you think about how BMC is networked even for people without specialized knowledge, you will find that the errors in the above description are obvious." Even organizations with a small number of servers to operate, it is generally said that the BMC network is separated and separated.
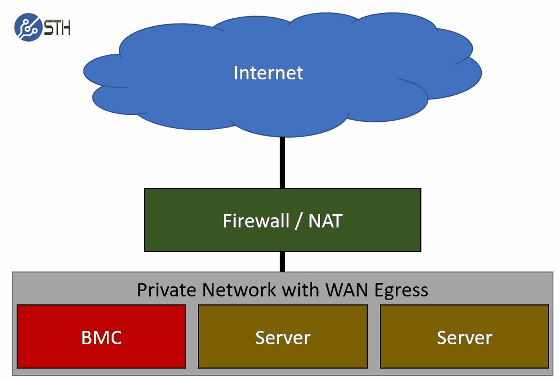
In the case of a company operating a large-scale server, BMC has been separated in a more sophisticated manner, and he is armed with excellent protection function. Mr. Kennedy says that the attack content that is impossible is described against the "30 largest US companies" mentioned in the spy chip article.
Next, the description of the "baseboard management controller ......" in the spy chip article states that even if the server is powered off, it can access highly confidential code, but this is also a mistake. Certainly BMC can turn off the server from a remote location, but confidential data on the system is not in BMC but in main server group. Mr. Kennedy points out that Bloomberg's description is technically incorrect as the server with confidential code is powered off because storage is not powered and inaccessible.

Secondly, the mistake on the part Bloomberg called "CPU hack" in the article has also been pointed out.
Spuermicro's motherboard 'X10 DRI' featured in the spy tip article is an LGA2011 Intel chip loaded model. In other words, the motherboard and the CPU are connected with 2011 pins, and the RAM pins for the memory of most pins occupy. Because communication between this memory and CPU is done with a fairly fast clock, "Small chips have no room to attack this communication."
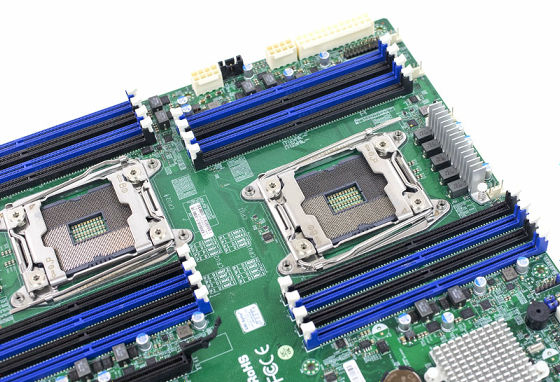
Even assuming that Bloomberg's report wrote "BMC" in this context incorrectly as "CPU", BMC RAM is temporary memory and it is troublesome in another aspect. Kennedy points out that for chips of size Bloomeberg depicts over and over, there are not enough pins to monitor memory for the purpose of injecting code. Even if we have aside as to whether we can have processor power corresponding to pins that can communicate at high speed, the number of physical pins is overwhelmingly short.
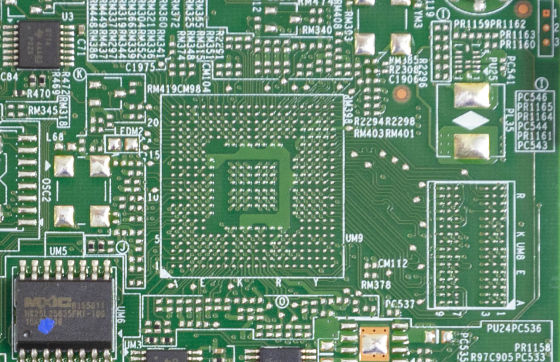
And Kennedy felt suspicious that there are many discussions on the accuracy of the chip in the spy chip article but not the actual chip picture. Mr. Kennedy thinks that it is strange that no one source of information that seems to have 17 people holds pictures of the real thing in this era, with cameras in every and all places, including smartphone cameras.
Bloomberg issued a small chip as an image image in a spy chip article, but said, "General people who are unfamiliar with technology seems to be afraid of small chips," said Kennedy noted that the image image was effective doing. However, with respect to such a small chip, "electronic equipment does not move without power supply" and "no additional parts such as capacitors and resistors are mentioned" "In order to keep internal data even for long periods of power off, nonvolatile It should be required for small chips, such as sex memory and controller ".

In addition, Bloomberg says the chip also has networking capabilities. However, because of the requirement of large die space for network MAC and data transmission / reception using 4 wire pairs at low speed 1 GbE standard, it is difficult to wire without changing the design change to PCB, Kennedy thinks that there is a big question in the network function because there is a risk that a communication interception attempt will be detected soon.
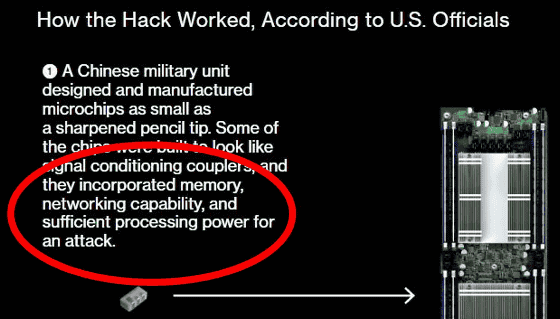
Then, if there is a "small chip" with the ability to divide between CPU and memory, hold code, have network function, there is a question of "How did you manufacture it?" If you could have Bloomberg 's stated capability with small chips, fabrication would require surprisingly fine lithography technology and as of 2014 it was possible for the four major companies of TSMC, Intel, Samsung and Global Foundaries .
China is advancing innovation through the "Made in China 2025" program, but there should have been no technical level to make the chips required as of 2014. In addition, the cutting-edge production line is allocated for the production of expensive chips such as smart phones, PCs, servers, etc. In small-volume production, it is necessary to use process nodes of the old generation, making high-performance small chips Mr. Kennedy thinks that it is a rather difficult task.
The rough people who appeared as sources of information in the spy chip article are six present and past national security officials, three Apple internal stakeholders, six former Supermicro employees, both of which are anonymous It is a state where it is impossible to externally verify to confirm the authenticity of information. If Bloomberg does not bend the claim that "the content of the spy chip article is fact", Bloomberg himself should present information to indicate "plausibly" what happened by the spy chip itself, If it can not be done, it is necessary to withdraw the article and investigate how the article was produced, and obviously it should compensate for the damages given to Amazon, Apple and Supermicro companies, Kennedy said.
Related Posts: