Microsoft turns out to have accidentally signed a rootkit by exploiting a weakness in the code signing process

Security company G DATA has detected a driver called 'Netfilter' with Microsoft's digital signature as malware. The alert system pointed out the possibility of false positives, but the verification revealed that it was positive (actually malware), so Microsoft has set out to investigate.
Investigating and Mitigating Malicious Drivers – Microsoft Security Response Center
https://msrc-blog.microsoft.com/2021/06/25/investigating-and-mitigating-malicious-drivers/
Microsoft signed a malicious Netfilter rootkit | G DATA
https://www.gdatasoftware.com/blog/microsoft-signed-a-malicious-netfilter-rootkit
Microsoft admits to signing rootkit malware in supply-chain fiasco
https://www.bleepingcomputer.com/news/security/microsoft-admits-to-signing-rootkit-malware-in-supply-chain-fiasco/
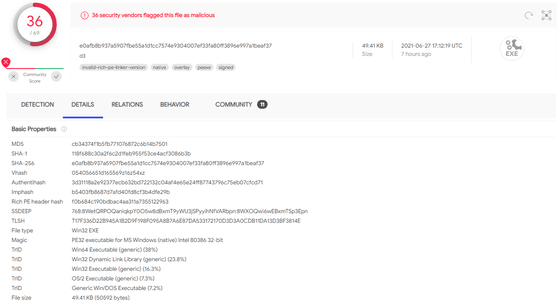
In 'Virustotal,' which publishes test results from multiple antivirus software, the file was flagged as a 'malicious file' by 36 out of 69 security vendors. The page for that file on Virustotal has already been deleted.
According to Microsoft, there is no evidence that the WHCP signing certificate has been published and there is no danger to the signing infrastructure.
News site Bleeping Computer reports that it may be due to a threat actor who, following Microsoft's process, sent a malicious Netfilter driver and successfully successfully obtained a binary that Microsoft digitally signed. I have.
Signed binaries can be exploited by advanced threat actors to carry out large-scale software supply chain attacks.
The attackers are mainly targeting the Chinese game sector, and so far there are no signs that companies have been affected.
Related Posts: