CCleaner's official file has been tampered with and downloaded and distributed with malware

System cleaner software that can delete data such as unnecessary registry items and temporary files in PCCCleaner"It became clear that the executable file containing malware was distributed on the regular download server. CCleaner's developer, Piriform, asks users to download and install CCleaner in the last month, promptly update to the latest version.
Cisco's Talos Intelligence Group Blog: CCleanup: A Vast Number of Machines at Risk
http://blog.talosintelligence.com/2017/09/avast-distributes-malware.html
Warning: CCleaner Hacked to Distribute Malware; Over 2.3 Million Users Infected
http://thehackernews.com/2017/09/ccleaner-hacked-malware.html
When September 13, 2017 the Cisco Talos security researchers are testing the new attack detection system, I found a file to launch the advanced malware system in the CCleaner exe file. Talos researchers declared that the CCleaner executable containing this malware was distributed on an authorized download server, so there was a so-called "supply chain attack" against the distributor Piriform.
The 32-bit versions of "CCleaner v 5.33.6162" and "CCleaner Cloud v 1.07.3191" were found to contain malware. It was distributed from August 15, 2017 to September 12, 2017.
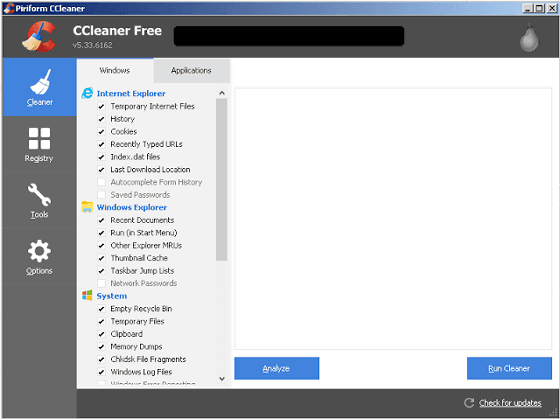
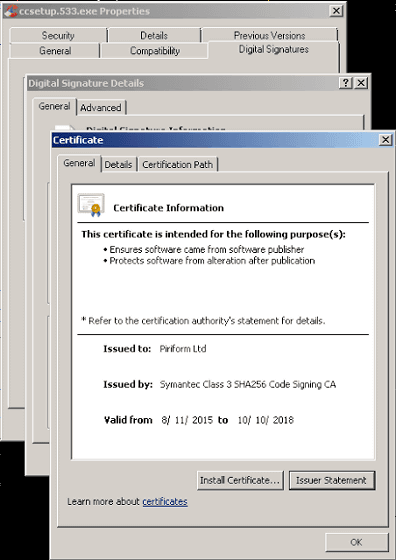
According to Talos, CCleaner with malware had a valid digital signature by Symantec issued Piriform.
The malware installed in the CCleaner has data such as "computer name", "installed software list", "running process list", "IP address and MAC address", "whether the process is executed with administrator authority" Collect and send to external server.
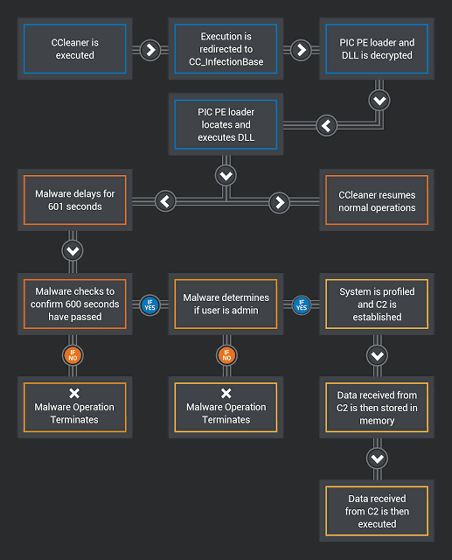
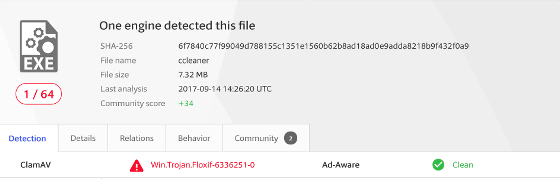
When Talos told CCleaner malware contamination in the blog, malware detection rate with security countermeasure software was very low state.
And on September 18, 2017 on the local date and time, CCleaner 's developer Piriform officially announced that the data was altered and files were distributed with malware mixed.
Piriform - Security Notification for CCleaner v5.33.6162 and CCleaner Cloud v1.07.3191 for 32 bit Windows users
http://www.piriform.com/news/release-announcements/2017/9/18/security-notification-for-ccleaner-v5336162-and-ccleaner-cloud-v1073191-for-32-bit-windows-users
Piriform grasped CCleaner's malware contamination on September 12, 2017. It is said that Avast, a security company, Parent acquiring Piriform, was tracking the malware contamination.
According to Piriform there are 2.27 million users who use CCleaner of the affected version. Distribution of the new version of "CCleaner v5.34" has already begun, so users using the 32-bit version of CCleaner v5.33 are prompting to update to v5.34 promptly. Please note that CCleaner Cloud v1.07.3191 has already been updated so users do not need to do anything special.
According to Piriform, the malware sent by the malware is low confidential data as mentioned above, there is no indication that other data has been sent to the server. Piriform stopped the corresponding server on September 15, 2017, and who collaborated with law enforcement agencies in the United States to incorporate malware, and how the data was tampered with in what circumstances I am under investigation.
Piriform has said that it was halted before the damage expanded, "Although users responded quickly to rapid malware contamination problems, there was no harm to the user," Piriform distributed malicious executable files for about a month It is a fact that there is a possibility that the damage has expanded further if luck is bad. In addition to the current CCleaner issue, examples of MEDoc's servers, etc. that served to spread NotPetya's spread by distributing files containing malware "NotPetya", a major epidemic in June 2017, It shows the power of supply chain attack that uses trust relationship.
· Continued
CCleaner's malware contamination problem turned out to be a targeted attack targeting large companies such as Intel, Sony and Microsoft - GIGAZINE

Related Posts: