Code tampering that infects Ransomware to those who saw sites running on WordPress is secondary

ByLinus Bohman
An advertisement that infects the virus is displayed by merely browsing the website, the file in the PC is encrypted, and if you want to take the encryption to the hostage and want it back to the original, the Ransomware that threatens to pay the money is raging It is. Among them, content management system (CMS)WordPressIt seems that websites that used to be hacked across the board and are being victimized by Ransomware.
Massive Admedia / Adverting iFrame Infection - Sucuri Blog
https://blog.sucuri.net/2016/02/massive-admedia-iframe-javascript-infection.html
Nuclear EK Leveraged In Large WordPress Compromise Campaign | Malwarebytes Unpacked
https://blog.malwarebytes.org/exploits-2/2016/02/nuclear-ek-leveraged-in-large-wordpress-compromise-campaign/
Security Alert: Ransomware Delivered by Hundreds of Compromised Wordpress Websites - Heimdal Security Blog
https://heimdalsecurity.com/blog/compromised-websites-ransomware/
Mysterious spike in WordPress hacks silently delivers ransomware to visitors | Ars Technica
http://arstechnica.com/security/2016/02/mysterious-spike-in-wordpress-hacks-silently-delivers-ransomware-to-visitors/
Security countermeasures companySucuriHas revealed the fact that web pages built using WordPress have been tampered with invalid code. The tampered web page is loaded with code at the end of the JavaScript file, and an Exploit Kit (for detecting vulnerabilities on the PCExploit kitIt is said that it is embedded.
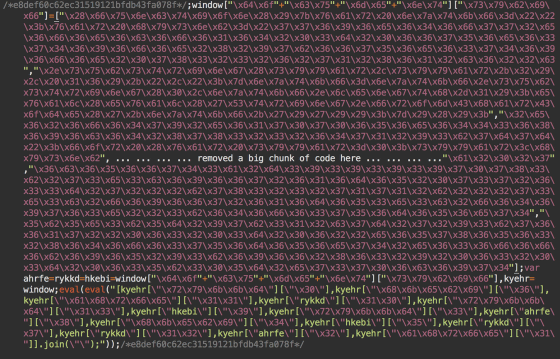
As a result, when a user using an old version of Adobe Flash Player, Adobe Reader, Internet Explorer, etc. browses a Web page that has been tampered with, vulnerabilities are found, infected with Ransomware, and the file is encrypted .
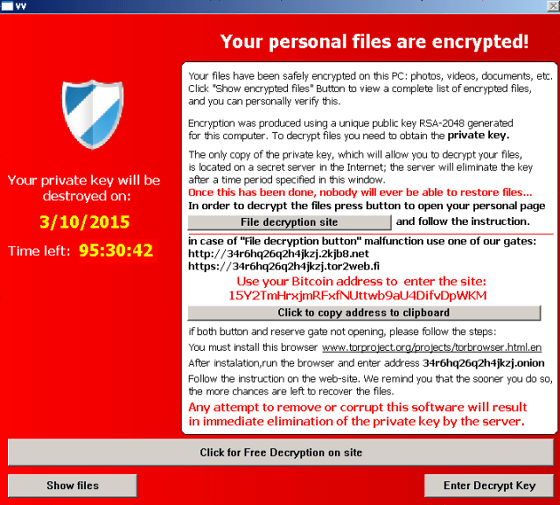
It is also clear that the Exploit Kit is evolving, and it has been discovered that it infects only when visiting the site for the first time, and one that uses the payload individually to prevent attacks from being detected It is said that.
Random wear attacks targeting sites that use such WordPress are rapidly increasing since the second half of 2015,The British major news site "The Independent" was tampered with and was under attack by guiding the viewer to a site infected with RansomwareIt is obvious that the damage has increased.
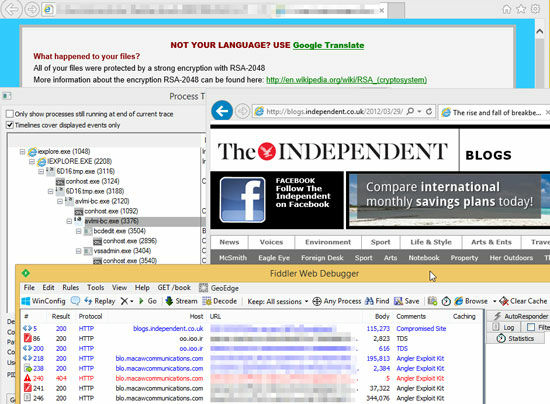
Although it is not clear yet why the damage caused by sites using WordPress continues in success, it is pointed out that there is a possibility that it is broken by an unknown vulnerability of WordPess plug-in. "Malware is trying to infect all accessible js files, as Sucuri said," If you host multiple domains with the same hosting account, the malicious site If there is even one, the rest of the site will be all affected by malware, "he says that it is necessary to update all the WordPress sites it manages to the latest version all at once.
Until now, damage caused by Ransomware was mainly caused by underground sites such as pornographic sites, but since the damage this time has occurred in a very general site built with WordPress, it is no longer a "dubious page Even if it does not open it is okay ", it seems that it is getting in a condition that can not be said.
Related Posts: