The ransom request Ransomware developer is releasing a rainless decryption key, turning over from attack and going down

ByIntel Free Press
Ransomware wishing to ransom instead of decrypting encrypted game save data and user profile "TeslaCrypt"Was discovered in March 2015 and players of prominent games such as" Call of Duty "" Star Craft 2 "" Diablo "were targeted, but the developers of Tesla Crypt released the decryption key, A decryption tool was released by ESET handling security related products.
TeslaCrypt shuts down and Releases Master Decryption Key
http://www.bleepingcomputer.com/news/security/teslacrypt-shuts-down-and-releases-master-decryption-key/
ESET Releases Decryptor for Recent Variants of Tesla Crypt Ransomware
http://www.eset.co.uk/Press-Centre/News/Article/ESET-Releases-Decryptor-for-Recent-Variants-of-TeslaCrypt-Ransomware
TeslaCrypt is a Randamuwaitu which requests money to encrypt and release the related data of the game saved in the PC when infected with the user's PC and details of the mechanism can be confirmed from the following article.
Malware that requests ransom to hostage game data is discovered - GIGAZINE

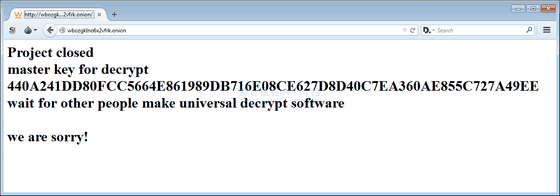
A security researcher at ESET noticed that the developer of Tesla Crypt is about to gradually terminate the same Ransomware after 2016, and from the support chat of the site used for paying ransom anonymously "decryption I want you to release the master key. " The developer of Tesla Crypt took the investigator 's request and really released the master key for decryption. The following image is a screenshot of the site for paying ransom and you can see that "we are sorry!" Is written with the decryption master key.
In response to the release of the decryption key, ESET has released software to decrypt files encrypted by TeslaCrypt. Using a public decryption tool, you can decrypt files with the extension ".xxx" ".ttt" ". Micro" ".mp3" encrypted by TeslaCrypt, or files without extensions is.
Decryptor for Tesla Crypt Ransomware
http://download.eset.com/special/ESETTeslaCryptDecryptor.exe
Open the above URL and click "Save file".
Move the downloaded file to the desktop.

From the start menu, go to "All Programs", "Accessories", right click on "Command Prompt" and click "Run as administrator (A)".

When the command prompt opens, enter "cd% userprofile% \ Desktop" and press "Enter". Be careful not to enter the actual user name in "userprofile" part.

Type "ESETTeslaCryptDecryptor.exe" and press "Enter".

Click "Agree".

You can now use the ESET decryption tool.

To search if the encrypted file is on the C drive, enter "ESETTeslaCryptDecryptor.exe C:" and press "Enter". If you want to search other drives, change "C:" is OK.

When "Looking for infected files ..." is displayed, searching for encrypted files is in progress.

Fortunately, encrypted files were not found. If an encrypted file is found, you can decrypt it according to the command prompt screen.

Related Posts: