North Korea's state-run news agency "Chuo Chuo Tsushin" proved to be charging malware on official website
North Korea's official news site "North Korea Central News AgencyIt was revealed that dropper type malware installed secretly in the viewer's PC was loaded on the above.
Surprise! North Korea's official news site delivers malware, too | Ars Technica
http://arstechnica.com/security/2015/01/surprise-north-koreas-official-news-site-delivers-malware-too/
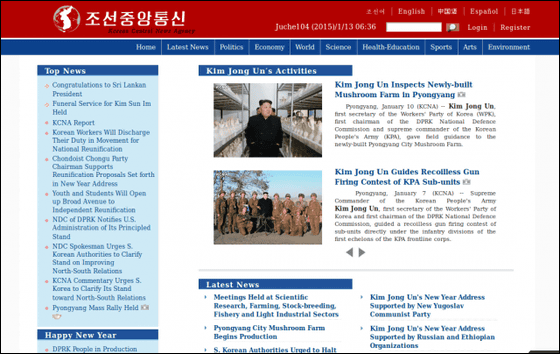
"Korean Central News Agency" is a state-run telecommunications company in North Korea and is the country's largest news organization. The official website was opened in 2010, and it delivers various news for domestic and overseas, and the design of the webpage looks like this.
Ars Technica found the data "FlashPlayer 10. Zip" in the red frame part on the source code of Chosun Central News Agency. When I decoded this file and JavaScript code independently, it turned out that this was malware instead of just a installer.
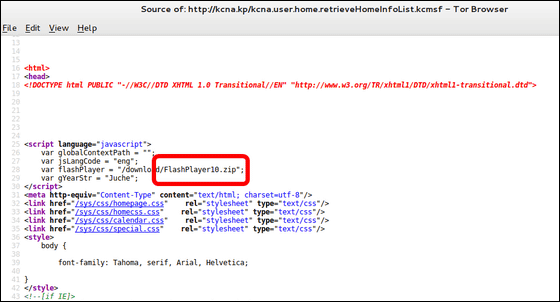
This file is set as a JavaScript variable "FlashPlayer" on the main page of the Chosun Chuo Tsunami's website and other pages, and it can also be installed in installers such as "Flash Player 10" and "ActiveX control" that can run on Windows He seems to have been disguised.
Although the file name is different, the contents are the same in every file, and this is called the online scan serviceVirusTotalWhen I scanned it, it turned out that it was a dropper type malware installed secretly in the user's PC. I checked the time stamp of "FlashPlayer 10. Zip", and it seems that the creation date was in December of 2012.
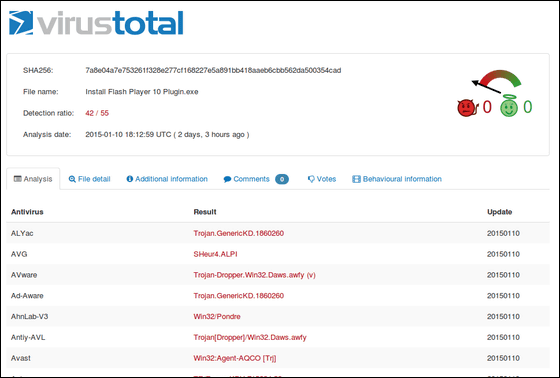
The malware that is put in the North Korean Central News Agency targeted someone who wanted to periodically check the trends of North Korea and Kim Rae'sWater fountain type attackIt is thought that it is not.
Related Posts:
in Note, Posted by logu_ii