Attack that replaces application installed on iPhone and iPad with malware Attack "Masque Attack" appears
Attack that replaces third-party applications (other than genuine Apple apps) installed on iOS 7.1.1 or later iOS devices with malicious malwareMasque AttackThe existence of "Internet security research firm"FireEyeIt was discovered by.
Masque Attack: All Your iOS Apps Belong to Us | FireEye Blog
http://www.fireeye.com/blog/technical/cyber-exploits/2014/11/masque-attack-all-your-ios-apps-belong-to-us.html
'Masque attack': Do not panic but do pay attention | iMore
http://www.imore.com/masque-attack
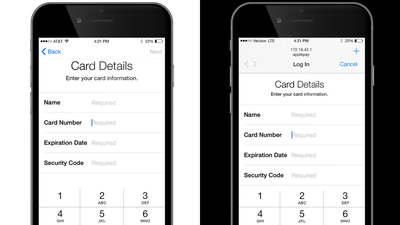
"Masque Attack (Attack Impersonation)" is trying to install a new application by pasting a link to a text message or e-mail and letting it follow the user. If you follow this link, the application will be installed without going through the App Store, the legitimate third party application installed in the terminal will be replaced with a fake application, and various information in the terminal will be extracted via this application That means that.
The following movies demonstrate how it would actually take "Masque Attack". Personal information has been pulled out during that period, and since the fake application is operating in the same way as a normal application, it is already unnoticed that the fake application has already been installed, and as usual the application It seems to use.
IOS Masque Attack Demo - YouTube
The demo screen looks something like this. "Masque Attack" is done to the iPhone displayed on the far right, and the two browser screens next to it are used to check the information extracted from the iPhone.
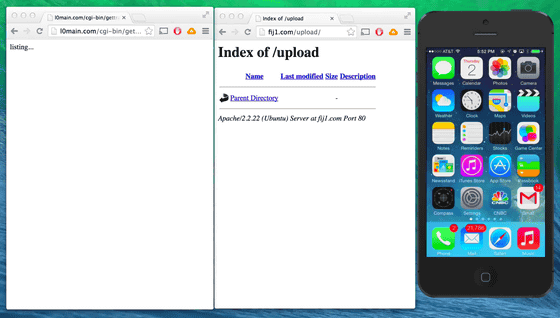
First of all, check the operation of the application. You can see that the regular Gmail application works well on the iPhone.
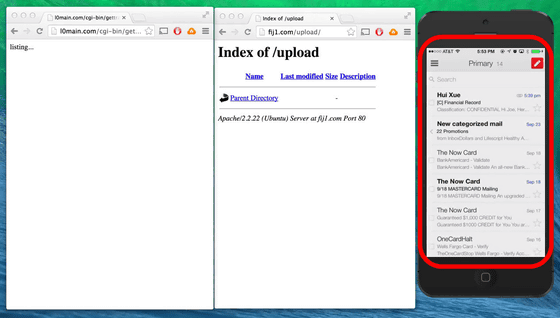
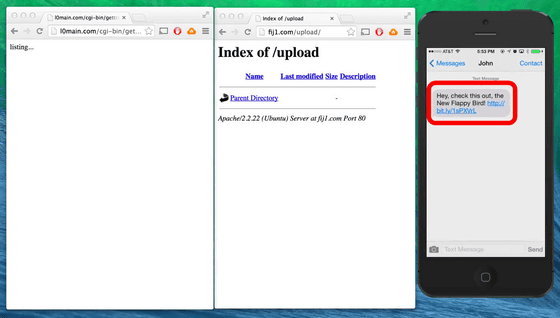
So here is the demonstration of "Masque Attack" demo. In "Masque Attack" you can send this URL via email or SMS. In this case, a link is sent to both the rough sentences that the user casually seems to have accessed the URL, such as "Please check out since the new Flappy Bird! Comes out!"
Link destination is absolutely Flappy Bird! On the screen like "Are you installing a new Flappy Bird!?" On the screen, if you press the "Install" button on this screen ... ...
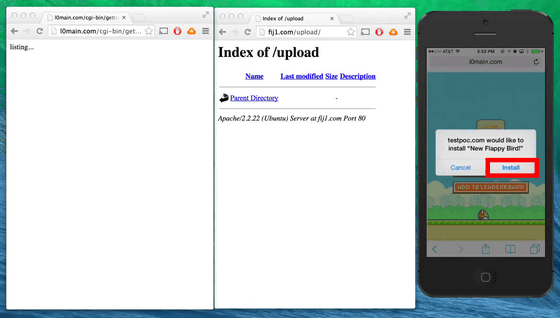
Somehow Gmail will be in the middle of updating. It is exactly at this moment that the regular application is replaced by a false app, but it seems that any application made by a third party can replace the application with "Masque Attack", so it is not necessarily said that the Gmail application will be replaced with a fake application It does not mean.
I opened a suddenly updated Gmail application (fake application) ......
It looks like you can normally use it as Gmail. However, if you look closely well, the address bar is displayed at the top of the screen, and it looks just like accessing the browser version of Gmail. Also note that when opening this fake Gmail application, a mysterious file "0000000000000001.db" appears in the center of the screen.
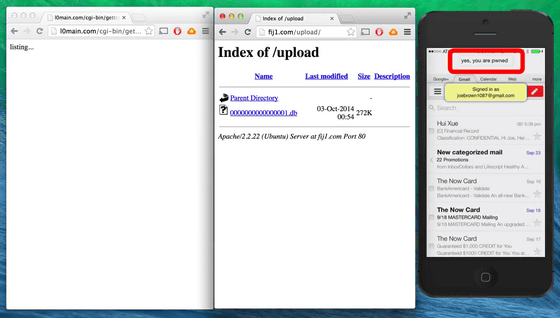
Try downloading this "0000000000000001.db" file that appeared as soon as the user opened a fake application.
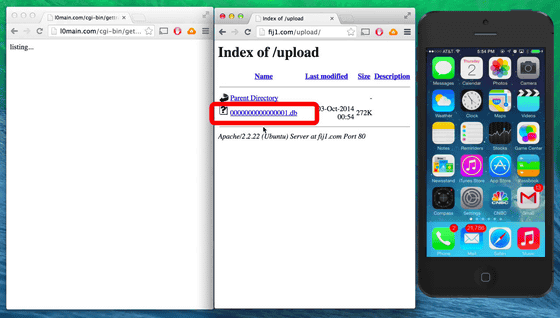
The contents of the file seems to be filled like this with various data as follows.
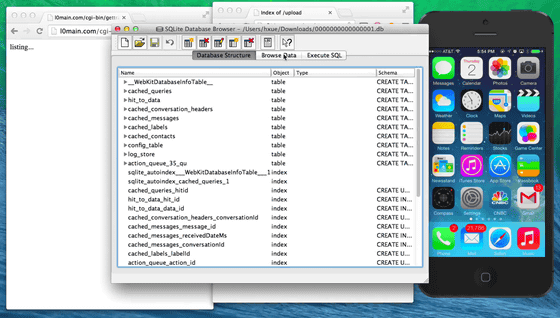
This is because all the personal information is stolen easily in such a record, etc. concerning the financial transaction that the user has done so far.
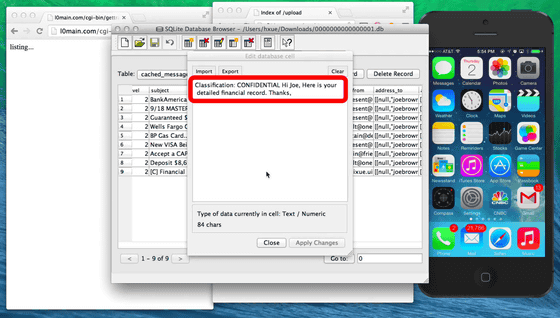
In addition, contents of e-mail, SMS, calls and so on can easily go through the condition like this.
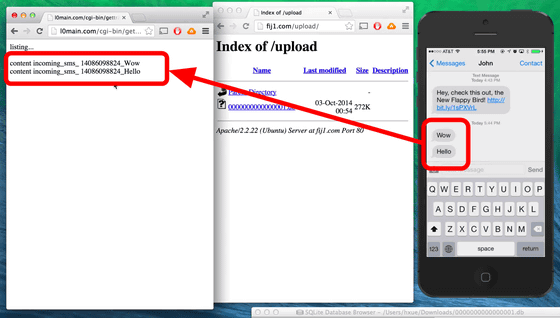
The reason why "Masque Attack" can install a fake application without going through the App Store is because the company distributes the application to employees without going through the App Store, called "Enterprise Provisioning Profiles" This is because we will replace the application using the technique. Also, since the fake application uses the same bundle ID as the regular application, it seems to be very difficult to detect this.
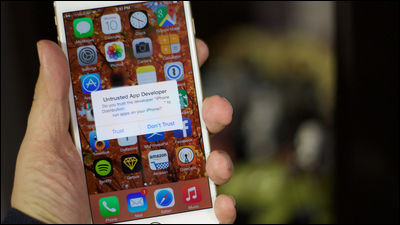
Security investigation company FireEye does not install third party applications from outside the App Store, does not press the "install" button pop-up displayed on the web page, when a warning "untrusted application developer" is displayed I instantly uninstall without installing an application, etc. are cited as a countermeasure to "Masque Attack".
Related Posts: