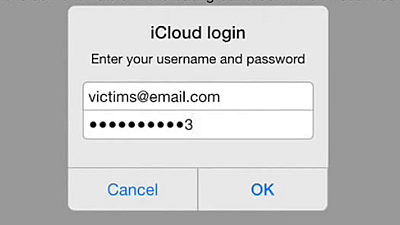
"IMessage" which should not be deciphered is actually decipherable and it turns out that ID and password can also be read
It was exposed by Mr. Edward SnowdenNSA's spy actIn the case, Apple found that iMessage and FaceTime were actually decipherable by Apple itself, which was said to be "the communication is encrypted, so it is impossible for third parties including Apple to know the communication contents" did. In addition, the third party intercepting the communication also involves the risk of enabling MITM attacks (man-in-the-middle attacks), and Apple's previous declaration "For the communication of iMessage and FaceTime" · Because "Encryption" is done, it is incompatible with the explanation that it is impossible to see contents except recipients and senders ".
IMessage Privacy
http://blog.quarkslab.com/imessage-privacy.html
IMessage_privacy.pdf(PDF file: about 8 MB)
http://blog.quarkslab.com/static/resources/2013-10-17_imessage-privacy/slides/iMessage_privacy.pdf
In the report, while admitting the high level of safety as "Apple's communications pass through the SSL tunnel", operate the public keyMan-in-the-middle attackWhen I tried, I heard that he succeeded. This means that no pinning (pinning) of the public key has been done. Then, when I created a forged CA (Certification Authority), it was easy to decrypt the encryption.
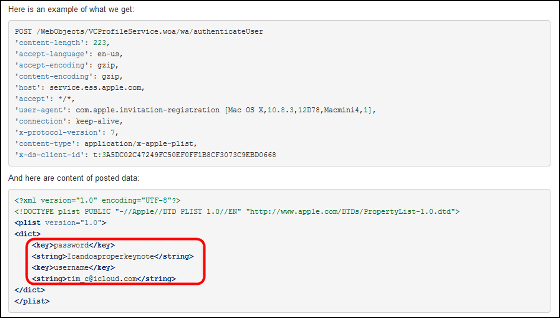
I was surprised more than that while I was in SSL communication, I could see the AppleID and password. In other words, it became clear that the data was sent with unencrypted plaintext. Although it is unlikely that Apple will acquire that information and divert it to others, using this method makes it possible for a third party to obtain another's ID and password.
The following is the data at that time. You can see that the password and user ID are displayed.
◆ MITM attack (man-in-the-middle attack)
The fact that the public key is not pinned and the situation where the ID and password are sent in text means that it will become a foothold for the MITM attack.
· One-side MITM attack
It is an attack that tampering communication contents by impersonating as either a sender or a recipient of a message. Hackers are on the leftDhillonI hid in between Apple's server and rewritten the message "Hey! (Hey!)" Sent by Dhillon as "Hey my love! (Hey honey!)" And received itBelindaAn example of how confused "!?" Is cited is given as an example.
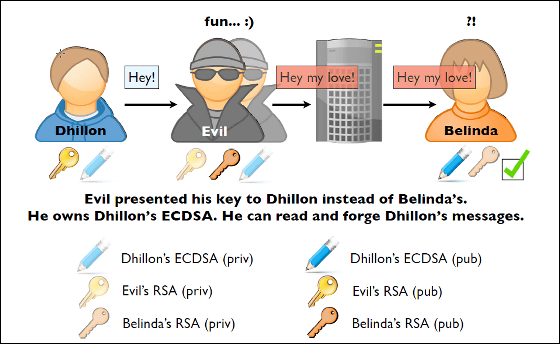
The same applies to the reverse flow, the hacker rewrites the message "What?" That Belinda replied as "<3 (Heart)" and delivers it to Dhillon, which can confuse the relationship between the two is.
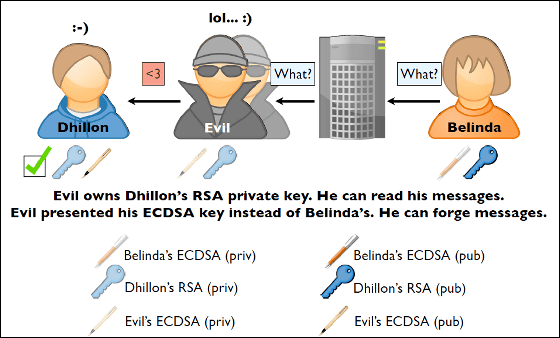
In this example light tame is introduced, but in fact it leads to more serious tampering.
· Both side MITM attacks
As shown in the example below, it is possible to impersonate both parties and tamper with communication.

· Bypass Apple
Furthermore, it is possible to send messages without going through Apple servers.

The conclusion
This report revealed that "in fact Apple has a way to intercept iMessage and FaceTime communications" and does not mention whether Apple actually intercepted it. On top of that, actually it is unrealistic for average hackers to conduct man-in-the-middle attacks on the iMessage communication network as mentioned above, and ordinary users say that there is no problem even if you continue to use iMessage Although it is not suitable for communication with content that you do not want to see by government agencies. In addition, Apple also stated that it should formulate a more transparent PKI (public key infrastructure) and release the protocol.
Related Posts: