A security researcher claims that Chinese authorities actually warned Apple in early 2019 about a vulnerability in AirDrop that was allegedly used to identify users.

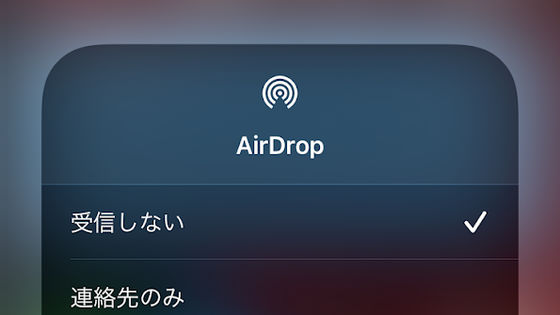
Chinese law enforcement authorities have announced that they have succeeded in breaking the encryption of AirDrop, a function that allows files such as images and videos to be exchanged between iPhones and Macs, and identifying users' personal information. The vulnerability that made it possible to break through this encryption was already discovered in 2019, and it has been pointed out that Apple's negligence made it possible for Chinese authorities to analyze it.
Attack of the week: Airdrop tracing – A Few Thoughts on Cryptographic Engineering
https://blog.cryptographyengineering.com/2024/01/11/attack-of-the-week-airdrop-tracing/
Apple AirDrop leaks user data like a sieve. Chinese authorities say they're scooping it up. | Ars Technica
https://arstechnica.com/security/2024/01/hackers-can-id-unique-apple-airdrop-users-chinese-authorities-claim-to-do-just-that/
AirDrop is a feature that allows nearby Apple devices to share files over their own wireless connection without having to connect to the Internet. This sharing feature has been used by Hong Kong democracy activists, and the Chinese government has reportedly cracked down on it in response.
Chinese authorities announce that they have successfully broken AirDrop's encryption and identified the person communicating with them, and also release screenshots of analysis tools - GIGAZINE
'Apple's response to this situation is extremely important,' said Benjamin Ismail of Greatfire.org, a group that monitors Chinese internet censorship. We should work to ensure the security of AirDrop.'
The vulnerability in AirDrop that allowed analysis by Chinese authorities was discovered in 2019 by a research team at Germany's Darmstadt University of Technology.
Essentially, AirDrop transfers data such as device name, email address, and phone number as part of identifying information between Apple devices. Normally, this information is encrypted to protect privacy, but since no measures were taken to mix in fake data and then scramble it, once the encryption was broken, personal information would be revealed. I'll put it away.

The research team reported their findings to Apple, but Apple did not show any signs of fixing the vulnerability. For this reason, they announced a fix for this vulnerability in 2021, but there seems to be no sign that it has been implemented.
Security researcher Ken White said: ``My reading is that what the Chinese authorities have published is almost certainly using a technique published by German researchers in 2019, four years after the discovery. Even after all this time, it appears that this design flaw has not been resolved.'
'Apple had four years to fix security holes in AirDrop that put user privacy and safety at risk,' Oregon Democratic Sen. Ron Wyden said. 'They stood by and did nothing,' he said, criticizing Apple.
Matthew Green, a cryptologist at Johns Hopkins University, said, ``If Apple had fixed this security hole in 2019 when it was reported, it would have been difficult for the Chinese authorities to analyze the code. 'Now that Chinese security agencies are exploiting this vulnerability, this becomes a tough political issue for Apple.'
Related Posts:
in Software, Posted by log1i_yk