A vulnerability is found in which a malicious application is installed without permission on an iPhone or iPad, using AirDrop
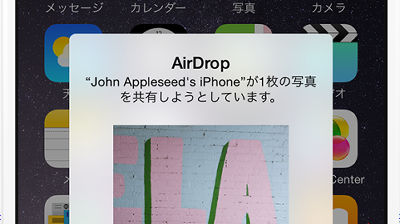
You can instantly share information with people using iOS devices around youAirDropA vulnerability has been discovered that allows you to install applications on your target device without permission and infect malware. According to Apple's survey, iOS 8 users are able toAccounting for 87%However, this vulnerability is based on iOS 8.4.1.
One Great Reason To Update To iOS 9 - A Nasty Silent AirDrop Attack Is In Town - Forbes
http://www.forbes.com/sites/thomasbrewster/2015/09/16/airdrop-ios-vulnerability/
What is the vulnerability of AirDrop? The demonstration movie is from below.
IOS 8.4.1 AirDrop Exploit Demo - YouTube
First of all, check the OS version. Tap the setting icon ......
Tap "General".
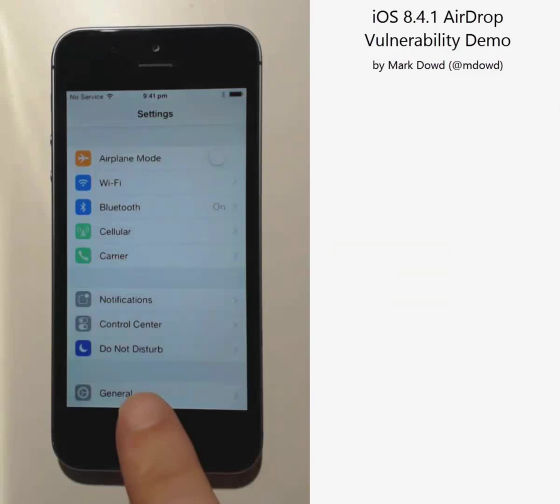
Tap "Software Update" ......
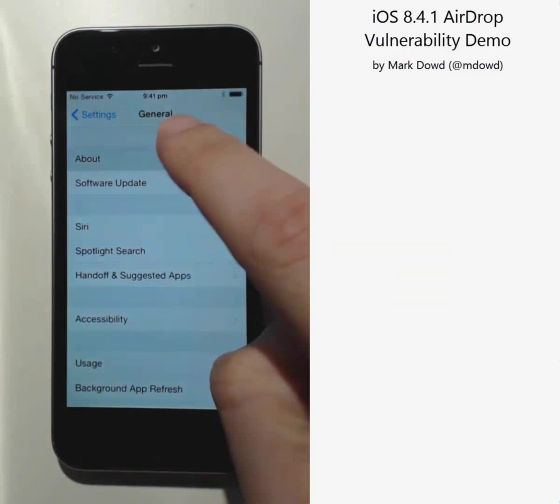
You can see that iOS 8.4.1 is installed on the terminal as follows.

You will return to the home screen.

Launch the phone application and confirm that it is working normally as usual.

I can not find any trouble even if I go back to the home screen and swipe it again.

So, after confirming that the iPhone has no problem lock the screen ... ....

I will use AirDrop from lock screen.

"Odd (off)", "Contacts Only" (contact only) "Everyone (all people)" will be displayed and you will be asked to select which people you will share the data with AirDrop.

Select "All people".

After a short time……

"" Jerk "would like to share a photo (" I want to share pictures "), so please press the power button without tapping the file ......

Turn off the power supply once.

Reboot the iPhone, unlock it and access the home screen.

It seems that there has not been any particular change.

But when I start up by tapping phone application ......

"HelloWorld (Hello world)" was displayed.

In the comments section of the movie, there is also a thing called "cool bug!", But actually the movie shows that "anyone who is within the range that AirDrop can use, anyone can put malware on the target terminal Possibility to be. This is a vulnerability discovered by the Australian security researcher Mark · Dout, and if we exploit this vulnerability it will be possible to bypass the App Store and install the application and overwrite the file. The vulnerability was discovered in iOS 8.4.1 and the vulnerability itself has not been fixed in iOS 9 released on 16th September local time, but it is impossible to use this method by improving AirDrop 's security It is becoming.
Apple mitigates but does not fully fix critical iOS Airdrop vulnerability | Ars Technica
http://arstechnica.com/security/2015/09/apple-mitigates-but-doesnt-fully-fix-critical-ios-airdrop-vulnerability/
As a precaution, someone using iOS 8.4.1 is recommended to set AirDrop not to be used in locked state. Also on Mac, upgrading to the latest version of OS X 10.11 will make it impossible to do this.
Related Posts:
in Video, Hardware, Software, Smartphone, Security, Posted by darkhorse_log