A bug that allows you to access photo data by bypassing Passcode input using the latest VoiceOver function in iOS 12.0.1
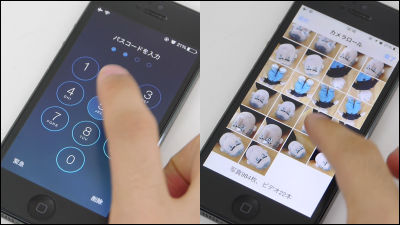
A vulnerability was found in iOS 12 that does not require a passcode to be accessed inside the terminal, but even in the latest iOS 12.0.1 it is still possible to bypass the passcode lock and use the "VoiceOver" A bug that accesses the photos inside is found and released on YouTube movie.
Passcode Bypass iOS 12 - 12.0.1 - YouTube
Using iPhone XS updated to the latest version of iOS 12.0.1, I tried to bypass Passcode Lock using the VoiceOver function and display photos inside the terminal, referring to the operation of the above movie. Since the bug itself is the one of iOS 12.0.1, there is a possibility that it is abused as well as iPhone XS.
I used VoiceOver function on iPhone XS of iOS 12.0.1 to bypass passcode lock and showed pictures - YouTube
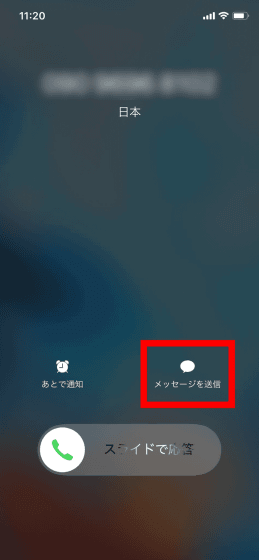
First, I will call the iPhone with passcode lock. Next, tap "Send message" without receiving incoming calls.
Tap "Custom ...".
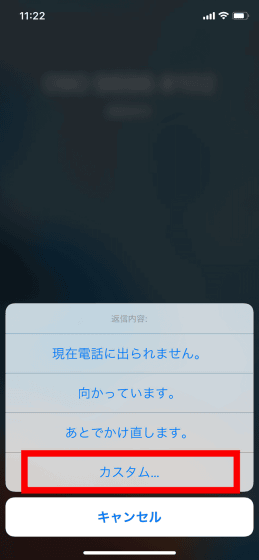
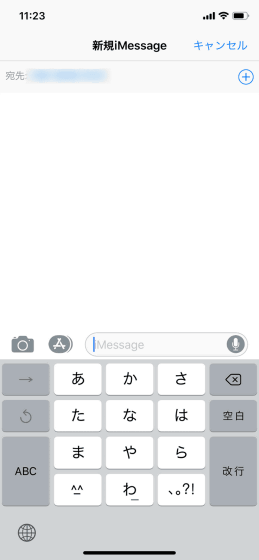
Since the new iMessage screen starts up, activate Siri by button operation.
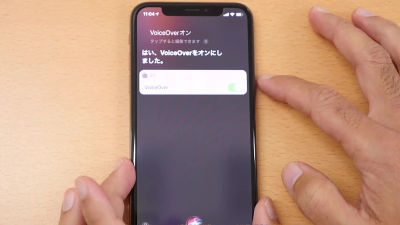
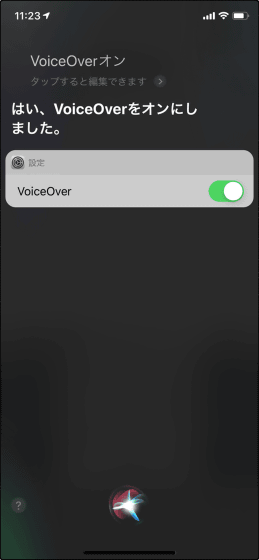
Talk to Siri and turn on the VoiceOver function, then press the Home button (side button on iPhone X series) to return to the iMessage screen again.
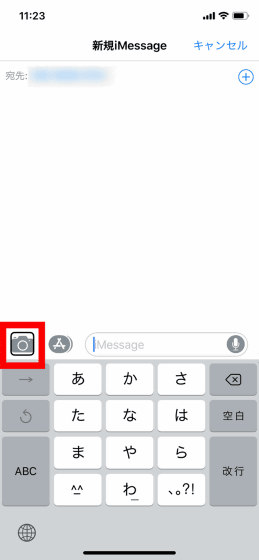
At this point, if you tap "Camera" icon and select "Double tap on screen simultaneously with starting Siri", you will enter bug mode.
The timing of double tap is severe, but if you succeed you can flick the screen to the left and right and operate the screen to start in the background. When you reach the picture you want, you can display it by tapping the screen. You can also send images.

In order to prevent bugs that access the data in the terminal without inputting the passcode using the VoiceOver function existing at the latest iOS 12.0.1 at the time of writing, it seems that there is no countermeasure only by turning off the function of Siri. A quick iOS update will be awaited by Apple to prevent this vulnerability.
Related Posts: