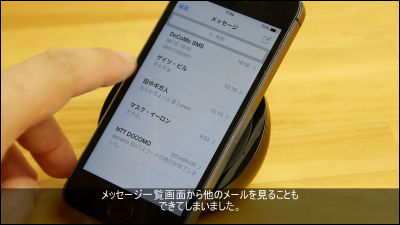
A FaceTime bug that avoids the passcode is discovered just after an iOS 12.1 release

On iOS 12.1 released on midnight on October 30, 2018 in Japan time, it was discovered that there is a FaceTime related bug that can avoid the passcode and see the entire contents of the address book. I discovered a lot of iOS related bugs so far and this time I found a new bug was found in about an hour from release.
New iPhone Passcode Bypass Found Hours After Apple Releases iOS 12.1
https://thehackernews.com/2018/10/iphone-ios-passcode-bypass.html
The security researcher, Spanish Jose Rodriguez , found the bug. FaceTime's group call feature " Group FaceTime ", which allows up to 32 people to simultaneously make video calls, was implemented from iOS 12.1, but it seems that a new bug was found in the same way. Mr. Rodriguez actually reproduces the bug using the iPhone that was updated to iOS 12.1.
iOS 12.1 allows by pass the passcode to see all contacts private information. Feature? Flaw? - YouTube
Press and hold the Home button to activate Siri. Using a ballpoint pen is supposed to prevent unlocking with TouchID.

On the screen of "What is your message?" When you talk to "Tell me" Test "... ...

"Which?" Siri returned, so select "Test".
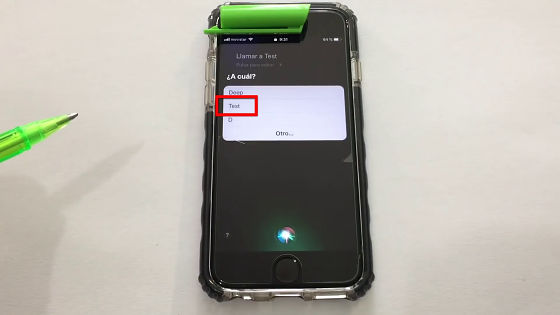
Then Siri called "Test".

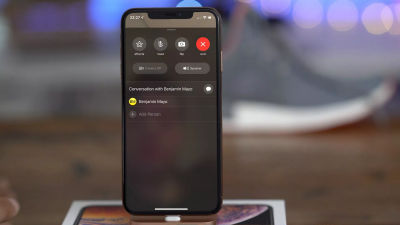
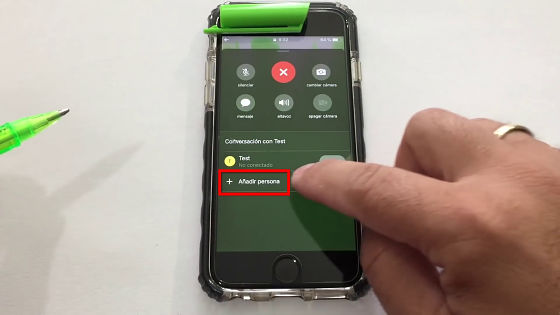
When "Test" gets the phone, start FaceTime frankly.

At this time, Rodriguez switched the terminal to flight mode.

Then tap the menu icon at the bottom right of the screen ... ...

Tap "Register new contact".
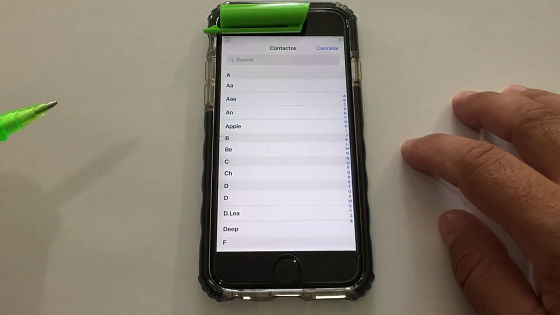
Tap "+" at the top right of the screen ......

A list of existing address books has been displayed. It is important to note that the terminal has never been unlocked so far .
You can also use 3D Touch to confirm details of registration ... ...
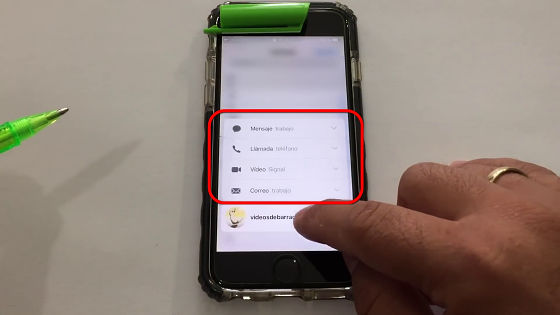
E-mail address etc can also be confirmed.
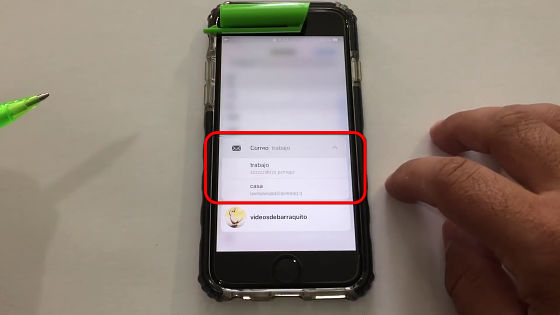
It seems that all the address book functions can be used apparently, such as the search function.
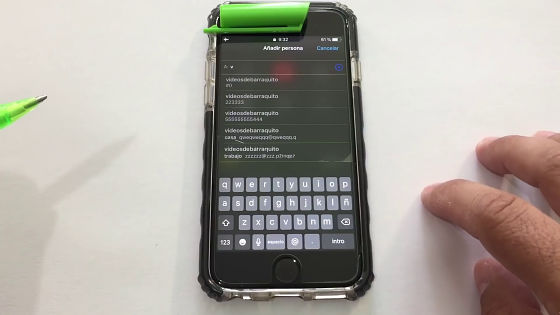
Apparently there seems to be no problem to avoid this problem immediately. Wait for updating to iOS 12.1 or if you have already updated it seems there is no way but to watch out until Apple releases the countermeasure version.
Related Posts: