A method to access photos and contacts in the iPhone without a passcode entry is discovered

by NeONBRAND
A vulnerability has been discovered that makes it possible to access "a device locked with a passcode" without inputting a passcode in the latest version of iOS " iOS 12 " which is a mobile OS for the iPhone / iPad. With vulnerabilities, attackers can access photos and contacts stored on the target iPhone.
iPhone XS Passcode Bypass Hack Exposed Contacts, Photos | The first stop for security news | Threatpost
https://threatpost.com/iphone-xs-passcode-bypass-hack-exposes-contacts-photos/137790/
The newly discovered vulnerability is that if you can physically touch an iPhone locked with a passcode, you will be able to access the data in the terminal bypassing passcode entry. It is the Spanish security researcher Jose · Rodriguez who discovered the vulnerability, and on his own YouTube account, I have released a movie reproducing how to access the data in the terminal without actually entering the passcode.
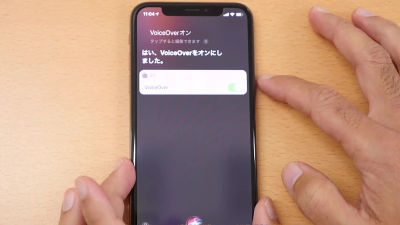
There are two ways, both of which use speech recognition assistant Siri and one of accessibility functions VoiceOver. As a method, both are considerably complicated, and Siri is enabled, Face ID of face authentication function is invalid, TrueDepth camera needs to be covered with tape etc. and not function there is.
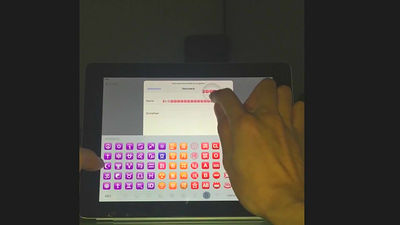
In the following movie, Siri × VoiceOver × phone function is used to reproduce the way to avoid entering the passcode to the terminal. You can access the contact in 16 steps and the photo in 37 steps, so you can see that you can access the data in the terminal via a fairly complicated operation.
Passcode Bypass iOS 12 (1-Call) - YouTube
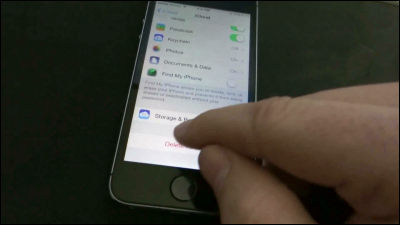
In the following movies, we use Siri and VoiceOver to reproduce the way to access data in the terminal from the memo app.
Passcode Bypass iOS 12 (2-Note) - YouTube
According to Threatpost of the security related news media that confirmed this movie, the vulnerability discovered by Rodriguez is reproducible on every terminal including " iPhone XS / XS Max " which is Apple's latest device.
The way to avoid iPhone passcode entry has become pretty popular over the last few years and security researchers and hackers are looking for loopholes each time the latest version of iOS is released. Rodriguez uses Siri and VoiceOver to bypass the passcode, but when iOS 10 was released it was discovered how to use Siri and VoiceOver in the same way.
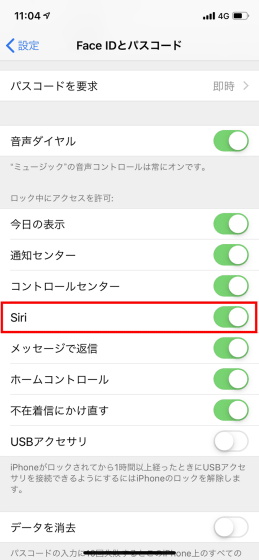
In order to prevent accessing data in the terminal by this method, it is best not to touch your iPhone to anyone, but go to "Settings" → "Face ID and passcode" , It is also effective to disable "Siri" in "Allowing access while locking". With this setting, you can not use Siri while locking, so you do not have to worry about bypassing your passcode.
Threatpost seems to ask Apple for comment on this issue, but he seems to have not received a reply at the time of writing the article.
Related Posts:
in Video, Software, Smartphone, Security, Posted by logu_ii