A critical fatal vulnerability in USB is discovered and its code is released
A fatal vulnerability in design was found on the USB which established the immovable status as the connection terminal of the PC, and the hacking method which exploits this vulnerability "BadUSB"Was held in August 2014 at the developer conferenceBlack Hat 2014 USAIt was announced in. The technician who announced about BadUSB did not disclose the code taking into consideration the risk of vulnerability without effective measures,DerbyCon 4.0In the lecture of BadUSB code was released by another technician.
SRLabs-BadUSB-BlackHat-v1.pdf
(PDF file)https://srlabs.de/blog/wp-content/uploads/2014/07/SRLabs-BadUSB-BlackHat-v1.pdf
The Unpatchable Malware That Infects USBs Is Now on the Loose | WIRED
http://www.wired.com/2014/10/code-published-for-unfixable-usb-attack/
USB has a huge security problem that could take years to fix | The Verge
http://www.theverge.com/2014/10/2/6896095/this-published-hack-could-be-the-beginning-of-the-end-for-usb
Security researchers Karsten Nol and Jacob Lell announced that there is a vulnerability to undetectably send malware to the USB firmware and naming the hacking technique to exploit this vulnerability as "BadUSB" did. You can see how to explain BadUSB in the following movie.
BadUSB - On Accessories that Turn Evil by Karsten Nohl + Jakob Lell - YouTube
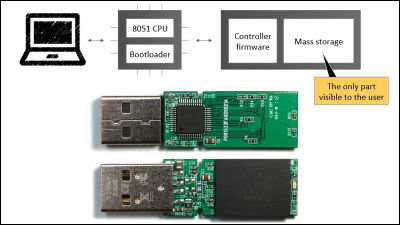
Terminals that use all USB terminals have dedicated chips and firmware so that the terminal can be recognized by firmware. Mr. Nor and Mr. Lell have discovered that this USB firmware has a design vulnerability that can be rewritten by exploiting this vulnerability. If you modify the firmware, you can sneak malware to the USB memory for example, tamper with the USB storage data, or operate the USB keyboard without permission.
According to Mr. Nor, the vulnerability of BadUSB is a USB design problem, it is impossible to rectify this, and it is necessary to rebuild the new USB standard from the beginning to apply security measures around the firmware . It is expected that it will take several years to create a new standard from scratch and that the influence of USB terminals is widespread around the globe will have a big impact, so Mr. Knoll and Mr. Lell will not disclose BadUSB code I made it.
However, at the security conference Derbycon held from September 24, 2014, Adam Cordill and Mr. Brandon Wilson announced that they had reverse engineered BadUSB,GitHub, We demonstrated to exploit the vulnerability as an exploit method by hacking the user's USB keyboard and entering the key as desired.
Adamcaudill / Psychson · GitHub
https://github.com/adamcaudill/Psychson
In addition, Mr. Cordill and Mr. Wilson 's lecture can be seen in the following movie.
T 510 Making BadUSB Work For You Adam Caudill Brandon Wilson - YouTube
Mr. Cordill and Mr. Wilson have described the reason why the code of BadUSB was released "to put pressure on USB hardware manufacturer". Based on the belief that manufacturers should not be keen on solving this problem if BadUSB is not made public and that it should be better to release dangerously in order to demand more serious measures.
Cordill already bad BadUSB hackingNSA"It is currently limited to organizations with huge amounts of funds such as NSA that can execute BadUSB hacking at present, anyone who publishes the code of BADUSB Only being able to use it gives manufacturers the pressure "this vulnerability must be fixed", "he said.
Related Posts:







