Malware emerging to avoid security of Chrome extension

Trend Micro, which develops and sells security related products for the Internet, has disclosed in the company's blog that malware to avoid the security of Chrome extension function has appeared.
Malware Bypasses Chrome Extension Security Feature | Security Intelligence Blog | Trend Micro
http://blog.trendmicro.com/trendlabs-security-intelligence/malware-bypasses-chrome-extension-security-feature/
In the beginning of 2014, in order to deal with the problem that "malicious browser extension is on the market", "Chrome Web StoreEnhancement of security policy so that only extended functions hosted on the server can be installed ". Trend Micro revealed that malware that attempts to avoid this security also exists, although it was thought that this influence was significantly improved by this influence.
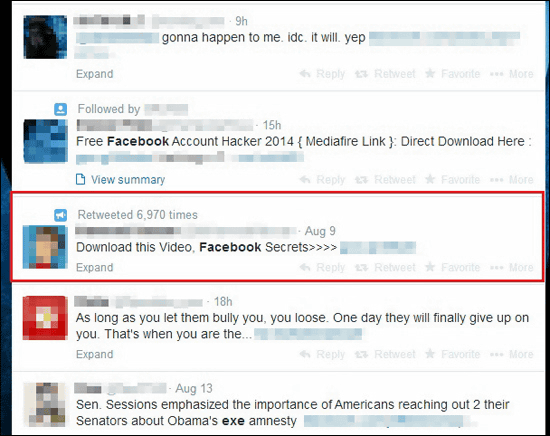
The extended function found by Trend Micro is "to get through Google Chrome's security policy and let's install it to users anyway." The name is "Facebook Secrets", it seems that it was spread on Twitter as a set consisting of short URLs and simple sentences explaining the features. The following image If you click the URL of tweet in the red frame part, it is skipped to a certain site and the execution file is downloaded automatically in the user's PC.
The name of the downloaded executable file is "download - video.exe", which is said to be malware containing "TROJ_DLOADE.DND". These malware is also characterized in that it often makes a file name such as "flash.exe" to make it a trustworthy user even a little.
Automatic Execution As soon as the file is downloaded, the browser extension will also be installed in the PC together. Since the installed extension is pretending to Flash Player, it seems to be software which seemingly does not hurt anything.
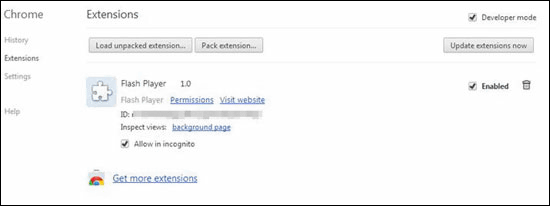
In order to avoid Google's security policy, malware creates folders in a directory separate from Google Chrome's browser extension component.
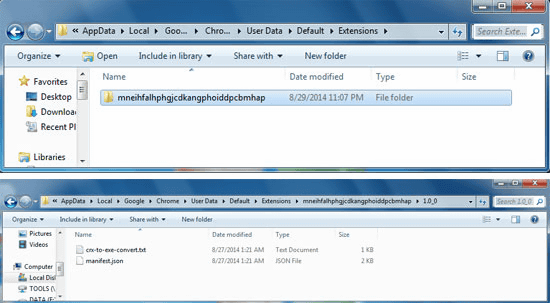
After installation, two files "manifest.json" and "crx - to - exe - convert.txt" appear in this folder. "Manifest.json" is a configuration file in which the extension name, version, etc. are described. "Crx - to - exe - convert.txt" contains a script to operate the extended function, and it seems that updating to the latest script can be done by accessing a specific URL at any time.
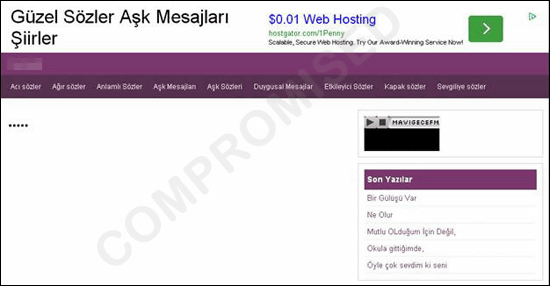
And when the user opens Facebook or Twitter, the extension opens certain sites without permission in the background. This "specific site" is said to be a typical click fraud site where Turkish texts are displayed one after another.
However, it seems that this kind of malware is not very effective, for example, it seems that tweets need to be retweeted more than 6000 times in order to encounter the URL where the user installs malware automatically. The way to protect yourself from these malware seems to be that you do not click short URLs that flow on Twitter and Facebook.
Related Posts:
in Software, Posted by logu_ii