The possibility that North Korea is trying to spy out the North Korean defectors and journalists using malware

byDmitry Ratushny
Popular communication application in Korea ·Kakao Talk, And other SNS such as Facebook, North Korea is infecting malware with terminals used by North Korean defectors and journalists, the Korean media reported. This is information indicating that North Korea is trying to steal information on North Korean refugees and journalists using various methods.
North Korean Defectors and Journalists Targeted Using Social Networks and KakaoTalk | McAfee Blogs
https://securingtomorrow.mcafee.com/mcafee-labs/north-korean-defectors-journalists-targeted-using-social-networks-kakaotalk/
The research team of McAfee, which develops security software, has obtained the malware APK file that North Korea is scattered, and publish its analysis results. According to McAfee, malware distribution includes Google's short URL creation service "Google URL ShortenerIt seems to be used.
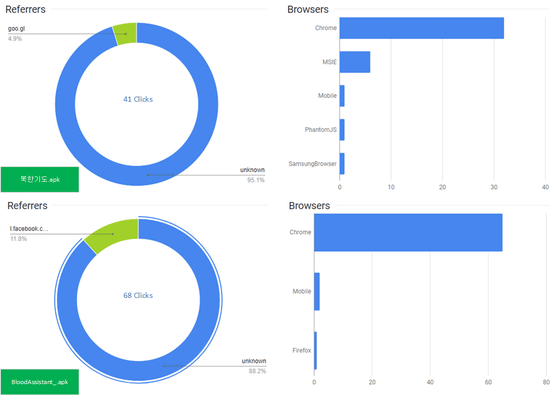
There are two malware distributed by North Korea, one is "북한 기도" (prayer of North Korea) and the other is "BloodAssistant" who disguised as a health care application. Access to URLs where these malware are distributed is mostly from Korean users, and it seems that Windows and Chrome are the majority of combinations of OS and browser being used. In addition, the URL to which "BloodAssistant" which is one of malware is distributed has about 12% access via Facebook.
When targeted as an attack, users will receive an abbreviated URL to news articles etc. Since the sent URL comes from the page for forwarding and the redirect destination is the page to distribute malware, in the thumbnail displayed together with the appearance of the URL, do not know if the link destination is a page to distribute malware It is becoming.
The following is a screenshot showing that the domain of the mail address used by Korean police called "mail.police.go.kr" has accessed the abbreviated URL. McAfee writes, "In short, this abbreviated URL indicates the possibility that it was sent from the police address."
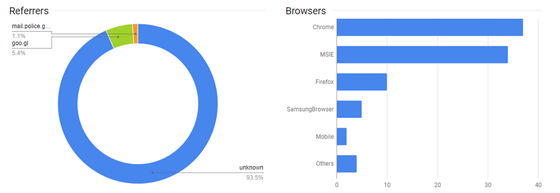
In addition, McAfee wrote that "Access to these URLs may include access not only by the victim but also by malware researchers," and the number of clicks may be information that is not very meaningful I am doing.
On the page where malware is distributed there is an APK file, which expands the Trojan on the victim's device. The screen belowA dropperScreenshot of the moment when it is running.
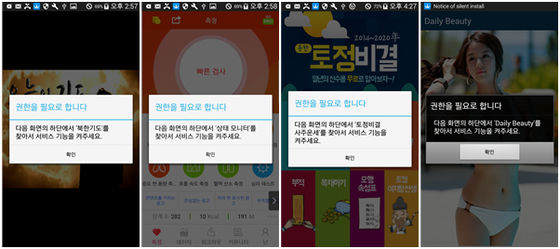
When the dropper is executed, it is first checked whether the target device is already infected with malware. If it is not infected, a notification as to whether access rights are given to the application is displayed, but if you tap the popup window, the application gets access right.
When malware gets access, malware starts to enable various other settings and install Trojan horse. However, in order to prevent the user from seeing that situation, malware suddenly forcibly displays a separate window, for example by playing the movie. In addition, it seems that the window to hide these behaviors disappears after installing the Trojan horse.
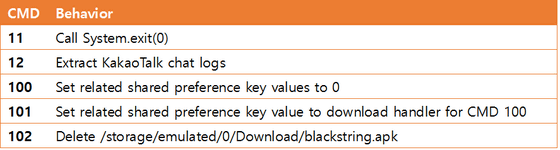
The installed Trojan horse seems to use Dropbox or Yandex as a control server for uploading data and receiving commands, saving infected terminal information in a temporary folder and uploading it to the cloud. In addition, you can download files containing commands and other data to control infected devices, and learn more brutal functions. It is also easy to update the entire malware, and there are things called "Capture chat log of cacao talk" among executable functions.
It is also clear that a malicious APK file is being uploaded on Google Drive with the same Google Account. In addition, it seems that SNS account was linked to this Google Drive address, and it turned out that it was sending to the target shortened URL to the webpage on which malware was distributed via these accounts Did. Since the group distributing malware uses Korean dramas and TV programs as the account name of the cloud service being used, I also know that it is a person familiar with Korean culture.
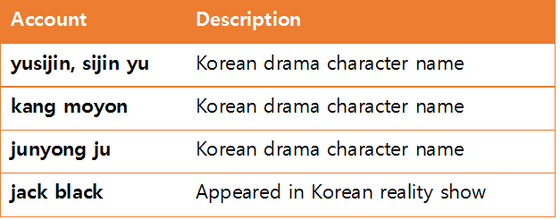
In addition, as we continue to analyze, we have also found the word "Flooding" (blood type) that is used only in North Korea, which is not used in Korea. In addition, the IP address of North Korea was found in the test log file of the Android terminal linked to the account used for spreading malware.
In addition, McAfee uses North Korean malware as a security application "McAfee Mobile Security"Android / HiddenApp.BP" to update it so that it can be detected. In order to protect you from these malware it is recommended not to install applications from unidentified sources and to run only from Google Play if installing cacao talk.
Related Posts:







