Malicious software "Kemoge" pretending to be an OS of a mobile terminal and forcibly displaying advertisements is diffusing into over 20 countries

ByLee Davy
A mobile researcher at FireEye, a security company, discovered "Android Takeover Malware" that is spreading acclaimedly to the whole world. Since the domain issuing the command is "aps.kemoge.net" in this attack, "Kemoge"It was named.
Kemoge: Another Mobile Malicious Adware Infecting Over 20 Countries «Threat Research | FireEye Inc
https://www.fireeye.com/blog/threat-research/2015/10/kemoge_another_mobi.html
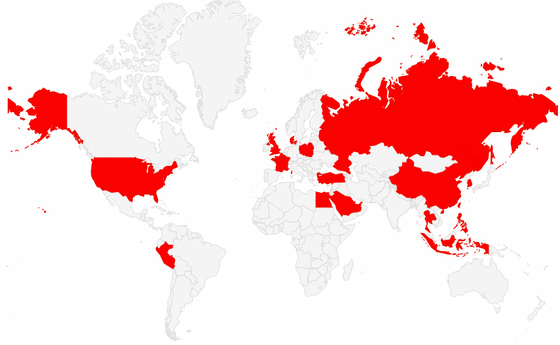
The current diffusion situation that FireEye indicated. It has spread to more than 20 countries already.
Since Kemoge is "distributed" with a look like a general app, it is quite difficult to distinguish from appearance. Kemoge's lifecycle is first installed on third-party app stores that are not Google Play and from devices like "promotions" "ads". Within the terminal, Kemoge acquires the device information and uploads it to the ad server,Forcibly pop-up advertisementIt will come to let me.
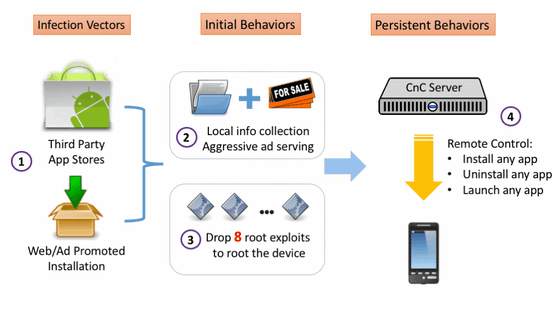
Furthermore, when the user unlocks the terminal or when there is a change in the network connection, it starts up the service and moves around finely, eventually obtaining the root authority. It is like to be able to receive a command from aps.kemoge.net by embedding camouflaged system services as if it were one of Android systems. In this state, an attacker can install, uninstall, and start arbitrary applications remotely.
FireEye actually tried, there was a movement to try to uninstall anti-virus applications and other legitimate applications. This is seen as preparing for further attacks. Since Kemoge contained simplified Chinese code, it is thought that it was made by a developer living in China or managed by a Chinese hacker.
At this time, it seems that it is not spreading to Japan, but FireEye says "Do not click suspicious link in mail, SMS, website and advertisement" "Do not install applications from other than official app store" "Android terminal Keep it up to date "as a countermeasure.
Related Posts:
in Security, Posted by logc_nt