Non-jailbreak iPhone and iPad are also spreading villainy malware "YiSpecter" infecting from multiple routes
ByClive Darra
Malware extracting personal information "XcodeGhostA situation where multiple applications infected with the App Store are delivered on the App Store occurred on September 24, 2015, causing a great confusion for the iOS users, but the application side distributed the patch or Apple infected We deleted the app from the App Store and so on. However, in less than a month from XcodeGhost, new types of malware that infect from multiple routes are discovered this time.
YiSpecter: First iOS Malware That Attacks Non-jailbroken Apple iOS Devices by Abusing Private APIs - Palo Alto Networks BlogPalo Alto Networks Blog
http://researchcenter.paloaltonetworks.com/2015/10/yispecter-first-ios-malware-attacks-non-jailbroken-ios-devices-by-abusing-private-apis/
A new type of malware that a security company Palo Alto discoveredYiSpecter"Infects a terminal equipped with Apple's mobile OS" iOS "Jailbreak (Jailbreak)It is said that there is a risk of infection on all iOS devices regardless of whether it is a finished terminal or not. Palo Alto says, "It is the first malware using iOS's private API and implements malicious functions," calling for strict precautions.

According to a survey by Palo Alto, YiSpecter appeared in November of 2014, spreading mainly in China, and at the time of article creation, Taiwanese iOS users also reported successive infections of YiSpecter . YiSpecter has a big feature to keep in mind different from other malware, it is that there are multiple infection routes.
For example, since XcodeGhost is infected via an application, there was practically no damage unless you installed an application infected with XcodeGhost on your terminal. However, the YiSpecter discovered this time is confirmed as multiple infected routes such as installation of online / offline applications, Internet service provider (ISP), SNS worm, etc. It is thought that there is a possibility of causing damage to a wide range of users I will.
According to Palo Alto, "HYQvod" and "DaPian" are the main infected applications, the main thing of malware infection is via the application. When this application is installed, a malicious application named "NoIcon" is also installed at the same time, and "Connect to the command and control the server using HTTP" "Upload basic information on the device" "Execute search and remote command" Changing Safari settings on iOS "" Installing malicious apps "ADPage" and "NoIconUpdate" "Acting to monitor trends of other applications and display advertisements using ADPage" .
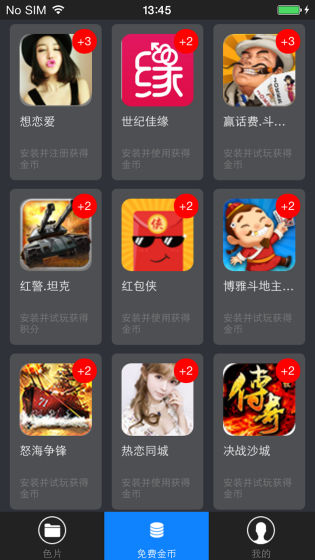
Infected routes via ISP with Internet traffic hijacked have also been confirmed, which displays a popup trying to install infected application's HYQvod during browsing in Safari. However, this pop-up is not displayed on mobile network connection, it seems that it will be displayed only when connected via Wi-Fi.
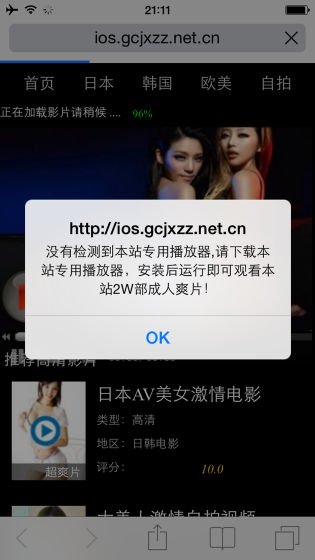
In a survey conducted by Chinese enterprise "Kikitera 360" and anti-virus software developer "Cheetah Mobile", YiSpecter is diffusing using a worm called "Lingdun" that avoids malware detection Also known. Lingdun avoids the detection system using VeriSign and Symantec's fake certificate and installs the software on its PC without permission. Most of the software Lingdun installs on the PC is harmless, but only one malicious one is included. When installing that software, the user's login information in China's messenger service "QQ" will be stolen.
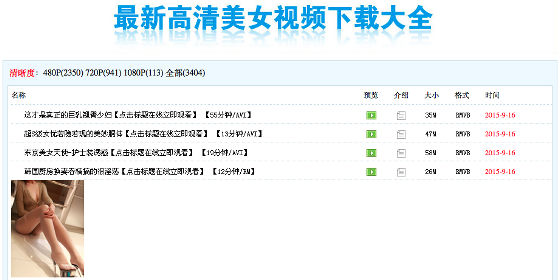
When installing malicious software, it breaks in the HTML file by breaking into the file sharing interface of QQ group chat using the user's login information. If you open that HTML file on your Android device, you will download adware that tries to install pornographic applications and open it on iOS will cause YiSpecter to be installed.
YiSpecter is made up of four different components, three of which have the function to hide the icon with the software "SpringBoard" which manages the application of iOS, so that users can find and delete themselves It is getting harder. Also, it is somewhat troublesome to make the name of the component the same as the system application so that it is difficult to find out. He told Apple about YiSpecter's problem. Palo Alto cites the following three points as a countermeasure and prevention method of YiSpecter
· Open "Settings" of iOS, open "Profile" inside "General", delete unknown or untrusted profile.
· Deleted if the application "Information dissemination device", "FREE SERVICE DOCUMENTS" "FREEZING 0" was installed.
·IFunBoxUsing third-party iOS management tools such as iOS, check all the applications installed on iOS device, remove apps with names similar to Phone, Weather, Game Center, Passbook, Notes, Cydia. Be careful not to delete the standard application at that time.
Related Posts:







