Ransomware wearing television to demand ransom appears
IPhoneYaAndroidRequest a ransom for unlocking by disabling the smartphone, "RansomwareAlthough malware called "malware" has been found, it is reported that "FLocker" of Android terminal lock type Ranthermware won not only smart phones but also how smart TV locked and ransom claimed.
TrendLabs Security Intelligence BlogFLocker Mobile Ransomware Crosses to Smart TV - TrendLabs Security Intelligence Blog
http://blog.trendmicro.com/trendlabs-security-intelligence/flocker-ransomware-crosses-smart-tv/

Ransomware for mobile "FLocker", impact on smart TV | Trend Micro Security Blog
http://blog.trendmicro.co.jp/archives/13453
FLocker has been confirmed from May 2015 as Ransomuware, it is detected as "ANDROIDOS_FLOCKER.A" on Android terminal, more than 7000 variants have been discovered. According to Trend Micro of security related products and services company, FLocker repeatedly increases and decreases from 2015 to 2016, and when it rapidly increased in April 2016, more than 1200 variants were confirmed.
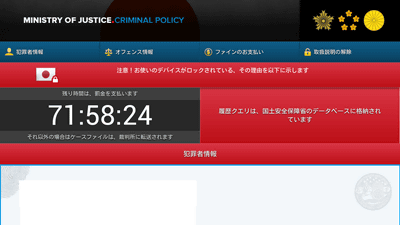
In Japan, in early March 2016, Police Ransom pretending to be a law enforcement agency with a subspecies of FLockerInfluxdoing. This variant corresponds to multiple languages, and in Japanese display, it names "MINISTRY OF JUSTICE (Ministry of Justice)". When an Android terminal infects FLocker, the terminal becomes inoperable and the user is requested as an ransom for an iTunes gift card of 1 to 20,000 yen. In this time, in addition to Android smartphone, an instance where Android equipped smart TV or TV Box is infected with FLocker was discovered. According to Trend Micro's analysis, there was no difference with FLocker that has been found so far.

In order to avoid detection by static analysis, FLocker hides its code as a raw data file in the Android's assets folder, and the file name pretends to be an ordinary file "form.html".

Classes.dexSince the code is simple, it is impossible to confirm illegal behaviors on the terminal side. When classes.dex is executed, form.html is decrypted and incorrect code is executed. The following is the code of classes.dex.

The code decrypted from form.html is as follows.
When FLocker is executed, it confirms the terminal area of the terminal and ends activities if it is sent from Kazakhstan, Azerbaijan, Bulgaria, Georgia (Georgia), Hungary, Ukraine, Russia, Armenia, Belarus. If it originates from outside of these nine countries, it is programmed to initiate fraudulent activity 30 minutes after infection, and Trend Micro is working on "handling work to avoid dynamic analysis using virtual environment (sandbox) technology It is analyzed as "It is.
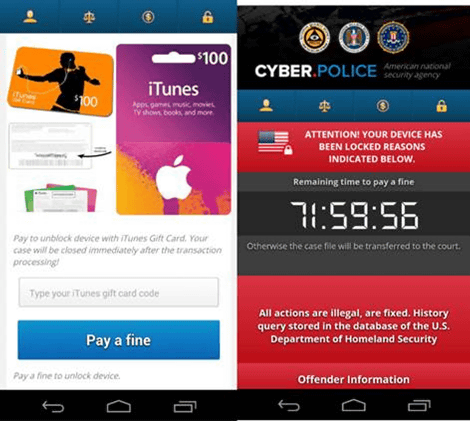
Thirty minutes after infection, FLocker requests administrator privileges on the terminal. When the user rejects the request, FLocker displays a screen impersonating the system update. And while continuing execution in the background, FLocker connects to the remote operation server and receives the command. The remote operation server sends an unauthorized application called "misspelled.apk" · HTML file · JavaScript to the terminal, the HTML file installs the unauthorized application and takes a picture of the user using JavaScript. Pictures taken are displayed on the threatening page. Below is a threatening screen of FLocker of mobile terminal.
While the terminal is locked, the remote operation server gathers information on the terminal, phone number, contact information, current location information, etc. The collected information is encrypted with hard-coded AES method and encoded by Base64 method.
In Trend Micro, "Ransomware often goes through SMS spam messages and unauthorized links, and during infection of mails and websites, while playing movies and music, infecting even by receiving messages and downloading files There are warnings that you should be very careful when you browse the Internet or receive messages from unknown sources. " In the unlikely event that Android smart TV or TV Box is infected with Ransomware, Trend Micro recommends "Ask the manufacturer of the terminal about how to deal with it". Also, it is said that it is also possible to delete a malicious program by executing debugging using the command line tool "Android Debug Bridge (ADB)".
Related Posts: