Dutch government's Military Intelligence and Security Service warns that Chinese hackers have infiltrated around 20,000 FortiGate systems around the world
In February 2024, the Dutch Military Intelligence and Security Service (MIVD) and the General Intelligence and Security Service (AIVD) reported that hackers backed by the Chinese government had infiltrated the network of
National Cyber Security Center
https://www.ncsc.nl/actueel/nieuws/2024/juni/10/aanhoudende-statelijke-cyberspionage-campagne-via-kwetsbare-edge-devices

20,000 Fortinet devices breached – reboots no defence
Chinese hackers breached 20,000 FortiGate systems worldwide
https://www.bleepingcomputer.com/news/security/chinese-hackers-breached-20-000-fortigate-systems-worldwide/
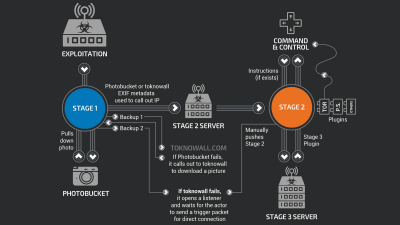
According to MIVD, Chinese hackers exploited a vulnerability called CVE-2022-42475 in FortiOS and FortiProxy, the operating systems that run FortiGate, to deploy malware called COATHANGER on FortiGate network security appliances over a period of several months from 2022 to 2023.
Once COATHANGER has infiltrated the networks of its targets, which include dozens of Western governments and international organizations, as well as numerous defense industry companies, it automatically installs a backdoor.
Chinese cyber spies access Dutch military network, intelligence agency reveals

MIVD and AIVD continued their investigations after the February 2024 report, reporting that 'it became clear that China's cyber espionage activities are much more widespread than previously known.' Specifically, between the exploitation of CVE-2022-42475 and its publication by Fortinet in January 2023, COATHANGER infected approximately 14,000 devices. Even after the publication, attackers continued to attack unpatched devices, accessing at least 20,000 FortiGate systems in the months between 2022 and 2023.
According to MIVD, COATHANGER has the stealth to hide the malware from scans and persistence to withstand reboots and firmware updates. Therefore, once COATHANGER is infiltrated, it is difficult to remove. MIVD points out that 'Once COATHANGER is infiltrated, the Chinese government has permanent access to FortiGate systems. Even if the victim installs security updates from FortiGate, the Chinese government can maintain access to the victim's device.'
'It is unclear how many victims actually have COATHANGER installed. The Dutch intelligence and cybersecurity agency NCSC believes that Chinese government-backed hackers may be further expanding the scope of their attacks and carrying out additional actions, such as data theft,' it said.

The Stack, an overseas media outlet, said, 'The only way to remove COATHANGER from an infected FortiGate device is to format, reinstall and reconfigure the device.' In addition, the Dutch Ministry of Defense reported, 'We have identified methods, such as YARA rules and JA3 fingerprinting, to detect COATHANGER.'
Related Posts:
in Security, Posted by log1r_ut