ArcaneDoor exploits Cisco zero-day vulnerability to infiltrate government networks

A cyber attack called ' ArcaneDoor ' has been detected that exploits vulnerabilities in
ArcaneDoor - New espionage-focused campaign found targeting perimeter network devices
https://blog.talosintelligence.com/arcanedoor-new-espionage-focused-campaign-found-targeting-perimeter-network-devices/
Cisco Adaptive Security Appliance and Firepower Threat Defense Software Web Services Denial of Service Vulnerability
https://sec.cloudapps.cisco.com/security/center/content/CiscoSecurityAdvisory/cisco-sa-asaftd-websrvs-dos-X8gNucD2
Cisco Adaptive Security Appliance and Firepower Threat Defense Software Persistent Local Code Execution Vulnerability
https://sec.cloudapps.cisco.com/security/center/content/CiscoSecurityAdvisory/cisco-sa-asaftd-persist-rce-FLsNXF4h
Nation-state hackers exploit Cisco firewall 0-days to backdoor government networks | Ars Technica
https://arstechnica.com/security/2024/04/cisco-firewall-0-days-under-attack-for-5-months-by-resourceful-nation-state-hackers/
'Sophisticated' nation-state crew exploiting Cisco firewalls • The Register
https://www.theregister.com/2024/04/24/spies_cisco_firewall/
ArcaneDoor hackers exploit Cisco zero-days to breach govt networks
https://www.bleepingcomputer.com/news/security/arcanedoor-hackers-exploit-cisco-zero-days-to-breach-govt-networks/
Over the past 18 months, threat actors, primarily backed by the Chinese government, have launched attacks that exploit previously unknown vulnerabilities in security devices from Ivanti, Atlassian, Citrix, Progress and others. These security devices sit on the so-called ' perimeter ' of the internet, providing a direct pipeline to our most sensitive resources and interacting with virtually all incoming communications, making them ideal targets for cyberattacks.
It has become clear that Cisco's ASA product , one of such boundary devices, has been the target of attacks by Chinese government-backed hackers. According to the research team of Cisco Talos , Cisco's cybersecurity team, since November 2023, an unknown threat actor has been detected and tracked by Cisco as 'UAT4356' and Microsoft as 'STORM-1849.'
This threat actor has been identified as using two previously undetected pieces of malware to carry out zero-day attacks . The zero-day attack by this threat actor is called 'ArcaneDoor' and has the following characteristics:
・ArcaneDoor is a sophisticated exploit chain that targets multiple vulnerabilities, including at least two zero-day exploits.
ArcaneDoor contains two previously undetected, mature, full-featured backdoors, one of which is designed to remain resident only in memory to avoid detection.
ArcaneDoor takes great care to cover its tracks by removing any artifacts that the backdoor may leave behind, often customizing the removal of artifacts based on the characteristics of a specific target.

Taking into account the above characteristics, Cisco Talos researchers have assessed that the zero-day attack is the work of 'government-sponsored hackers with espionage objectives.' The researchers wrote, 'Our attribution assessment is based on the significant level of sophistication employed in terms of victimology, capability building, and forensic countermeasures, as well as the identification and subsequent chain of events of a zero-day vulnerability. For these reasons, we assess with high confidence that the zero-day attack was carried out by a state-sponsored actor.'
The research team warned that ArcaneDoor may target devices other than Cisco's ASA products. They also noted that it was unclear at the time of writing how 'UAT4356' achieved initial access. Therefore, the ASA product vulnerability may be exploited because 'an unknown vulnerability (one or more) was exploited' at the time of writing. It has been suggested that this 'unknown vulnerability' may exist in network software such as Microsoft's.
'Regardless of your network equipment provider, now is the time to ensure that your devices are properly patched, logging is done in a central, secure location, and strong multi-factor authentication (MFA) is configured. Cisco has released security updates to patch the vulnerabilities and urges all ASA users to install them immediately,' the Cisco Talos research team said.
'UAT4356' has been developing and testing exploits since around July 2023, setting up a server infrastructure dedicated to attacks in November, and starting full-scale cyber attacks using ArcaneDoor in January 2024. The timeline of attacks by UAT4356 on Cisco products is as follows:
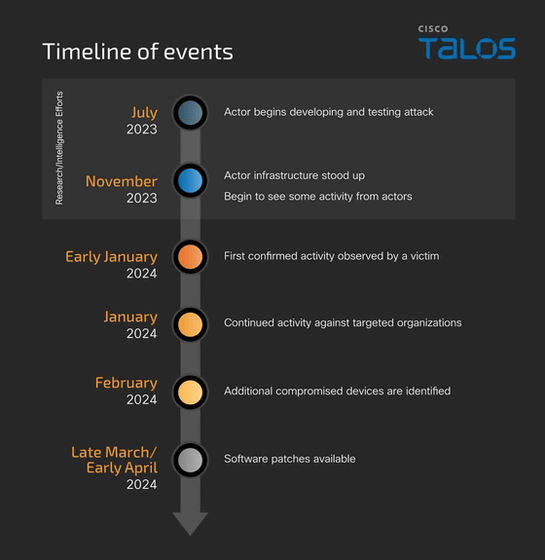
One of the vulnerabilities exploited by ArcaneDoor is ' CVE-2024-20359 '. This vulnerability exists in a feature that allows preloading of ASA VPN clients and plugins, which is discontinued at the time of writing. This vulnerability is caused by improper validation of files when reading them from the flash memory of a vulnerable device, and if exploited, could lead to remote code execution with root system privileges. 'UAT4356' exploited CVE-2024-20359 to introduce two backdoors, Line Dancer and Line Runner. In addition, 'UAT4356' has also been found to have installed a backdoor on network equipment by exploiting a vulnerability called ' CVE-2024-20353 '. Cisco has already fixed the two vulnerabilities, CVE-2024-20359 and CVE-2024-20353.
According to Cisco Talos researchers, Line Dancer is a memory-only backdoor with minimal reliance on files stored on disk. Memory-resident malware is an advanced technique used by hackers to evade various forms of detection, and once installed, Line Dancer allows hackers to use simple unauthenticated web requests to send malicious code through the host scan reply field component.
According to the research team, the host scan reply field is typically used later in the SSL-VPN session establishment process and is processed by ASA devices configured for SSL-VPN, IPsec IKEv2 VPN, client services or HTTPS management access. However, ArcaneDoor modifies the default host scan reply code pointer to point to the Line Dancer shellcode interpreter, allowing threat actors to use POST requests to interact with the device without authenticating or interacting directly through traditional management interfaces.
On the other hand, Line Runner has built-in defense mechanisms to avoid detection by security software and allows attackers to execute arbitrary Lua code on a hacked system.
Cisco strongly recommends monitoring system logs for signs of unscheduled reboots, unauthorized configuration changes, or suspicious credential activity.
◆ Forum is currently open
A forum related to this article has been set up on the official GIGAZINE Discord server . Anyone can post freely, so please feel free to comment! If you do not have a Discord account, please refer to the account creation procedure explanation article to create an account!
• Discord | 'Are you using any Cisco products?' | GIGAZINE
https://discord.com/channels/1037961069903216680/1232985602064908288
Related Posts:
in Security, Posted by logu_ii







