UK and US identify and warn Russia-backed hacking group new botnet malware 'Cyclops Blink'

US and UK cybersecurity authorities and law enforcement agencies have warned of the new malware ' Cyclops Blink ' used by the Russian government-backed hacker group
New Sandworm malware Cyclops Blink replaces VPNFilter --NCSC.GOV.UK
https://www.ncsc.gov.uk/news/joint-advisory-shows-new-sandworm-malware-cyclops-blink-replaces-vpnfilter
Important Detection and Remediation Actions for Cyclops Blink State-Sponsored Botnet | WatchGuard Technologies
https://www.watchguard.com/wgrd-news/blog/important-detection-and-remediation-actions-cyclops-blink-state-sponsored-botnet
Russia's most cutthroat hackers infect network devices with new botnet malware | Ars Technica
https://arstechnica.com/information-technology/2022/02/russias-most-cut-throat-hackers-infect-network-devices-with-new-botnet-malware/
US, UK link new Cyclops Blink malware to Russian state hackers
https://www.bleepingcomputer.com/news/security/us-uk-link-new-cyclops-blink-malware-to-russian-state-hackers/
Since June 2019, a malware called 'Cyclops Blink' that helps sandworm operators create botnets has been confirmed to target devices on the WatchGuard Firebox and SOHO networks.
NCSC, the National Cyber Security Center in the United Kingdom, told Cyclops Blink that the malware named Cyclops Blink will replace the malware released in 2018, VPNFilter , which will allow sandworms to remotely access the network. 'There is a sex.' 'Cyclops Blink is common with VPN Filter, and it seems that the deployment is spreading indiscriminately.'
According to NCSC, Cyclops Blink is primarily deployed on WatchGuard devices, but sandworms may be able to compile Cyclops Blink for other architectures and firmware.
The targeted WatchGuard developers note that Cyclops Blink may have affected about 1% of active WatchGuard firewall appliances on devices used primarily by business customers.

According to analysis by agencies such as NCSC, FBI, CISA and NSA, Cyclops Blink uploads / downloads files to and from
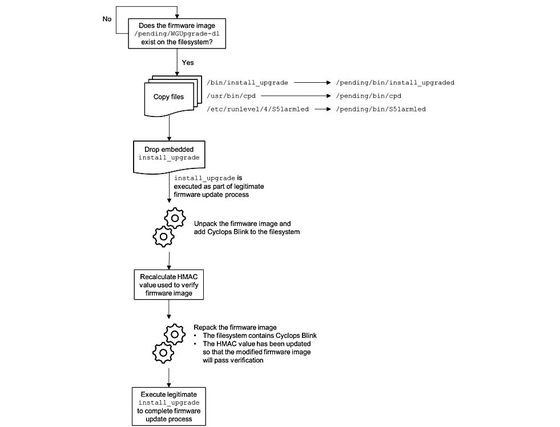
According to NCSC, 'Cyclops Blink persists on reboot and throughout the legitimate firmware update process, so affected organizations need to take steps to remove the malware.'
WatchGuard will work closely with the FBI, CISA and NCSC to provide tools and guidance that will enable the detection and removal of Cyclops Blinks on WatchGuard devices through a non-standard upgrade process.
All accounts on Cyclops Blink infected devices should be considered compromised, so organizations should immediately remove Internet access to the management interface of the affected network device.
Related Posts: