GitLab server turns out to be exploited for DDoS attacks above 1Tbps

It has been reported that
GitLab CE CVE-2021-22205 in the wild --hn security
https://security.humanativaspa.it/gitlab-ce-cve-2021-22205-in-the-wild/
GitLab servers are being exploited in DDoS attacks in excess of 1 Tbps --The Record by Recorded Future
https://therecord.media/gitlab-servers-are-being-exploited-in-ddos-attacks-in-excess-of-1-tbps/
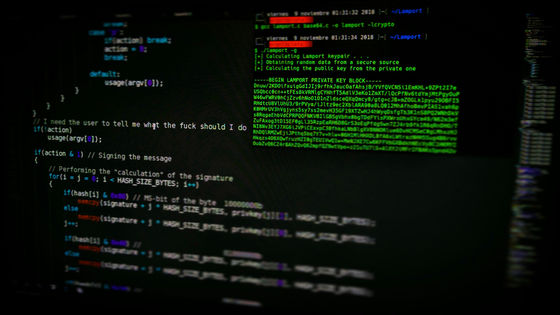
The problem vulnerability ' CVE-2021-22205 ' is a library called 'ExifTool ' used by both the open source version of GitLab Community Edition and the paid GitLab Enterprise Edition to remove metadata from images uploaded to the server. It uses the behavior of. It has been reported that ExifTool version 7.44 or later has improperly disabled user data in DjVu format and can execute arbitrary code when analyzing malicious images.
CVE-2021-22205 has not been shown to be abused for a long time, but on October 25, 2021, Italian security company HN Security said, 'A suspicious user stabbed CVE-2021-22205 and was promoted to privilege. I achieved the case. ' In this report, HN Security conducted an investigation after receiving a report from a customer that 'two suspicious accounts with random strings as user names have gained administrator privileges', and as a result, privilege promotion It was said that the vulnerability that made it possible was found to be CVE-2021-22205. The two suspicious accounts actually reported to HN Security were like this.
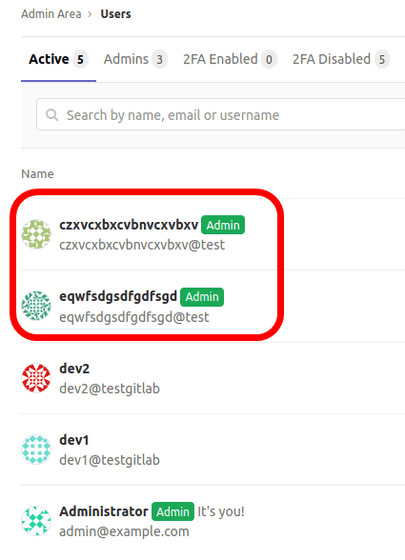
HN Security reported that 'the purpose of the attack is unknown' because the images uploaded by the attacker to poke CVE-2021-22205 are not saved, but on November 4, 2021, he specialized in DDoS attacks. 'A botnet of thousands of GitLab instances compromised by CVE-2021-22205 is performing a DDoS attack of over 1 Tbps,' said Damian Menscher, Google's security reliability engineer. I revealed it in.
A botnet of thousands of compromised #GitLab instances (exploited via CVE-2021-22205) is generating DDoS attacks in excess of 1 Tbps. Please patch your servers!
— Damian Menscher (@menscher) November 4, 2021
According to an analysis released by cybersecurity company Rapid7 on November 1, 2021, of the more than 60,000 GitLab servers connected to the Internet, about half, or 30,000, will fix CVE-2021-22205. He said he has not applied the patch. The Record, which reported this incident, recommended that the patch be applied immediately, and the ExifTool vulnerability that started the problem is affecting other types of web applications, further vulnerabilities. Touching on the possibility of creating sex, he commented, 'The easiest way to prevent an attack is to block uploads of DjVu files at the server level if you don't need to work with them.' ..
Related Posts:
in Security, Posted by darkhorse_log