Google points out that ``hacker groups supported by the Russian and Chinese governments are conducting attacks by exploiting WinRAR's zero-day vulnerability.''

Google's security research team has found evidence that hackers backed by the Russian and Chinese governments are exploiting vulnerabilities in Windows file compression and decompression software
Government-backed actors exploiting WinRAR vulnerability
https://blog.google/threat-analysis-group/government-backed-actors-exploiting-winrar-vulnerability/
Google links WinRAR exploitation to Russian, Chinese state hackers
Russia and China-backed hackers are exploiting WinRAR zero-day bug | TechCrunch
https://techcrunch.com/2023/10/18/russia-sandworm-fancy-bear-china-winrar-zero-day/
WinRAR is shareware for Windows released in 1995, and is an archiver that can compress and decompress RAR and ZIP formats, as well as LZH format and 7-Zip format.
According to Google's Threat Analysis Group (TAG), attackers are conducting attacks by exploiting a zero-day vulnerability in WinRAR called ``CVE-2023-38831.'' Group-IB, the cybersecurity firm that first discovered CVE-2023-38831, said, ``This zero-day vulnerability can be used to attack malicious archive files disguised as benign images or text documents. You can hide certain scripts.' Rarlab, the vendor of WinRAR, applied a patch and fixed CVE-2023-38831 on August 2, 2023. However, TAG points out that ``many users who have not updated WinRAR are at risk.'' In fact, TAG reports that ``Multiple hacking groups supported by the Russian and Chinese governments are exploiting CVE-2023-38831 to conduct hacking.''
According to TAG's report, some groups that exploit WinRAR vulnerabilities to carry out hacking activities are known to have launched the ransomware NotPetya , which caused major damage to Ukraine's central bank, state-run telecommunications, and power infrastructure in 2017. It includes a Russian military spy unit called 'Sandworm' that uses this to carry out attacks.
TAG reports, ``Sandworm has been confirmed to be exploiting a zero-day vulnerability in WinRAR since early September 2023 as part of an email campaign impersonating a Ukrainian drone combat training school.'' Sandworm's method is to include a link in the email to an archive file that exploits CVE-2023-38831, and if the link is opened, malware will be installed on the victim's PC to steal information. , the passwords used in the browser were leaked.

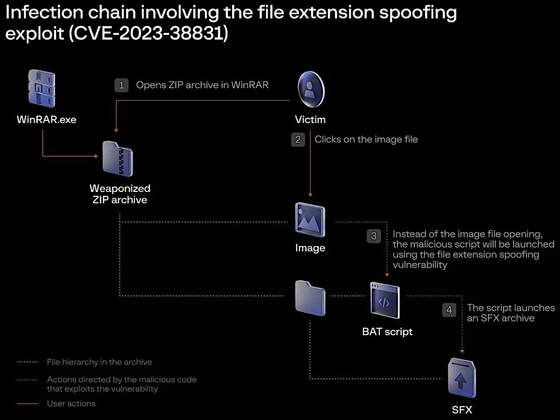
This is how the hacker group's techniques are illustrated. A user unzips the problematic zip file with WinRAR and opens the image file it contains. Then, instead of opening the image file, a script that installs malware is launched, destroying the SFX file system that prevents unauthorized access to the computer.
In addition, the Russian government-backed hacker group APT28 (Fancy Bear) is launching an email campaign impersonating a Ukrainian public policy think tank to attack Ukrainian internet users, and the Chinese government TAG has reported that APT40 , which supports the attack, was conducting a phishing campaign targeting users based in Papua New Guinea using similar techniques. In the campaigns conducted by these hacker groups, a link to Dropbox containing an archive file that exploits CVE-2023-38831 was attached to the victim.
TAG warns that WinRAR's zero-day vulnerability continues to be exploited despite the release of patches, ``This highlights that attacks that exploit known vulnerabilities are highly effective.'' ``Users should immediately apply the latest patches to WinRAR to ensure the safety of the software.''
Related Posts: