"Steganography" that infects malicious malware is found only by displaying advertisement by embedding invisible code in the image in the image

Data concealment technology that you do not know from the image of banner advertisements displayed on popular websites "SteganographyHacking techniques have been discovered that attach malicious software to vulnerabilities of users' PCs by crafting them.
Readers of popular websites targeted by stealthy Stegano exploit kit hiding in pixels of malicious ads
http://www.welivesecurity.com/2016/12/06/readers-popular-websites-targeted-stealthy-stegano-exploit-kit-hiding-pixels-malicious-ads/
Hacking Millions with Just an Image - Recipe: Pixels, Ads & Exploit Kit
http://thehackernews.com/2016/12/image-exploit-hacking.html
ESET researchers from security countermeasures found a suspicious program embedded in banner advertisements. This image is so-called steganography, it is impossible to notice that the malicious JavaScript code is embedded in the alpha channel that defines the transparency of the PNG image, and it is impossible to notice that the program is installed with the naked eye.
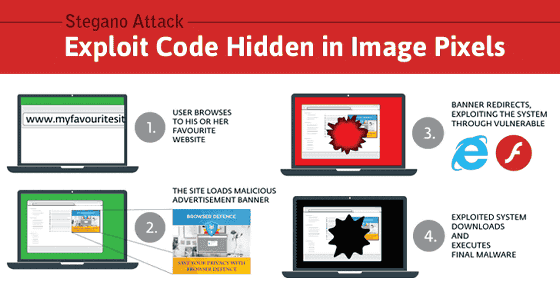
The mechanism of malware infection using this steganography is shown in the following figure. (1) When a user visits a website, (2) steganography embedding malicious code is displayed. Then, (3) the script embedded in the image transmits the information of the computer that has infiltrated the server of the attacker, judges whether the behavior of the malware is monitored by vulnerability of Internet Explorer (IE) of the web browser In addition, if it is in an attackable state, furthermore it is necessary to collect information by using the security hole of Adobe Flash Player, check whether it can send malware, (4) send malware to PC if the situation is well prepared. After that, it seems to be downloading spyware, Trojans, etc.
According to ESET researchers, furthermore, according to ESET researchers, the time it takes for malicious code embedded in the banner to be executed and malware to be sent using IE and Flash Player's vulnerability Is only 2 to 3 seconds, and a series of processes will be done without user's notice. It is said that the top priority measures that can be done by the user are not to use vulnerable IE or Flash Player.
Related Posts:
in Software, Web Service, Security, Posted by darkhorse_log