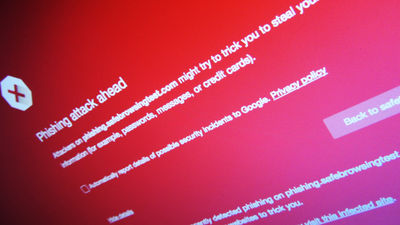
What is the attack group 'Tag Barnakle' that directs tens of millions of smartphones and PCs to fraudulent apps and harmful sites?

``By exploiting vulnerabilities in ad servers (
Tag Barnakle One Year Later: 120+ More Revive Adserver Hacks | by Eliya Stein | Apr, 2021 | Confiant
https://blog.confiant.com/tag-barnakle-one-year-later-120-more-revive-adserver-hacks-f3e5b3bc8e70
Millions of web surfers are being targeted by a single malvertising group | Ars Technica
https://arstechnica.com/information-technology/2021/04/malvertisers-use-120-hacked-ad-servers-to-target-millions-of-web-surfers/
The act of spreading malware through online advertisements or directing users to malicious websites is called `` Malvertising ''. Malvertising attackers typically pretend to be harmless ad buyers in ad serving systems and pay to serve harmful ads. In this case, the attacker needs to learn how the ad distribution system works and create ad buyers who are evaluated as 'harmless', which requires a lot of time and money.
However, Confiant's newly reported malvertising group 'Tag Barnakle' does not take the conventional method described above and is attacking without paying a single sentence for advertising expenses.
According to Confiant, Tag Barnakle attacks by hacking the open source ad distribution server `` Revive Adserver ''. Revive Adserver is a service for those who want to operate their own ad server without relying on a third party. According to Confiant, the number of ad servers compromised by Tag Barnakle is up to 60 as of August 2020 , and is expected to double to 120 by 2021.
Tag Barnakle uses vulnerabilities in Revive software to compromise servers and deface advertisements. At this time, Tag Barnakle used client-side fingerprinting to avoid detection and displayed malicious advertisements only to a small number of 'most attractive targets'.
The mechanism by which Tag Barnakle delivers malicious advertisements is as follows.
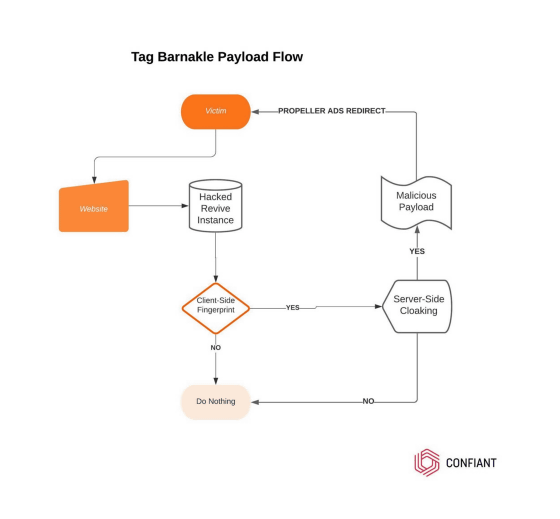
Tag Barnakle's method has not changed since it was reported in 2020, and it is targeting advertising companies that have not patched their servers. However, in the 2020 report, the target OS was the desktop OS, but in the past year it has changed to target mobile users as well.
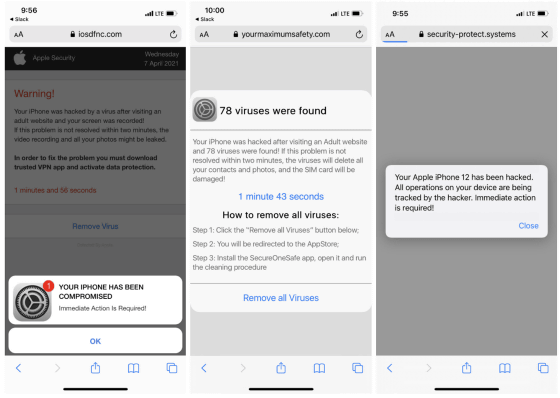
Below is an example of what is actually displayed. It indicates that the user's device is compromised and attempts to redirect to an unnamed security app.
It seems that some experts underestimate the fact that the number of damaged servers was 120, but these advertising companies use real-time bidding (RTB) and distribute advertisements to various advertising companies. increase. This has resulted in malicious ads being displayed in many places beyond the hacked servers. Confiant notes that 'it's nearly impossible to accurately calculate the number of malicious ads served by Tag Barnakle,' but conservatively estimates that 'tens of millions, if not hundreds of millions It climbs to the device.'
Related Posts:
in Security, Posted by darkhorse_log