What is "iBanking" which has a formidable mechanism and business model as malware for Android?

ByMarsmettnn Tallahassee
Even if 97% of companies take security measures, they are being invaded by malwareAs the survey results show, as evidenced by continued remodeling, the number of malware that has become increasingly aggressive with increasing attack power year by year, but the newly confirmed "IBanking"The malware having the mechanism which was hardly seen in the past has been made clear on the blog of" Symantec "famous for anti-virus software" Norton "series.
IBanking: Exploiting the Full Potential of Android Malware | Symantec Connect Community
http://www.symantec.com/connect/blogs/ibanking-exploiting-full-potential-android-malware
IBanking is a malware created by a person named GFF, unusual as this kind of softwareService type softwareIt has a business model of. A user (attacker) who uses this service either pays a fee of up to $ 5000 (about 500,000 yen) to the creator or pays a certain percentage from the illegally obtained "interest" to acquire a license It is supposed to be like that. It has a strange business model, but if you return the back, it will be astounding malware that you can only see the effect.
◆ How iBanking intrudes target
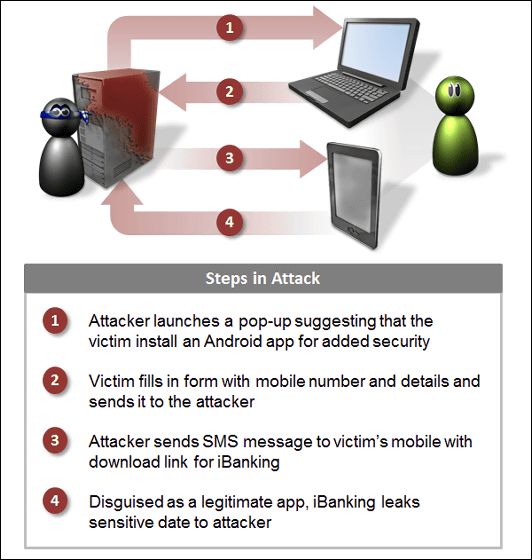
In many cases, an attacker uses a PC infected with a virus in advance to guide the targeted individual 's Android terminal to install iBanking.
1.When a target user opens a website of a financial institution such as a bank, it has already infiltrated the PCTroyA popup is displayed on the screen. The pop-up contains a message prompting you to install a mobile application to improve security.
2.A user who sees a popup transmits detailed information such as a telephone number to the server of the attacker according to the instruction,
3.From the server that received the contents, send SMS message describing the installation method of iBanking to the terminal with the listed phone number. Users install with illusion as official application by financial institution.
Four.From the terminal on which iBanking is installed, a lot of personal information etc. are transmitted to the server of the attacker.
IBanking installed on the terminal has been found to perform the following operations.
· Retrieve the phone number of the terminal, ICCID (SIM card ID), IMEI, IMSI, model name, OS name
Intercepted SMS messages are sent and sent to the server
· Intercept calls and send to the server in real time
Forwarding calls to phone numbers specified by the attacker
· Send the information stored in the phone book to the server
· Record ambient sound using a microphone and send it to the server
· Send SMS message
· Acquisition of GPS information
· Access to file system
· Access to program list
· If you have administrator privileges, prevent malware detection
· If you have administrator authority, reset the terminal to factory default
· Obfuscated program code
◆ How iBanking is misused
It is believed that iBanking is most utilizedNeverquestIt is a cyber criminal group called. NeverquestTrojan.SnifulaIt is a group that creates thousands of victims using malware that has undergone original remodeling to the international financial institutions etc.Man-in-the-middle attackIt is believed that iBanking has been introduced as a means to reinforce MITM attacks. I am hacking by looking at the one-time password that is issued mainly in the case of Internet banking, but since many of the telephone numbers being used are used in Western Europe, Neverquest is also west It is considered to be active mainly in Europe.
◆ Measures
Symantec, which is detecting iBanking activity, already has this threatAndroid.iBankingIt is detecting as. Many users who are infected with this malware often have PCs infected with Trojan as a preliminary step, so it is possible to prevent infection by iBanking by preventing infection with PC anti-virus software is.
In order not to suffer the damage, keep the virus definition file up to date, as well as pay attention to messages that contain links to suspicious software installation files (APK) in the text, It is necessary to put in the corner of the head that there are cases where APK with distribution is distributed in a reliable marketplace.
Related Posts:
in Note, Software, Smartphone, Posted by darkhorse_log