Vulnerability `` Simjacker '' that can take over iPhone and Android that has been abused for over 2 years is discovered

Security company
Simjacker – Next Generation Spying Over Mobile | Mobile Security News | AdaptiveMobile
https://www.adaptivemobile.com/blog/simjacker-next-generation-spying-over-mobile
Simjacker attack exploited in the wild to track users for at least two years | ZDNet
https://www.zdnet.com/article/new-simjacker-attack-exploited-in-the-wild-to-track-users-for-at-least-two-years/
Hackers are exploiting a platform-agnostic flaw to track mobile phone locations | Ars Technica
https://arstechnica.com/information-technology/2019/09/hackers-are-exploiting-a-platform-agnostic-flaw-to-track-mobile-phone-locations/
AdaptiveMobile Security is now found vulnerabilities 'Simjacker' is, as its name suggests SIM card by the attack that has passed through the, that can take over the smartphone exploits is. According to ZDNet , an IT information media for enterprises, although its existence was suggested at least in 2011, it was not widely known, so it was left untreated.
A series of attacks on Simjacker begins with an attack message called “Simjacker Attack Message” sent via SMS (Short Message Service) .
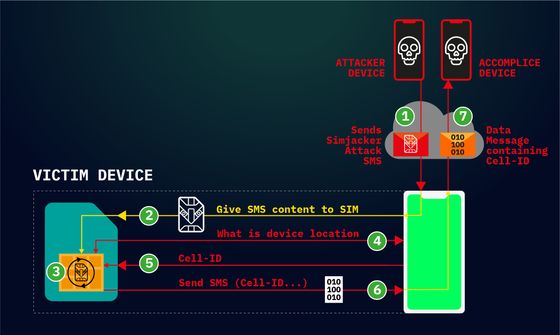
When the attacked device receives a “Simjacker Attack Message”, it is the device identification number through the vulnerability of the application “SIMalliance Toolbox Browser (commonly known as S @ T Browser)” preinstalled in the SIM card. Information such as
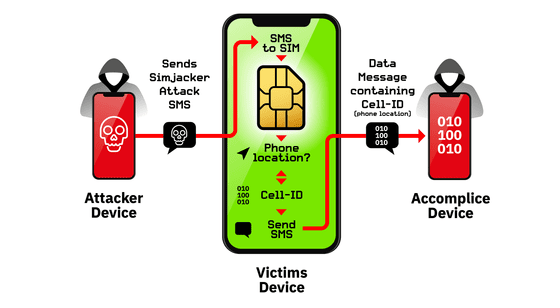
By using the same technique, various attacks are possible, such as making a phone call from a target device to an arbitrary phone number, sending a text message, or installing malware. Also, since the first attack message and the message sent by the attack do not leave any history in the SMS inbox or transmission box, it is extremely difficult for the target person to notice the attack.
S @ T Browser is old software that has not been updated since 2009, and many of its functions have been replaced by other technologies, but it has been used in the background. Simjacker is a vulnerability that depends on the type of SIM card, but since the OS and manufacturer of the device are not chosen, attacks are repeated in over 30 countries mainly in the Middle East, North Africa, Asia, and Eastern Europe It has been said.
Already, attacks on not only Apple, Google, Samsung, ZTE, Motorola, Huawei smartphones but also IoT devices equipped with SIM cards have been confirmed, and reports of cases where 300 terminals were attacked at once per day It has been. Many of these attacks are single shots, but in some cases they have been repeatedly attacked for several months.
AdaptiveMobile Security says, “We are confident that Simjacker was developed by a private company that monitors the individual with the will of the government.”
In a similar case, a case in which an Israeli software development company NSO Group created a spy software `` Pegasus '' for government agencies was used to track activists using the vulnerability of the chat application `` WhatsApp '' .
A vulnerability that can take over a smartphone with a single phone call to the chat application WhatsApp is discovered, and an example of spyware installed-GIGAZINE

There are also reports that Huawei engineers were involved in government espionage in two African countries using Pegasus similar software.
Reports that Huawei engineers were participating in government spy activities in two African countries-GIGAZINE

AdaptiveMobile Security has already reported this issue to the mobile operator industry group “ GSM Association ” and also shared information with “ SIMalliance ”, which has developed the specifications for S @ T Browser technology. The company is cooperating in updating the security guidelines.
However, since creating advanced Simjacker requires advanced and extensive knowledge, AdaptiveMobile Security has already stated that there are entities that can make a huge investment in the back of Simjacker developers. He expressed his view that there is a high risk of developing attack methods.
In the future, AdaptiveMobile Security will propose this issue at the international virus countermeasure conference ' Virus Bulletin International Conference 2019 ' to be held from October 2, 2019, and will work on countermeasures against Simjacker.
Related Posts:
in Smartphone, Security, Posted by log1l_ks