Microsoft and Citizen Lab reveal the actual situation about Israeli company 'QuaDream' that develops spyware that hacks iPhone via iCloud calendar invitation

Microsoft and cybersecurity research institute Citizen Lab have discovered a commercial spyware called Reign (which Microsoft calls KingsPawn) created by an Israel-based company called
Sweet QuaDreams: A First Look at Spyware Vendor QuaDream's Exploits, Victims, and Customers - The Citizen Lab
https://citizenlab.ca/2023/04/spyware-vendor-quadream-exploits-victims-customers/
DEV-0196: QuaDream's “KingsPawn” malware used to target civil society in Europe, North America, the Middle East, and Southeast Asia - Microsoft Security Blog
https://www.microsoft.com/en-us/security/blog/2023/04/11/dev-0196-quadreams-kingspawn-malware-used-to-target-civil-society-in-europe-north- america-the-middle-east-and-southeast-asia/
Standing up for democratic values and protecting stability of cyberspace: Principles to limit the threats posed by cyber mercenaries - Microsoft On the Issues
https://blogs.microsoft.com/on-the-issues/2023/04/11/cyber-mercenaries-cybersecurity-tech-accord/
iPhones hacked via invisible calendar invites to drop QuaDream spyware
https://www.bleepingcomputer.com/news/security/iphones-hacked-via-invisible-calendar-invites-to-drop-quadream-spyware/
Experts warn of new spyware threat targeting journalists and political figures | Hacking |
https://www.theguardian.com/technology/2023/apr/11/canadian-security-experts-warn-over-spyware-threat-to-rival-pegasus-citizen-lab
QuaDream's commercial spyware 'Reign' exploited 'ENDOFDAYS', a zero-day vulnerability affecting iPhones with iOS 1.4 to iOS 14.4.2 installed from January 2021 to November 2021. , hacking the iPhone using 'iCloud calendar invitations that can't see past dates'. Specifically, the spyware operator hacks the target device by sending an iCloud calendar invitation to the device.
ENDOFDAYS is a zero-day vulnerability developed by QuaDream whereby when an iOS device receives an iCloud calendar invitation with a tampered timestamp, the event is automatically added to the user's calendar without any notification or prompt. By including malware in this, the iPhone can be hacked without the victim's operation.
Citizen Lab senior researcher Bill Marczak told TechCrunch , an overseas media outlet, ``Since this iCloud calendar invitation does not notify the device, the victim knows that he or she is being attacked. I can't,' he says.
The 'Reign function list' found by Citizen Lab's analysis is as follows.
・Call voice recording
- Microphone voice recording
- Take photos with the front or back camera of your device
・Theft or deletion of password information from
・It hijacks the Anisette framework and hooks the system call (gettimeofday) to generate an iCloud time-based one-time password login code for an arbitrary date. It was used to generate two-factor authentication codes valid for a future date, and was presumably used to facilitate the permanent exfiltration of user data directly from iCloud.
・Run queries on SQL databases
- Removal of traces that may have been left by zero-click exploits
・Track device location information
-Perform various file system operations, including searching for files that match specified characteristics
In addition, Reign seems to be designed to erase all traces by deleting its own file data after stealing information from the terminal and deleting all traffic from the victim's iPhone. However, there are also traces that can be traced to Reign, which researchers at Citizen Lab call the 'Ectoplasm Factor'. The name of the malware trace is derived from the Stardew Valley quest, and the details are 'hidden to track the malware'.
Citizen Lab reports that it has discovered QuaDream servers in multiple countries including Bulgaria, Czech Republic, Hungary, Ghana, Israel, Mexico, Romania, Singapore, United Arab Emirates, Uzbekistan and more.
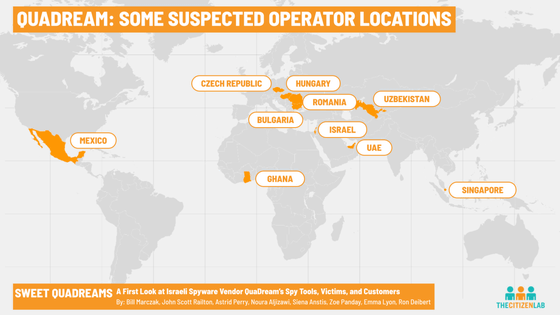
Citizen Lab researchers 'succeeded in identifying at least five victims of QuaDream spyware and exploits in North America, Central Asia, Southeast Asia, Europe and the Middle East.' , opposition parties, non-governmental organization (NGO) staff, etc. At this time, we cannot disclose the names of the victims.'
Spyware like Reign is used to monitor what the target is doing, and it seems that development costs can reach hundreds of millions of yen if it is supported by the state. Therefore, Citizen Lab said, ``Spyware like Reign would never conduct a cyberattack targeting the majority of iPhone users. We will continue our efforts,' he said, saying that spyware like Reign is unlikely to affect the general public.
QuaDream also uses a Cyprus-based company called InReach to sell commercial spyware, according to Citizen Lab. “QuaDream uses InReach to avoid Israeli regulators,” an anonymous person who has worked in the spyware industry told TechCrunch.

In addition, the source said, 'QuaDream's system is currently the most important system in Mexico,' and QuaDream's spyware is being used by the president of Mexico, nominally to 'keep quiet' the local government of Mexico City. I also revealed that it is used for '.
In addition, QuaDream ``recently closed its Android division and is now focused solely on iOS,'' TechCrunch reports.
QuaDream is a little-known spyware development company, but its name has been reported in the past for using the zero-click exploit 'FORCEDENTRY' used in the spyware ' Pegasus ' developed by the NSO Group .
A zero-click exploit for iPhone similar to spyware 'Pegasus' was also used by another Israeli company-GIGAZINE

In addition, Citizeb Labs said, ``Until the uncontrolled spread of commercial spyware is successfully curbed by systematic regulation by the government, spyware abuse may continue to increase.'' Until then, I fear that there will still be a lot of commercial spyware.
Apple spokesman Scott Radcliffe has said that since March 2021, when the update corresponding to ENDOFDAYS was released, ``there is no trace of the zero-day vulnerability being exploited.''
Related Posts:






