What is the method of phishing attacks that impersonate Apple or Google support to talk to targets and steal cryptocurrency and account information?

In recent years, with the advancement of technology, phishing scams have become more sophisticated. Brian Krebs, a former reporter for The Washington Post, has written a blog post explaining the methods and activities of the 'Crypto Chameleon' voice phishing group, which exploits legitimate services from Apple and Google to deceive targets through phone calls, emails, and system messages.
A Day in the Life of a Prolific Voice Phishing Crew – Krebs on Security
The voice phishing group '
Crypto Chameleon deceived its victims using phishing kits that closely mimicked the single sign-on pages of Okta and other authentication providers. Lookout also found that Crypto Chameleon used phishing kits operated and rented by a cybercrime group known as 'Perm' or 'Annie.' Perm is also believed to be the administrator of 'Star Fraud,' a large cybercrime community that operates on Telegram.
Until now, Crypto Chameleon had been operating in cooperation with Perm, a cybercriminal known as 'Aristotle' or 'Stotle,' but due to some reason, a rift occurred in the relationship between the two organizations, and Stotle subsequently betrayed Perm and revealed the nature of their activities and their methods to Lookout.
In Crypto Chameleon, each member has a role called 'Caller', 'Operator', 'Drainer' and 'Owner'. The specific roles are as follows.
・Caller: Calls the target and extracts information
・Operator: Operates the phishing tool and guides the target from page to page
Drainer: Logging into sites with leaked accounts and stealing targets' funds and information
Owner: The owner of the phishing tool, who listens in on fraudulent calls and sometimes participates in them
The reward for each member was a set fee per call or a certain percentage of the total amount of stolen funds. In addition, the administrator or rental company of the phishing tools received a certain percentage of the reward for each successful theft. According to Krebs, in the case of Perm, he received 10% of the amount stolen as a reward.
Below is a video posted by Stotle showing a real-life scam being perpetrated by Crypto Chameleon targeting musicians in California.
Voice phishers tricking a target into entering their password at a fake Apple website. - YouTube
Crypto Chameleon will first attempt to reset the target's Apple ID password, which will trigger a notification from Apple on the target device.
Next, Crypto Chameleon calls the victim using a spoofed Apple support number (800-275-2273) under the false name “Michael Keen.”
Target notified Michael Keen, who said he was a member of Apple's account recovery team, that there had been an unauthorized password reset attempt. In response, Michael Keen said, 'We will investigate,' and 'we will send a prompt to your device.'
Crypto Chameleon then calls Apple's support line using a spoofed phone number from the victim and displays an Apple account verification alert on all associated devices.
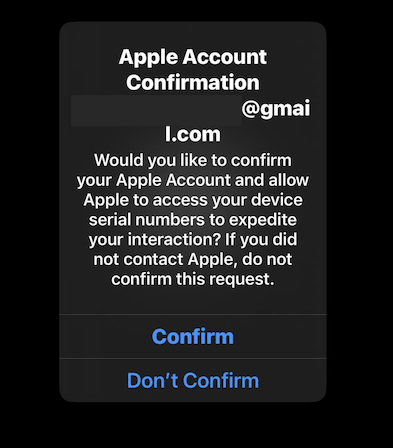
The victim receives a confirmation alert, believing they are actually speaking to Apple, and follows the instructions to change their account password in the device setup by Crypto Chameleon.
Once the Apple ID password has been changed, Crypto Chameleon takes the next step in closing the ticket by sending the victim a text message with a link to a website that mimics Apple’s iCloud login page, and if the victim enters their Apple ID password and passcode into the fake website, Crypto Chameleon will have access to the victim’s iCloud account information.
Crypto Chameleon then uses the victim's Apple ID account to steal information.
According to Stotle, the target list used by Crypto Chameleon includes information that includes user account data leaked from cryptocurrency hardware wallet vendor Trezor in 2022 and 2024. Crypto Chameleon collects and verifies personal information about targets called 'Autodoxers,' and narrows down targets using a tool that checks whether they have active accounts on cryptocurrency exchanges.
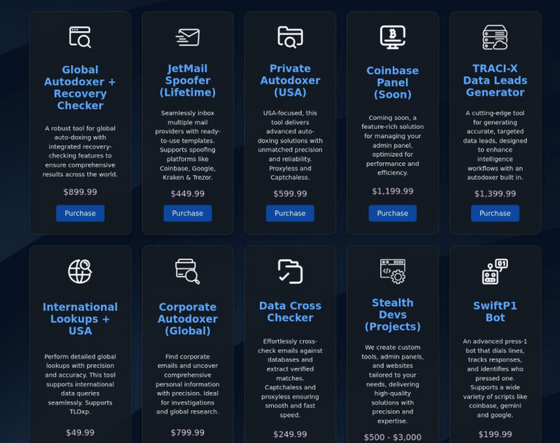
In fact, Stotle and his accomplices
In addition, Apple warns, 'Apple representatives will never ask you to provide or enter your password, device passcode, or two-factor authentication code on a web page. If you receive a message or phone call claiming to be from Apple, immediately discontinue contact or hang up.'
Recognize and take action against social engineering schemes, including phishing messages, fake support calls, and other scams - Apple Support (UK)
https://support.apple.com/ja-jp/102568
Related Posts: