'TunnelVision' attack method discovered that sends communications that were supposed to go through a VPN directly to the Internet

A new attack method has been discovered that sends traffic that was supposed to be sent via a VPN directly to the Internet, eliminating the benefits of using a VPN, such as encryption and concealing IP addresses. Security company Leviathan Security Group explains what this attack is.
CVE-2024-3661: TunnelVision - How Attackers Can Decloak Routing-Based VPNs For a Total VPN Leak — Leviathan Security Group - Penetration Testing, Security Assessment, Risk Advisory

TunnelVision - CVE-2024-3661 - Decloaking Full and Split Tunnel VPNs - Leviathan Security Group - YouTube
Novel attack against virtually all VPN apps neuters their entire purpose | Ars Technica
https://arstechnica.com/security/2024/05/novel-attack-against-virtually-all-vpn-apps-neuters-their-entire-purpose/
VPN is a technology that creates a private network over the Internet as if a dedicated line had been laid. By communicating via an encrypted VPN, data leakage or alteration can be prevented, and by accessing the Internet from the VPN destination, it is possible to communicate while hiding one's own IP address.

When you configure your PC to communicate via a VPN, packets sent by applications are sent to the VPN client via the routing table. The VPN client encrypts packets and sends them to the Internet, and also decrypts received packets and sends them back to the application.

The newly discovered vulnerability, 'TunnelVision,' can forcibly change the destination of packets that were supposed to be sent to a VPN by using a function called option 121 of the DHCP server, which automatically issues IP addresses to devices on the network.
Using DHCP option 121, a route with higher priority than the route set by the VPN can be set in the user's routing table, making it possible to send packets that would have gone through the VPN directly to the Internet. Also, since the VPN client itself is running, the PC will continue to display 'VPN connected.'
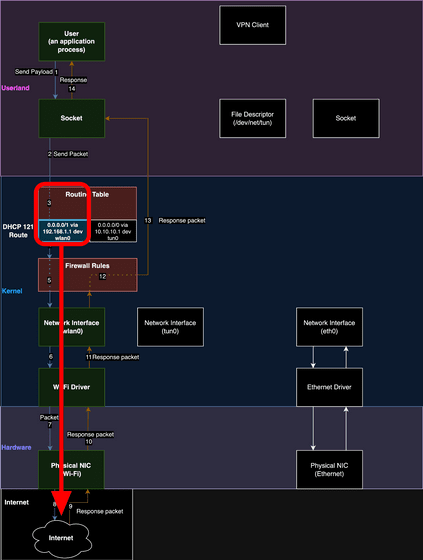
Even if the communication content itself is encrypted by the application, another benefit of VPNs, 'hiding the destination IP address and source IP address,' is lost, so there is a possibility of being subjected to targeted denial of service attacks that cut off communication with specific parties. In addition, it is said that administrative privileges for the DHCP server are required to run TunnelVision.
Android is not vulnerable to TunnelVision attacks because it does not implement option 121, but other operating systems do not have a complete solution. The most effective solution is to use a VPN in a virtual machine with a network adapter in router mode, or to use a VPN over a mobile device's Wi-Fi network.
Related Posts:
in Security, Posted by log1d_ts